Virtual Router Redundancy Protocol (VRRP) or VRRP protocol for IPv6 can be configured for Ethernet, Fast Ethernet, Gigabit Ethernet, 10-Gigabit Ethernet, and logical interfaces. VRRP protocol allows hosts on a LAN to utilize redundant routing platforms on that LAN with only the static configuration of a single default route on the hosts being necessary. The default route set on the hosts’ hosts is assigned a shared IP address by the VRRP routing platforms. Each VRRP routing platform has a primary (active) platform that is always in use, and backups for the other platforms.
Introduction
To construct a virtual gateway, one can utilize the VRRP (Virtual Router Redundancy Protocol), which is quite similar to the HSRP (Hot Standby Routing Protocol).
A standard protocol established by the IETF in RFC 3768, VRRP protocol is extremely similar to HSRP; if you are familiar with HSRP, you will have no trouble understanding VRRP. There are a few variations, but overall, the configuration is essentially the same.
An appropriate standard defines VRRP as a fault-tolerant protocol. The route selection feature of VRRP supports numerous gateways and enables logical devices to function independently of physical devices.
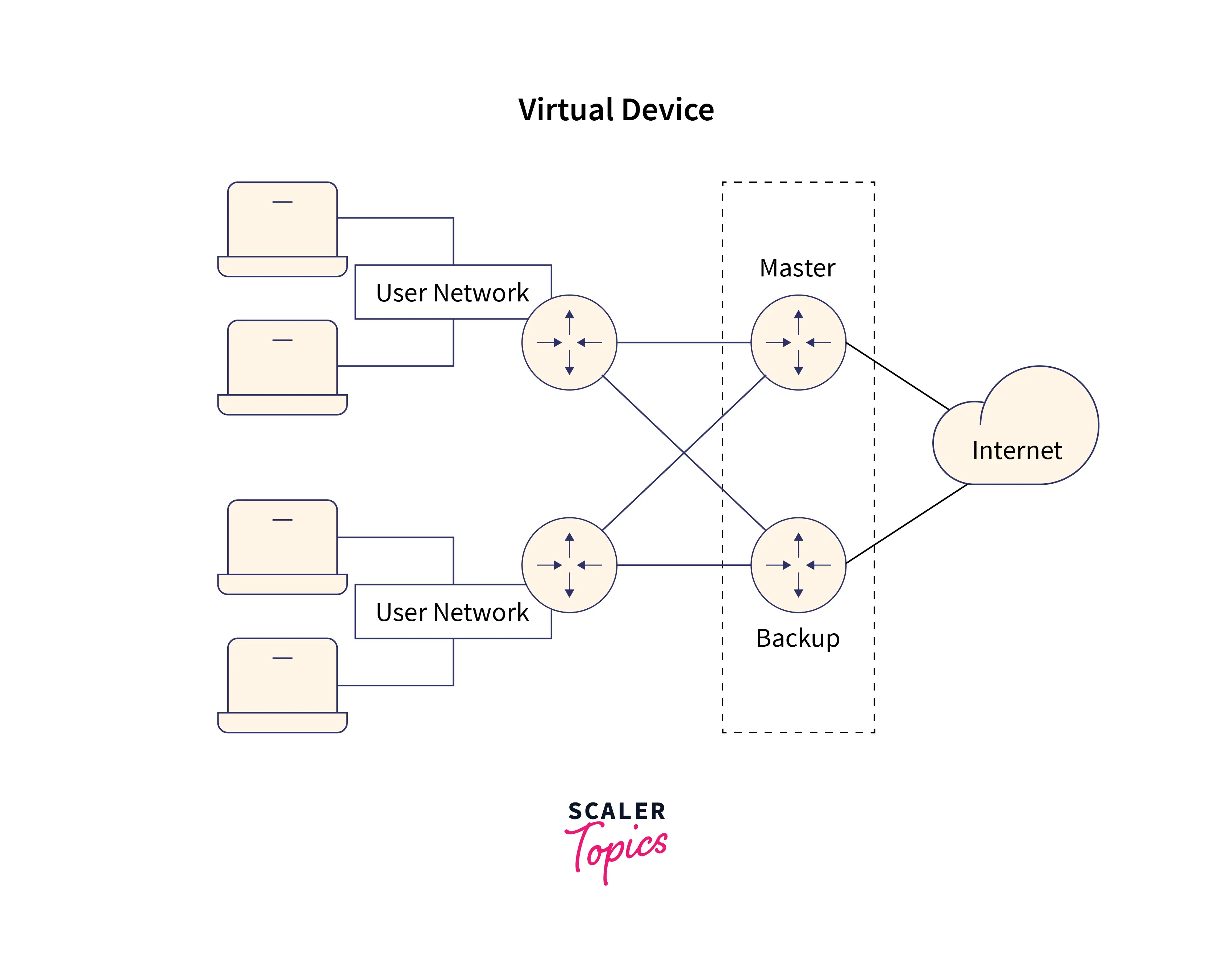
VRRP is activated on two routers in the network. The master is the first, while the backup is the second. The two routers work together to create a virtual router, which has both a virtual MAC address and a virtual IP address. Only the presence of the virtual router is observed by hosts. Through the virtual router, the hosts talk to hardware connected to different network segments.
A logical VRRP gateway is used by VRRP on multicast or broadcast LANs (such as Ethernet) to guarantee the dependability of crucial links. VRRP offers high reliability by preventing service interruptions if a physical VRRP gateway fails. Routing protocol configurations, for example, do not need to be changed for VRRP configuration to take effect.
A backup device can quickly replace a malfunctioning default device using VRRP. With the least amount of VRRP transmission and without contacting the hosts, this is accomplished. On administration interfaces, Virtual Router Redundancy Protocol is not supported.
VRRP-enabled devices elect their primary and backup devices on a dynamic basis. Priorities from 1 to 255 can also be used to force the assignment of primary and backup devices, with 255 being the highest priority. The default primary device in VRRP operation periodically transmits advertising to backup devices. The 1-second default interval is used. The backup device with the next highest priority becomes the primary and starts forwarding packets if a backup device is idle for a predetermined amount of time without receiving an advertisement.
History
Although Cisco asserts that Hot Standby Router Protocol, a similar protocol with essentially the same facility, is patented and licensed. Robert Barr of Cisco stated in 2001 that they would not assert any patent claims unless someone tried to assert a claim against Cisco. VRRP is described in the open-standard Internet Engineering Task Force (IETF) publication RFC 5798, but Cisco claims that Hot Standby Router Protocol, a similar protocol with essentially the same facility, is patented and licensed. On the IETF website, IBM also claims that its software covers patents.
The VRRP, on the other hand, was created and developed by IEFT in 1999 as a non-propriety protocol. It is claimed that a variety of systems can use this protocol. Additionally, it sports a 3-second hold timer in addition to a 1-second faster timer for its default hello. Additionally, it has been noted that the standby speaker in the VRRP protocol is unable to deliver hellos, in contrast to the HSRP protocol.
In the case of VRRP, a backup router fills in for the master router in case the latter is unable to perform its duties. Despite one type of Cisco model being able to use it, this redundancy protocol is primarily utilized for routers that are not Cisco-based, like Juniper.
Configuration of VRRP
Customizing VRRP
It’s not necessary to modify VRRP’s behavior. It’s important to know that a VRRP group is active as soon as you enable it. Before you have finished customizing the functionality, the router might take over the management of the group and become the virtual router master if you enable a VRRP group first before customizing VRRP. So it makes sense to tweak VRRP before activating it if you intend to do so.
- Steps In Summary
- enable
- set up the terminal
- the number of the interface
- Ip address and Ip-address mask
- the text of the vrrp group description
- vrrp group priority level
- vrrp group preempt [minimum seconds of delay]
- The [sec] interval is advertised by the vrrp group timers
- learn about vrrp group timings
- exit
Enabling VRRP
- SUMMARY OF VRRP STEPS
- enable
- set up the terminal
- the number of the interface
- Ip address and Ip-address mask
- IP address of the vrrp group (secondary)
- end
- show vrrp [brief] | group]
- display the vrrp interface type number [short]
Configuring VRRP Object Tracking
Steps In Summary
- enable
- set up the terminal
- line-protocol | IP routing track object-number interface type number
- the number for the interface
- vrrp group IP IP-address
- vrrp group priority level
- object-number vrrp group [decrement priority]
- end
- Display Track [Object-Num]
Configuring VRRP Text Authentication
Before You Start The RFC 2338 technique may have been implemented by vendors, however interoperability with those vendors is not permitted.
For a VRRP group at any one time, text authentication cannot be paired with MD5 authentication. When MD5 authentication is set up, the text authentication field in VRRP greeting messages is set to all zeros on transmit and ignored on receive—provided the receiving router has also enabled MD5 authentication.
STEPS IN SUMMARY
- enable
- set up the terminal
- the number of the terminal interface type
- secondary IP address IP-address mask
- text-string for vrrp group authentication
- the IP address of the vrrp group
- repetition of Steps 1 through 6 on each communicating router
- end
Using VRRP as an Example
Router A and Router B each belong to three VRRP groups in the scenario that follows.
The following attributes apply to each group in the configuration:
- Group 1:
- Virtual IP address is 10.1.0.10.
- The group’s master router, with priority 120, will be Router A.
- A 3-second commercial break.
- Preemption has been enabled.
- Group 5:
- Router B will take over as the group’s master, with priority 200.
- 30 seconds are allotted for each advertisement.
- Preemption is enabled.
- Group 100:
- Since Router A has a higher IP address, it will take over as the group’s master first (10.1.0.2).
- The standard advertisement interval is one second.
- Preemption is not enabled.
Legacy Configuration
This technique can be used to configure VRRP V2.
Define the group and virtual IP address in interface configuration mode:
vrrp IP
There are further possible configurations that can be added, but this is all the configuration needed to get VRRP operating.
Between 0 and 255 can be used to designate a priority. Use the command vrrp group-number> priority> to specify the priority. The master router is given the highest priority. Since preemption is turned on by default, changes are nearly quickly reflected.
The command vrrp group-number> authentication can be used to add authentication. An MD5 hash of the password can be used in place of sending a plain text password over the network. Use the following keywords: text, text-password, md5 keychain, keychain name, and key string.
Hierarchical VRRP Configuration
Different settings for VRRP are used in IOS XE.
To enable VRRPv3 on the router, start by using the command fhrp version vrrp v3 while in global configuration mode.
The VRRP instance is then defined in interface configuration mode with the command VRRP group-id> address family. You can use either IPv4 or IPv6 for this.
With the command vrrpv2, it is possible to modify it now if just VRRPv2 is to be used.
The command address ip-address> can be used to define the gateway virtual IP address.
The command priority priority-value> can be used to configure the group’s priority as an alternative.
Synchronise the Configurations
This process demonstrates how to load balance from primary to secondary or from primary to secondary while using VRRP to synchronize settings.
- On Primary, choose Administration > File Management, then click View on the CONFIG field.
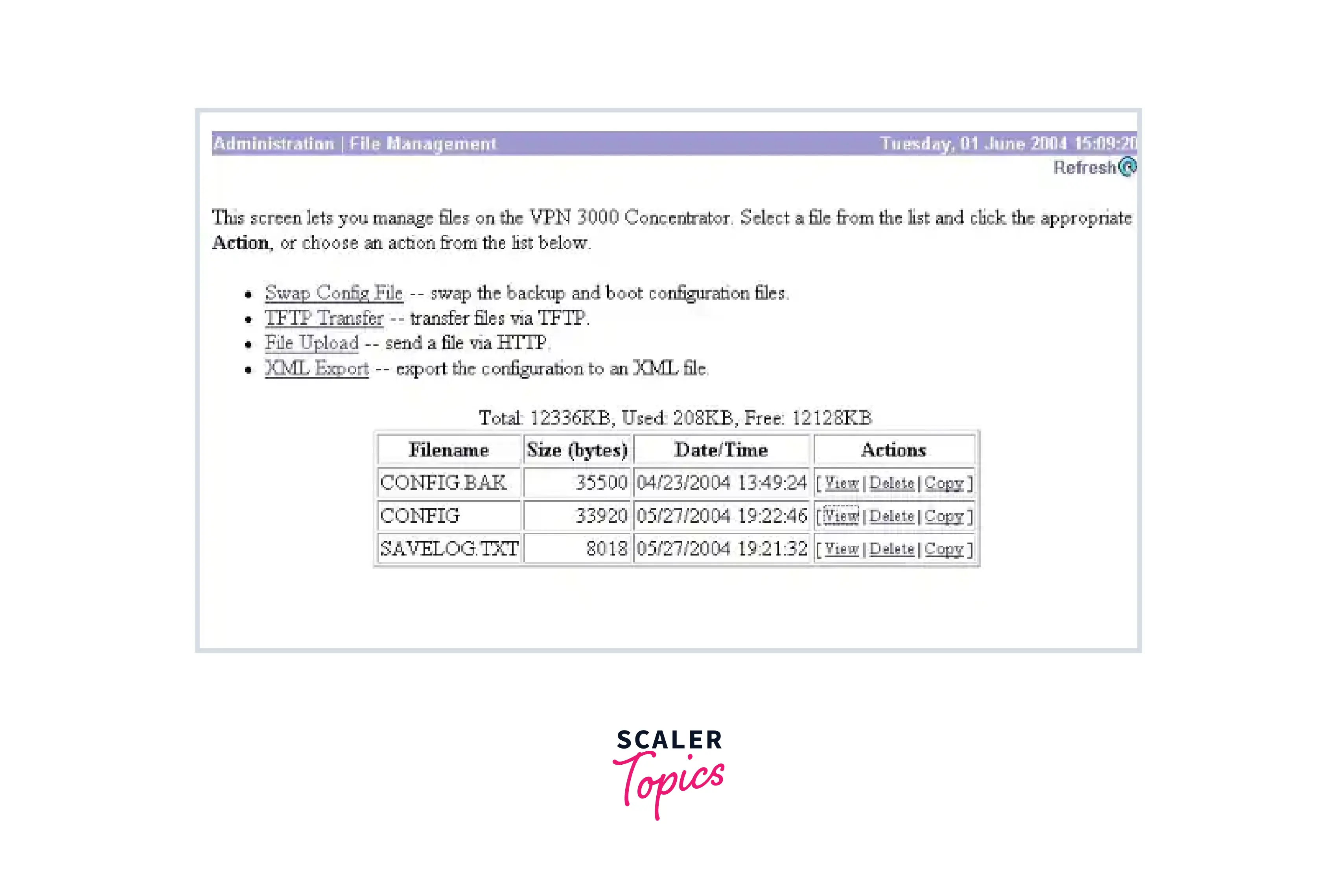
- The setting will appear when the web browser starts; select it and copy it (ctrl-a, ctrl-c).
- Enter WordPad with the configuration pasted in.
- In the Find What area, choose Edit > Replace, then type Primary’s public interface IP address. The IP address you intend to assign to the secondary or backup should be entered in the Replace With area.
- If you have an external interface configured, do the same for that as well as the private IP.
- Your choice of name should be used to save the file. But make sure to save it as a “text document” (for example, synconfig.txt).
- The default extension of “.doc” prevents you from later changing it. The VPN Concentrator only accepts text, thus the format saving is the cause.
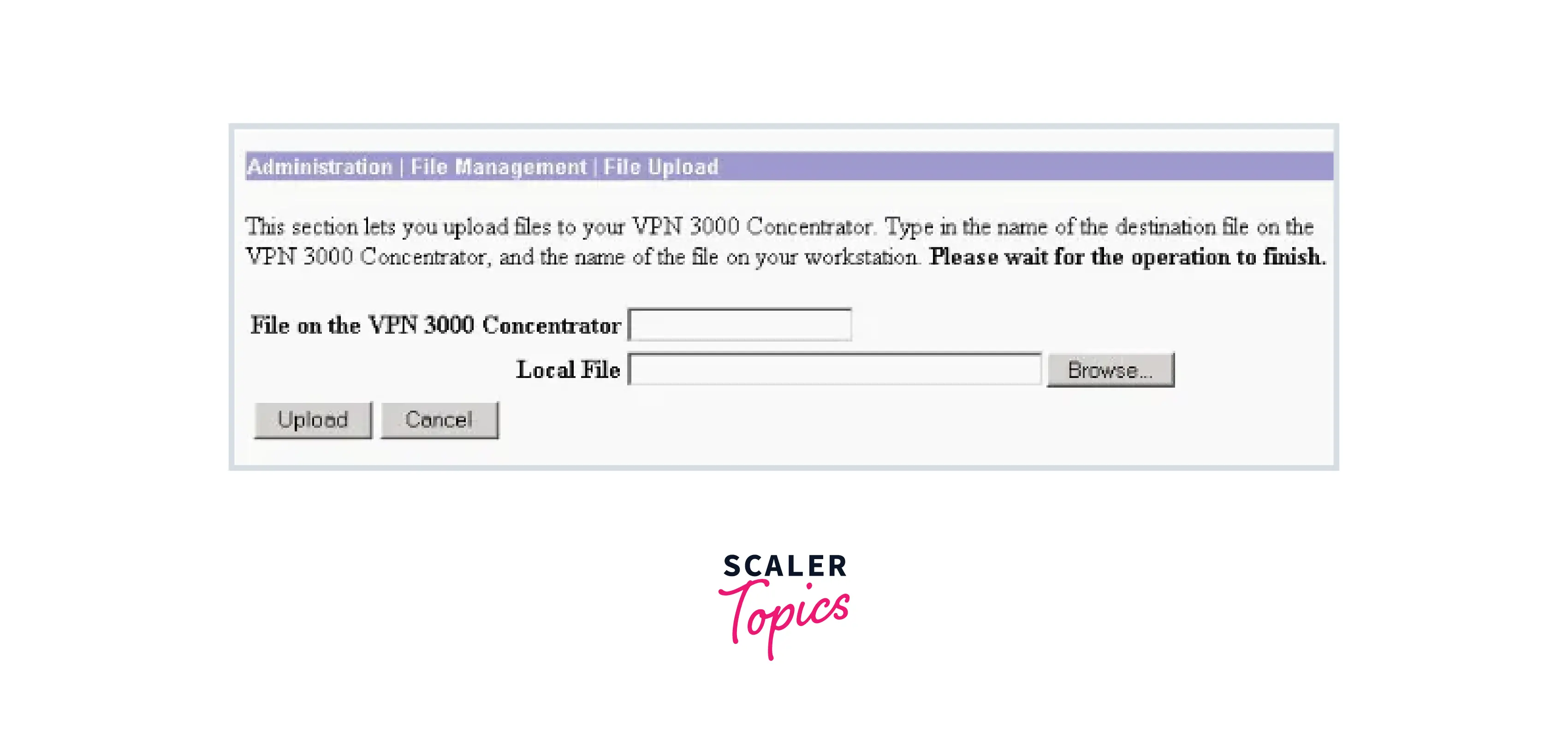
- In the File on the VPN 3000 Concentrator section, type config.bak and then navigate to the stored file on your computer (synconfig.txt). Next, select Upload.
- It is uploaded by the VPN Concentrator, which also converts the synconfig.txt file to config.bak automatically.
- To force the VPN Concentrator to start with the uploaded configuration file, choose Administration > File Management > Swap Configuration Files and press OK.
- Continue with the default settings in the System Reboot box after being forwarded there and click Apply.
Except for the addresses you previously modified, it has the identical configuration as the Primary when it first starts up.
The parameters in the Load Balancing or Redundancy (VRRP) window need to be changed, therefore remember to do so. Select Redundancy under Configuration > System > IP Routing.
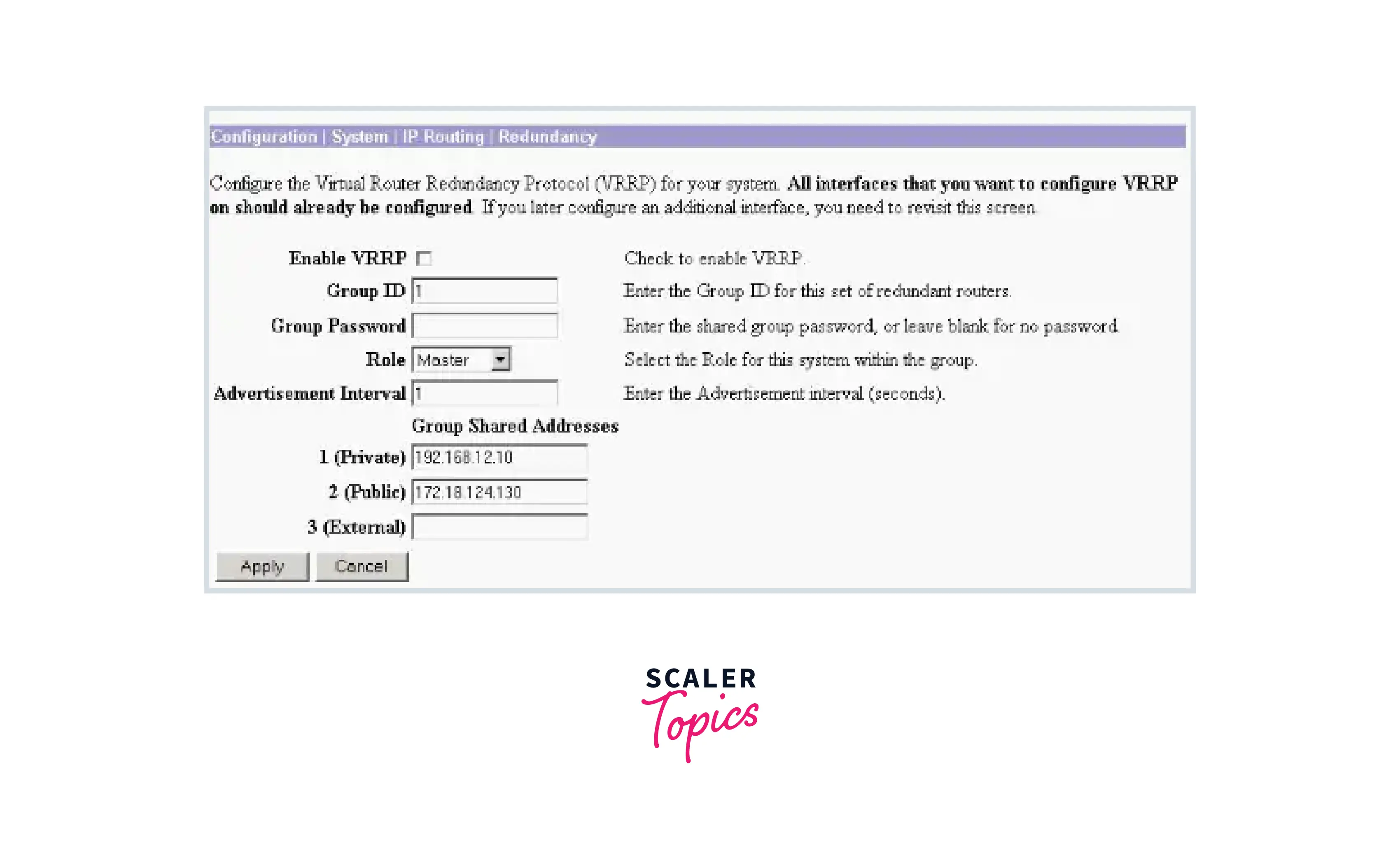
How Does the VPN 3000 Concentrator Implement VRRP?
SEP load balancing and concentrator redundancy are also features of the VPN 3000 family of concentrators. The ability to support up to 4 SEP modules is available in models 3015 and higher. Two of these modules can be used to obtain the highest throughput, while the other two can act as backup SEPs in the event of a primary SEP failing. SEP redundancy is a top-down function, with the bottom SEP taking over when the top SEP fails. In such cases, sessions automatically go to the bottom SEP while still being connected. The other top SEP module takes over SEP processing if both the top and bottom SEP modules fail.
If no more redundant modules remain, the concentrator’s software will manage the sessions. Users must re-connect in each of these cases because sessions are lost. It is not necessary to configure SEP redundancy because it is automatic.
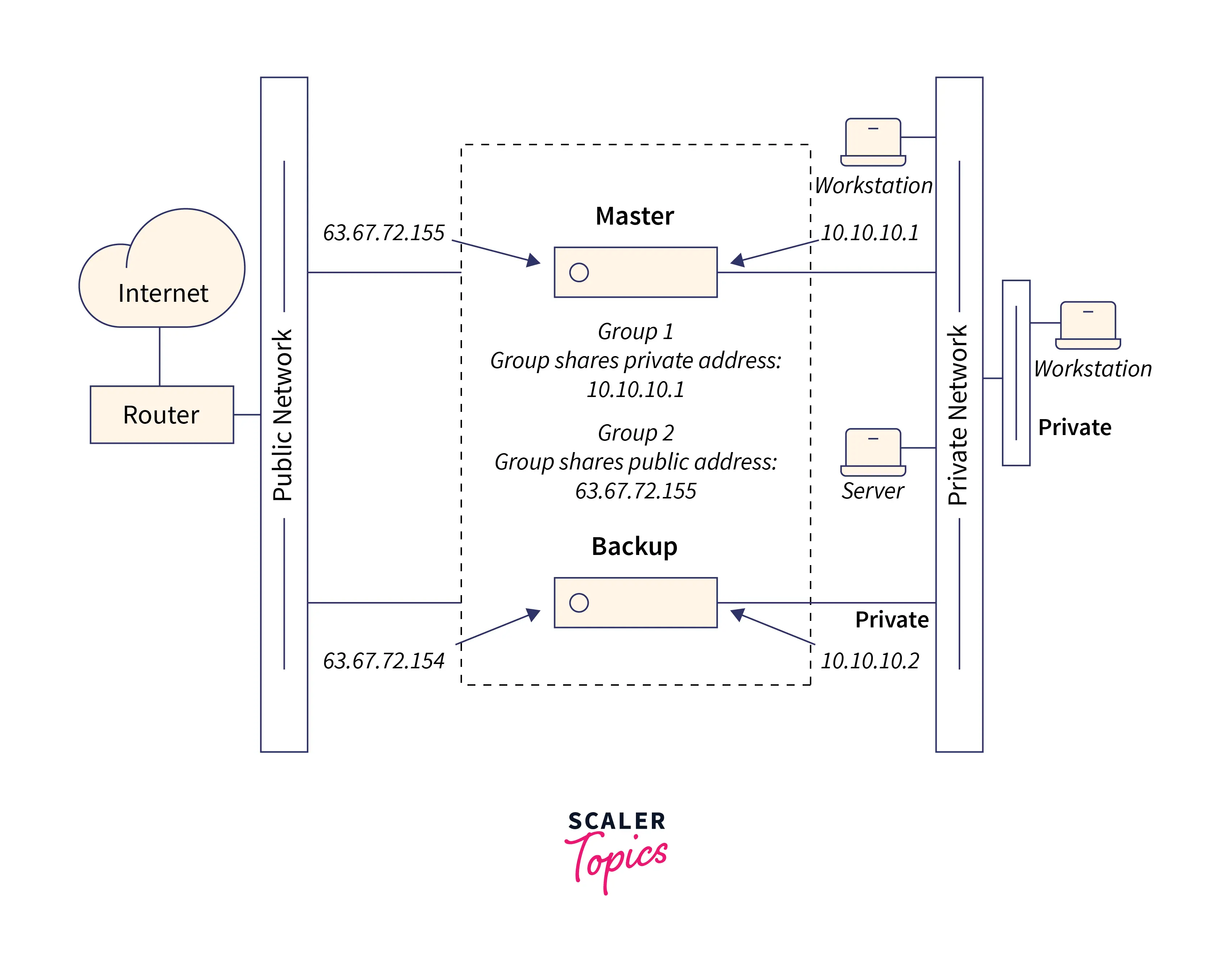
When several concentrators are working simultaneously at the same location, concentrator redundancy is affected. All parallel concentrators’ private interfaces must be located in the same LAN, while the public interfaces must be located in separate LANs from the private interface’s LAN, for this fault tolerance to function properly.
Through the use of a technology called Virtual Router Redundancy Protocol, the VPN 3000 Concentrators can tolerate faults (VRRP). With this protocol, all VPN services are routed through the concentrators’ virtual router. The VRRP group, whose master concentrator is responsible for maintaining requests to the IP address of the virtual router, has one concentrator. The other concentrators stop getting VRRP hellos on both interfaces if the master fails. When this happens, an idle backup concentrator becomes the master and keeps routing requests to the IP address of the virtual router for the next three to ten seconds.
The far-end devices must rejoin after remote access sessions are terminated. It is not necessary to rejoin after the switchover occurs for LAN-to-LAN (site-to-site) tunnels.
Typically, IKE X-Auth is used for per-user SA authentication granularity in remote access VPN tunnels. A Phase 1 SA must be provisionally authenticated before attempting Internet Key Exchange (IKE) X-Auth in “Phase 1.5” to use IKE X-Auth successfully. For the temporary authentication of the Phase 1 SA, the IPsec group password is utilized.
Groups of redundant VPN concentrators are recognized.
- The group is given a single Primary.
- The group’s Primary VPN Concentrator may have one or more backups.
- The Backup devices receive status updates from the Primary device.
- VRRP tries each Backup in order of precedence if the Primary is unable to communicate its status. The Primary function is taken over by the responding Backup.
- Recall that VRRP only permits redundancy for tunnel connections. As a result, the backup only listens to tunnel protocols and traffic in the event of a VRRP failover. The VPN Concentrator cannot be pinged. The configurations of participating VPN Concentrators must be the same. The interface addresses of the Primary Primary must match the virtual addresses specified for VRRP.
Redundancy is only possible with VRRP for tunnel connections. As a result, the backup only listens to tunnel protocols and traffic in the event of a VRRP failover. The VPN Concentrator cannot be pinged. The configurations of participating VPN Concentrators must be the same. The interface addresses of the Primary’s Primary must match the virtual addresses specified for VRRP.
How to Implement VRRP on Cisco IOS XR Software?
The following tasks are covered in this section’s instructions:
- Customizing VRRP
- Enabling VRRP
- Verifying VRRP
- Clearing VRRP Statistics
Customizing VRRP
It’s not necessary to modify VRRP’s behavior. It’s important to know that a VRRP group is active as soon as you enable it. If you enable a VRRP group first and then customize VRRP, the router may take over the management of the group and become the master virtual router before you’ve completed tweaking the function. So it makes sense to tweak VRRP before activating it if you intend to do so.
You can modify your VRRP setup by using the parts that follow.
OVERVIEW STEPS
- configure
- vrrp router
- interface type interface-path-id
- text-authentication with vrrp and vrid
- vrid assume-ownership disable
- priority vrrp
- vrid preempt [delay seconds] [disable]
- vrrp vrid timer [msec] interval
- vrrp vrid track interface type instance interface-path-id [priority-decrement]
- vrrp delay [minimum seconds] [ reload seconds]
- execute one of these commands:
- end
- commit
Activating VRRP
To enable VRRP on an interface, use the vrrp ipv4 command as detailed in the sections that follow.
STEPS IN SUMMARY
- configure
- router with vrrp
- interface-path-id as the interface type
- ipv4 IP-address [secondary] vrrp vrid
- execute one of the following instructions:
- end
- commit
Verifying VRRP
To view a quick or in-depth status of one or all VRRP virtual routers, use the show vrrp command.
STEPS IN A NUMBERED SUMMARY
- display vrrp [interface type instance interface-path-id [vrid]] [short | detailed | all statistics]]
VRRP Statistics Removal
To remove all software counters for the selected virtual router, use the clear vrrp statistics command.
- Clear vrrp statistics [interfacetype interface-path-id [vrid]]
BFD for VRRP
A network protocol called BFD for VRRP Bidirectional Forwarding Detection (BFD) is used to find errors when two forwarding engines are communicating with one another. One of the two modes, asynchronous mode or demand mode, is available for BFD sessions to operate in. The two endpoints exchange hello packets regularly in asynchronous mode. The session is deemed down if some of those packets are not obtained. The exchange of hello packets is not required in demand mode; either host may send a hello message if necessary. Asynchronous BFD mode is supported by Cisco.
- BFD’s positive aspects
- Setting Up the BFD Process
HSRVP vs. VRRP
A CISCO-exclusive protocol called Hot Standby Router Protocol (HSRP) offers redundancy in a network. Only one router is operational at a time, with the others in standby mode. If the active router fails, the standby router will be in charge of traffic forwarding.
The Virtual Router Redundancy Protocol (VRRP) is an open standard protocol that offers redundancy in a network. A network layer protocol is called VRRP. It employs the idea of a master router and backup router, whereby, in the event of a master router failure, one of the backup routers will assume control of the master router’s duties and be in charge of traffic forwarding until the master router is restored.
Similarities –
- Virtual IP address: Both protocols make use of the idea of a virtual IP address, in which the default gateway for hosts connected to a network or subnetwork is one of the IP addresses in the subnetwork or network itself.
- Preempt: Preempt is a situation in which the chosen (active in the case of HSRP and master in the case of VRRP) router reassumes control of the task of forwarding traffic from the other (standby in the case of HSRP and backup in the case of VRRP) routers when it becomes active once more. There is a concept of preempting in both protocols.
- Monitoring the monitored objects, such as the condition of the line protocol, is done by object tracking, a process. The procedure checks on the tracked object regularly, and if any changes are detected, the priority of backup or standby routers is raised, making one of these routers the active or master router.
- Priority: In HSRP and VRRP, the router with the highest priority will take over as the active or master router. One router will serve as the head (active router in HSRP, master router in VRRP), with the rest acting as backups (standby router in HSRP, backup router in VRRP). Look at some of the differences between HSRP and VRRP now.
| HSRP | VRRP |
|---|---|
| A Cisco-only protocol is HSRP. | An open standard protocol is called VRRP. |
| An application layer protocol is HSRP. | A network layer protocol is VRRP. |
| Multicast address 224.0.0.18 and protocol number 112 are used by VRRP. | Version 2 of HSRP utilizes UDP port 1985 and 224.0.0.102 as the multicast address, while HSRP version 1 uses UDP port 1985 and 224.0.0.2 as the multicast address. |
| Preempt must be manually enabled. | In VRRP, preempt is activated by default. |
| In HSRP, the hello message and dead times are 3 and 10 seconds, respectively. | VRRP uses the concepts of Master advertisement interval (1 second by default) and Master down interval in place of the hello timer and dead timer (3.069 by default). |
| The HSRP MAC address is 0000.00 07.ac0a. Where the hexadecimal representation of 0a (here group number assumed 10) is the HSRP group number. | VRRP uses the MAC address 0000.5e00.01xx. In this case, xx stands for the VRRP group number. |
| Version 1’s allowable group number range is 0-255, while Version 2’s range is 0-4095. | range permitted is 0-255 |
Benefits of VRRP
The following are some advantages of VRRP:
- Redundancy—Allows you to designate more than one router as the default gateway router, reducing the likelihood of a network having a single point of failure.
- Load sharing—Allows multiple routers to share traffic to and from LAN clients. The available routers receive a more equitable distribution of the traffic load.
- Multiple VRRP groups—If the platform supports numerous MAC addresses, then it supports multiple VRRP groups on a router’s physical interface. You can achieve redundancy and load sharing in your LAN architecture by using multiple VRRP groups.
- Preemption – This function enables you to replace a backup router that has replaced a failed primary with a higher priority backup router that has become available.
- Manage various IP addresses, including secondary IP addresses, thanks to the availability of additional IP addresses.
You can set up VRRP on each subnet if you have several subnets defined on an Ethernet interface. - The advertisement protocol uses a specific multicast address (224.0.0.18) assigned by the Internet Assigned Numbers Authority (IANA) for VRRP advertisements. This addressing method enables testing equipment to precisely identify VRRP packets on a segment while reducing the number of routers required to support the multicasts. VRRP’s IP protocol number is 112, according to IANA.
- By changing VRRP priorities based on interface conditions, VRRP monitoring makes sure that the best VRRP router is the group’s primary router.
- In most cases, an Active-Passive (Primary-Backup) setup is used with VRRP. However, it can also be set up for an Active-Active setup with load balancing.
- As an IETF Open Standard Protocol, VRRP allows for the inclusion of devices from various vendors and across several categories.
- If necessary, the primary gateway device may have several backup devices.
- Tackling failover issues in the router rather than at the network periphery.
- Preventing the necessity of changing the settings of the end nodes if a gateway router fails.
- Removing the requirement for protocols for router discovery to facilitate failover functioning.
- Reliable transmission is provided by a logical VRRP gateway on a multicast or broadcast local area network (LAN), such as an Ethernet network. In the case that a link to a physical VRRP gateway fails, VRRP helps avoid service outages.
- Applications that are flexible: An IP packet is encapsulated with a VRRP header. With this implementation, VRRP can be connected to several upper-layer protocols.
Conclusion
- Static configuration issues can be resolved using the Virtual Router Redundancy Protocol (VRRP) functionality. A transparent failover at the first-hop IP router is made possible by the IP routing redundancy protocol known as VRRP. Several routers can unite as a single virtual router thanks to VRRP.
- It is not required to modify VRRP’s functionality. Remember that a VRRP group is active the moment you enable it. The router might take over control of the group and turn become the master virtual router if you enable a VRRP group before configuring VRRP. This could happen even if you haven’t finished customizing the feature.
- VRRP is intended for use across Ethernet LANs with multiaccess, multicast, or broadcast capabilities. VRRP is not meant to take the role of current dynamic protocols. In addition to being supported by VRF-aware MPLS VPNs, Gigabit Ethernet, Fast Ethernet, Bridge Group Virtual Interface (BVI), and Ethernet interfaces, VRRP is also supported by MPLS Virtual Private Networks (VPNs) and VRF-aware MPLS VPNs.
- Simple, rapid, and easy VRRP configuration is provided by the simplified method. More consideration must be given to configuration details when using legacy VRRP. While the Legacy VRRP configuration technique provides total control over all functions, the Simplified VRRP configuration option does not offer one or two features (specifically preempt mode configuration).
- By establishing a secure connection over a TCP/IP network (such as the Internet), which users perceive as a private connection, the VPN 3000 Concentrator (also known as the VPN Concentrator) provides a virtual private network.
- You must be a member of a user group linked to a task group with the appropriate task IDs. The task IDs needed for each command are listed in the command reference guides. Contact your AAA administrator for help if you think a user group assignment is preventing you from utilizing a command.