ICMP works like the communication between the carpenter and the store. It relays messages from the receiver to the sender about the data that was supposed to arrive. ICMP protocol notifies the sender if the data is not received by the receiver or received in the wrong order. Thus, ICMP is a protocol for communicating information about data, but it does not manage the data itself.
What is ICMP in Computer Networks?
A network device uses the Internet Control Message Protocol (ICMP) to diagnose network communication problems. Information about whether data is reaching its desired destination on time is primarily determined by ICMP. Commonly, the ICMP protocol is used on network devices, such as routers. ICMP is essential for error reporting and testing and it can also be used in distributed denial-of-service attacks.
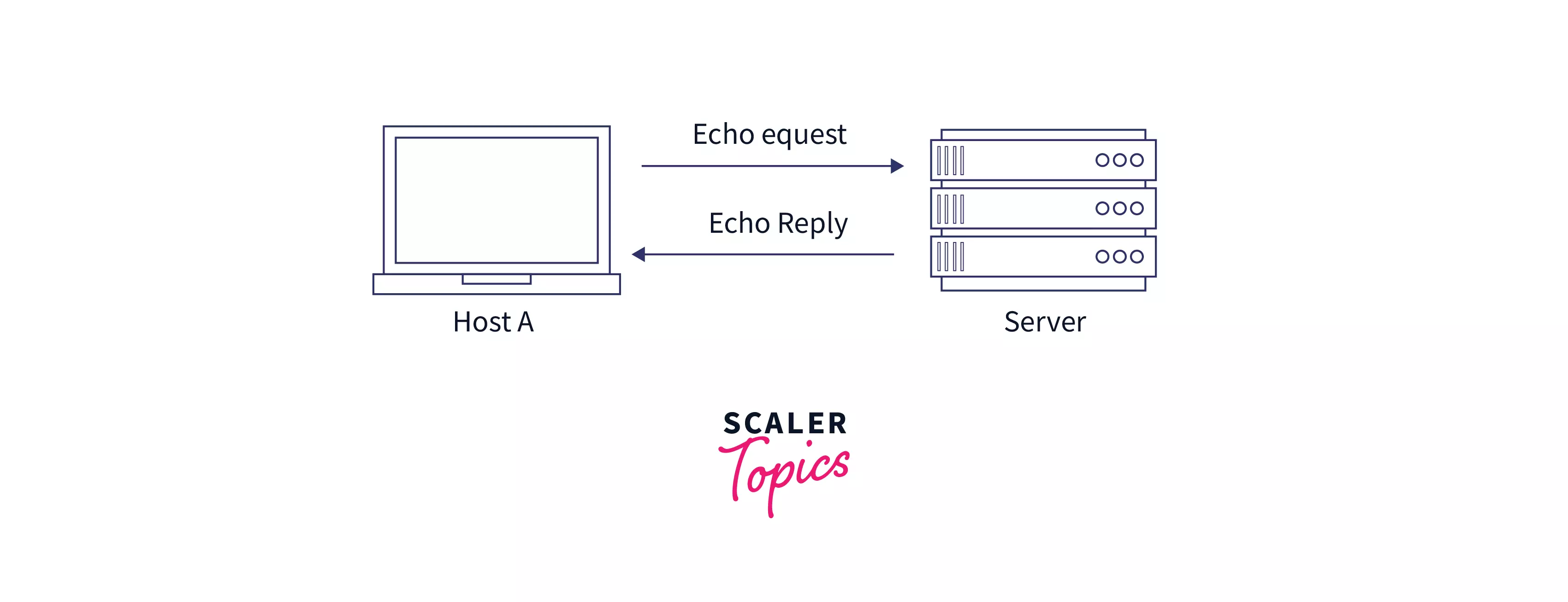
Ping messages refer to both the ICMP echo request and echo reply messages. A network device receives an ICMP echo request from the ping command and immediately sends back an ICMP echo reply.
Additionally, it lacks a level within the Open Systems Interconnection (OSI) model, which outlines the seven layers involved with network transmissions. When you understand ICMP, you will see why it is such a valuable tool, but it is also important to comprehend how ICMP can be used in DDoS attacks that may threaten an organization.
What is the Internet Control Message Protocol Used for?
- A network problem is diagnosed and reported using the Internet Control Message Protocol (ICMP). When data does not arrive as expected, ICMP sends a message from the sender to the receiver. Ping and traceroute use ICMP messages as part of the diagnostic process to provide information on how data is being transmitted.
- Some senders want to send a message to a destination, but the router is unable to do so. The router notifies the sender that I am unable to send the message to that destination.
- ICMP is also commonly used for network diagnostics. Both traceroute and ping use ICMP. Traceroute and ping are messages sent when data is successfully transmitted. The physical routers that handled the data are included.
- ICMP is also used to hurt network performance. ICMP floods, Smurf attacks, and ping of death attacks are used to overwhelm a device on the network and prevent it from functioning properly.
How Does ICMP in Computer Networks Work?
- In ICMP, no connection is formed. The message is simply sent. In addition, unlike TCP and UDP, which specify the ports to which information is sent, ICMP does not specify a specific port to which information will be received.
- When the network disables the delivery of packets to the destination device, it generates and sends error messages to the sender device. Error messages include time exceeded, parameter problem, destination unreachable, network congestion, etc.
- An IP(Internet Protocol) datagram is sent from one device to another through multiple routers and intermediaries when it is sent from one device to. There can be an error in forwarding that IPV4 datagram. Hence, ICMP messages are divided into two broad categories :
- Error messages
- Query messages
ICMP Message Format
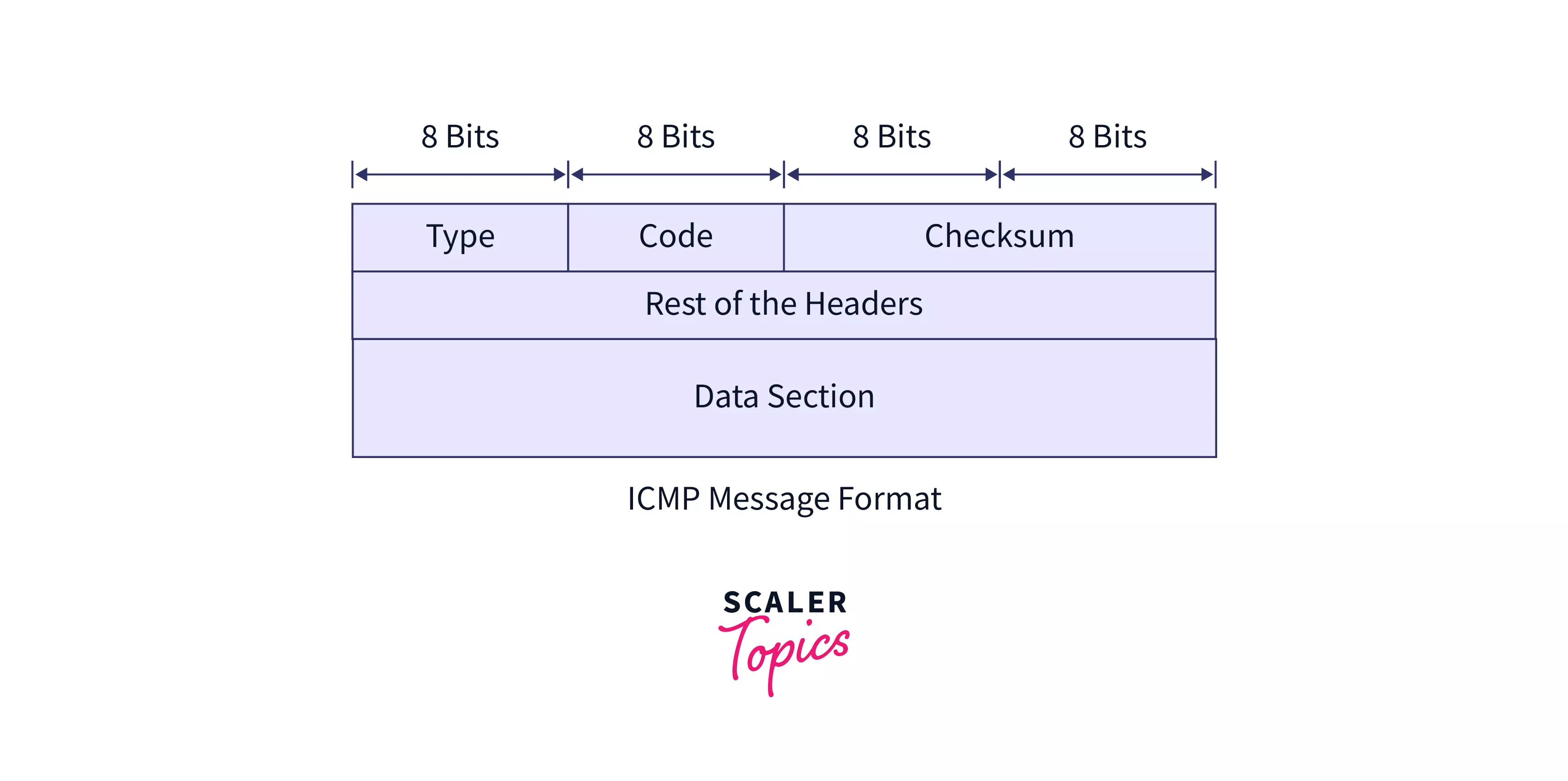
So far, we’ve learned about two different forms of ICMP messages.
Let’s look at the format of ICMP messages presently. The following is the format of the lower ICMP message:
Although the ICMP header differs for each message type, the first three fields are the same in all messages. These three fields take up a total of 4 bytes.
These fields are described in great detail :
- Type:
This specifies the field message type. This field, for example, is used to establish the code associated with any form of an error report. Similarly, if there is a query message, this field will appear in the code for that query. - Code:
For error messages, this defines a subtype of field error. For example, if a destination unreachable error occurs, the code field indicates what type of destination the error is. Examples: Network unreachable (code 0), host unreachable (code 1), protocol unreachable (code 2), etc. The code also defines the subtypes of these errors. - Checksum:
Checksums are calculated from the headers and data used to detect errors.
In IP datagrams, ICMP messages are included. The remaining IP headers can be seen in the ICMP message header section. - Data:
In the context of error messages, the package contains the complete information for the package in this section.
Types of ICMP Error Reporting Messages
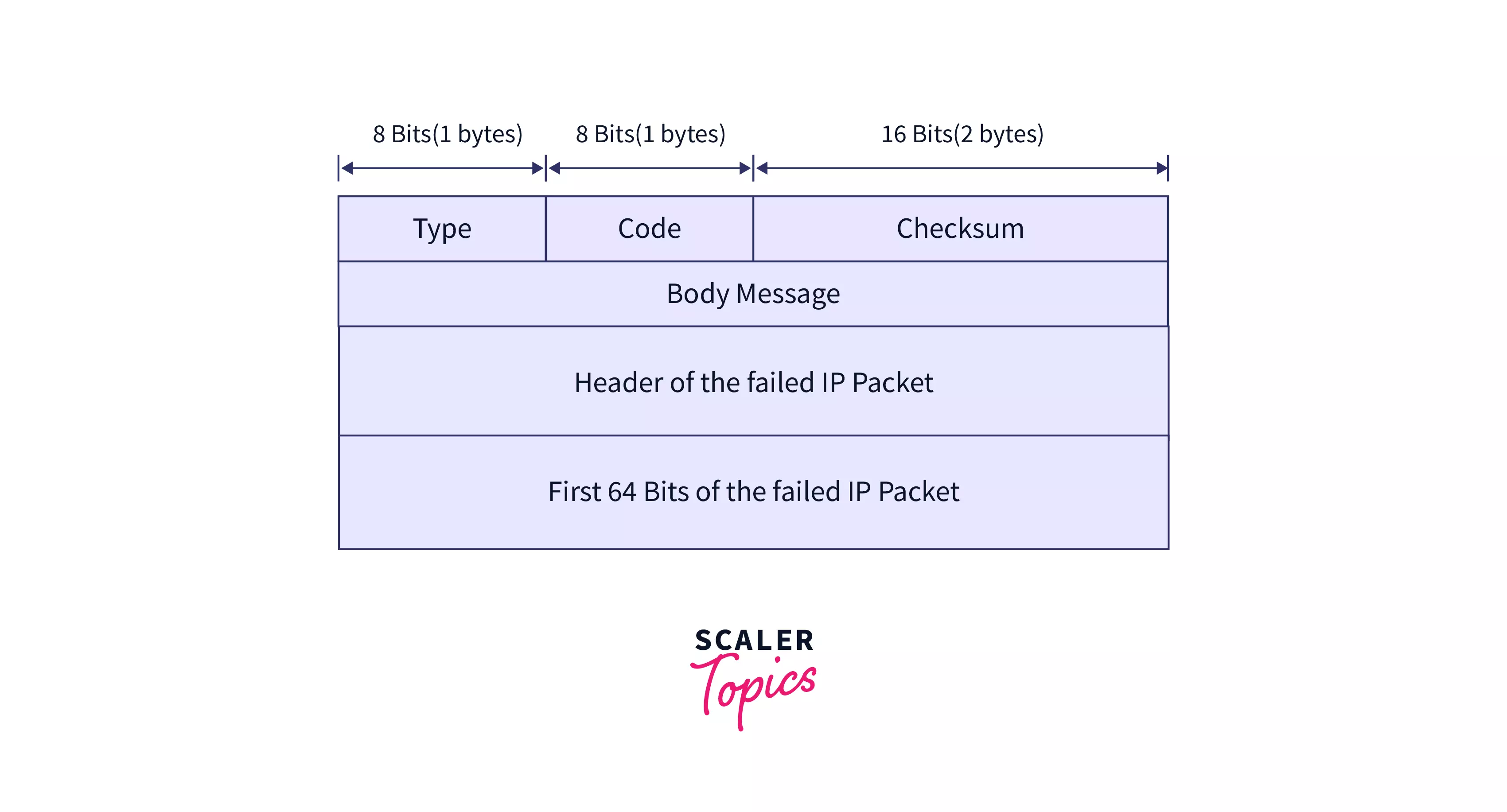
An error message is sent by a router/host when it encounters a problem while processing IP packets. A datagram containing only the source and destination IP addresses is always sent to the source.
The Types of Error Messages are:
- Message “Unable to reach destination”: Hosts and routers send this message when IP packets cannot be routed to their destination. An intermediary router can discard a datagram and send an unreachable message to sender A if recipient B does not receive it.
- Source quench message: When the network is congested or when the source is sending packets faster than the router can handle, the host or router will send this message.
When Sender A sends a data packet at a high data rate that the router cannot handle, Sender A discards the packet and sends a source quench message instructing A to send the packet at a lower rate. To do. The packet is either stopped from being sent or slowed down after A receives the message.
- Timeout message: The host/router sends this message if the datagram lifetime value is reduced to zero or if the destination address does not receive all packets at the specified time interval. For example, after a packet is sent from the 1000-unit layer to the 200-unit layer, the packet is split into five fragments. If all fragments do not reach the destination within the specified time, all fragments are discarded and a timeout message is sent to the source.
- Parameter problem message: The host/router sends this message if the datagram parameters are not set correctly. Used to indicate an error in the datagram header field.
- Redirect message: The host/router sends this message to update the host’s routing table. For example, sender A wants to send a message to recipient B, and there is a router between them. A then sends the data to the router, which sends the message to B and the redirect message to A, allowing A to update the routing table.
ICMP in DDoS Attacks
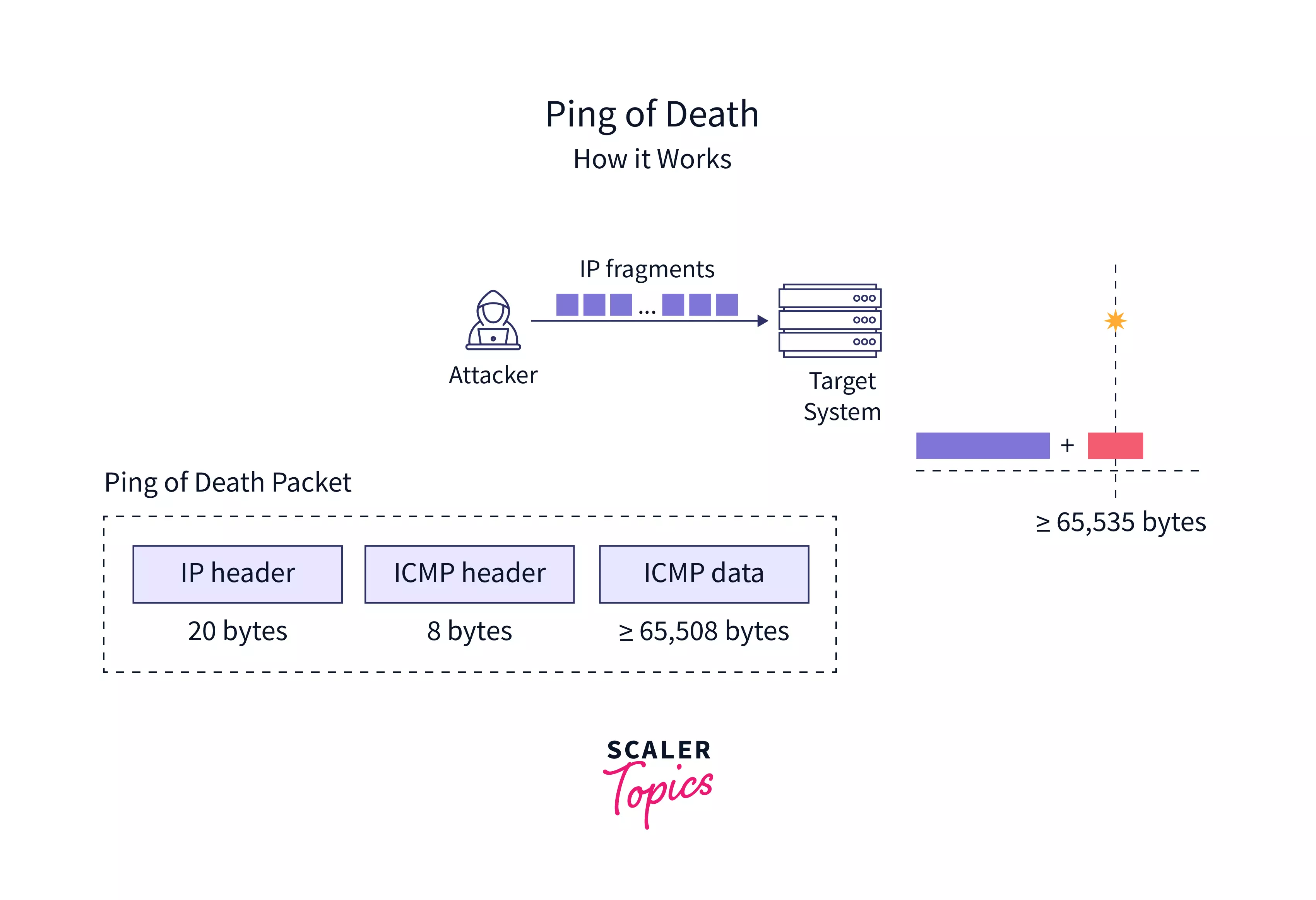
ICMP Flood Internet Control Message Protocol (DDoS) attacks, also known as ping flood attacks, are common denial of service (DoS) attacks in which an attacker attempts to use ICMP to echo a target device. ICMP echo request and echo response messages are typically used to ping network devices to diagnose device health and connectivity, and the connection between the sender and the device. Flooding the destination with request packets forces the network to respond with the same number of response packets. This makes the destination inaccessible to normal traffic.
The DDoS format for ping (ICMP) floods can be Divided into two Repeating Steps.
- The attacker sends many ICMP echo request packets to the target server through multiple devices.
- The target server then sends an ICMP echo-response packet to the IP address of each requesting device.
Conclusion
- ICMP will give you a little feedback about communication when something goes wrong. It is used to exchange information about the state of the Internet from one host to another, not to transfer data.
- The state that triggers an ICMP packet is mainly due to the result found in the IP header of the failed packet.
- ICMP does not exist in data transmission packets. ICMP is primarily used by network administrators to improve the internet connection of diagnostic utilities.
- This article defines what ICMP is, gives you a technical overview of ICMP, and also describes error messages and the tools you can use with ICMP.
- ICMP will continue to be a powerful tool for network administrators to diagnose network issues and other related issues.