The optimum route between the source and destination networks is found during the routing process by a layer 3 device (either a router or a layer 3 switch). Dynamic routing protocols are used to reduce administrator workload, i.e., administrators need to set up less, however by default, all routing information is exposed to all interested parties since it is not encrypted, making it vulnerable to an attack. By adding authentication to the interface over which we are advertising the routes, such as by the creation of a key chain, we may secure routing protocols like RIP, EIGRP, and OSPF.
Scope
- This article describes adding Security to Routing Protocols.
- We will also learn about
Routing Information Protocol (RIP). - We will also learn about the
Enhanced Interior Gateway Routing Protocol (EIGRP). - We will also learn about
Open Shortest Path First (OSPF). - We will also learn about different BGP Communities.
Introduction
Ad hoc networks are constructed by nodes working together without the use of any infrastructure. Nodes do not have a comprehensive understanding of the network topology. They need to identify reliable routes that nodes may use to forward packets from source to destination to deliver packets. Nodes must broadcast their presence, listen for other nodes’ announcements, forward route discovery requests and reply packets, maintain and update their routing tables, and communicate their routing information as part of the route discovery operation.
Ad hoc routing techniques are already challenging due to the nodes’ mobility and poor wireless connectivity, but security presents an additional difficulty.
Ad-hoc networks, which lack a central routing device (router), are wireless networks that spontaneously form between specific devices (computers, sensors, mobile phones, and others) and have constrained resources (battery, memory, processing power). Each node is responsible for ensuring this function. Additionally, when needed, the network structure changes dynamically. These features lead the routing protocols designed for ad-hoc networks to pose several security concerns. Ad-hoc On-Demand Distance Vector Routing (AODV) and OLSR (Optimized Link State Routing Protocol) are the two primary protocols examined in this research. Additionally, we’ll examine how our modifications affect how well the aforementioned processes function. The network simulator for OPNET Modeler will be used to do the analysis.
Routing Information Protocol (RIP)
A distance-vector routing protocol is called Routing Information Protocol (RIP). When using the distance-vector protocol, routers update their neighbors with all or a portion of their routing tables using routing-update messages.
The hosts can be set up to function as a member of a RIP network using RIP. When your network changes or network connectivity fails, this sort of routing automatically reconfigures routing tables with minimum maintenance required. The System product now supports RIPv2 so that you may send and receive RIP packets to update routes throughout your network.
In the next image, a static route is introduced to the central system (AS1) that defines the connection to network 10.1.1.x through AS2. With route redistribution set to true, this is a static route that was introduced by your network administrator. By using this configuration, other routers and systems will be able to share this route and send traffic to your main System I platform when it comes to 10.1.1.x (AS1). To transmit and receive RIP data, AS2 has configured its routed system. The information that AS2 has a direct connection to 10.1.2.x is being sent by AS1 in this case.
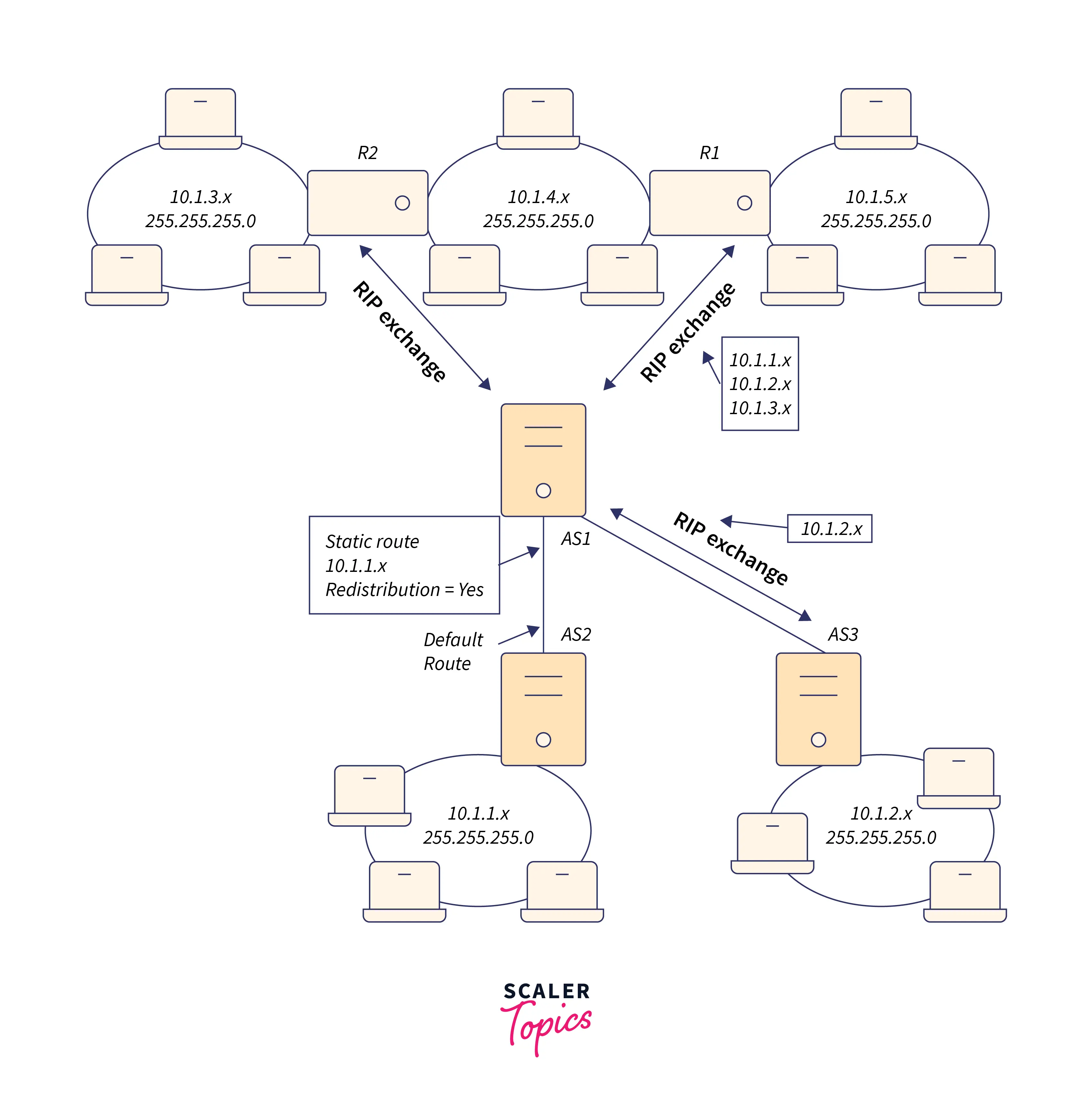
The traffic routing seen in the previous graphic is explained by the following procedure.
- This RIP packet is obtained from AS2 and processed by AS1. It will save this route if AS1 does not already have a route to
10.1.2.x. - This new route data will be ignored if it already knows a shorter or equal-hop route to
10.1.2.x. In this instance, AS1 saves the route information. - Information about the path to 10.1.5.x is sent to AS1 by R1. This route data is retained by AS1.
- R2 provides information to AS1 that includes the path to
10.1.3.x. This route data is retained by AS1. - When AS1 sends RIP messages to R1 in the future, R1 will get information describing all the connections that AS1 is aware of but that R1 may not be aware of. 10.1.1.x, 10.1.2.x, and 10.1.3.x route data is transmitted by AS1. Because AS1 is aware that R1 is linked to 10.1.4.x and does not require a route, AS1 does not provide R1 information about 10.1.4.x. Both AS3 and R2 receive similar information.
Hop Count
The number of routers between the source and destination networks is referred to as the hop count. The routing table includes the path that has the fewest hops since it is seen to be the optimal way to connect to a network. By restricting the number of hops permitted between a source and a destination, RIP avoids routing loops. A hop count of 16 is regarded as being outside the reach of the network and is over the maximum permitted for the RIP of 15.
How does the RIP work?
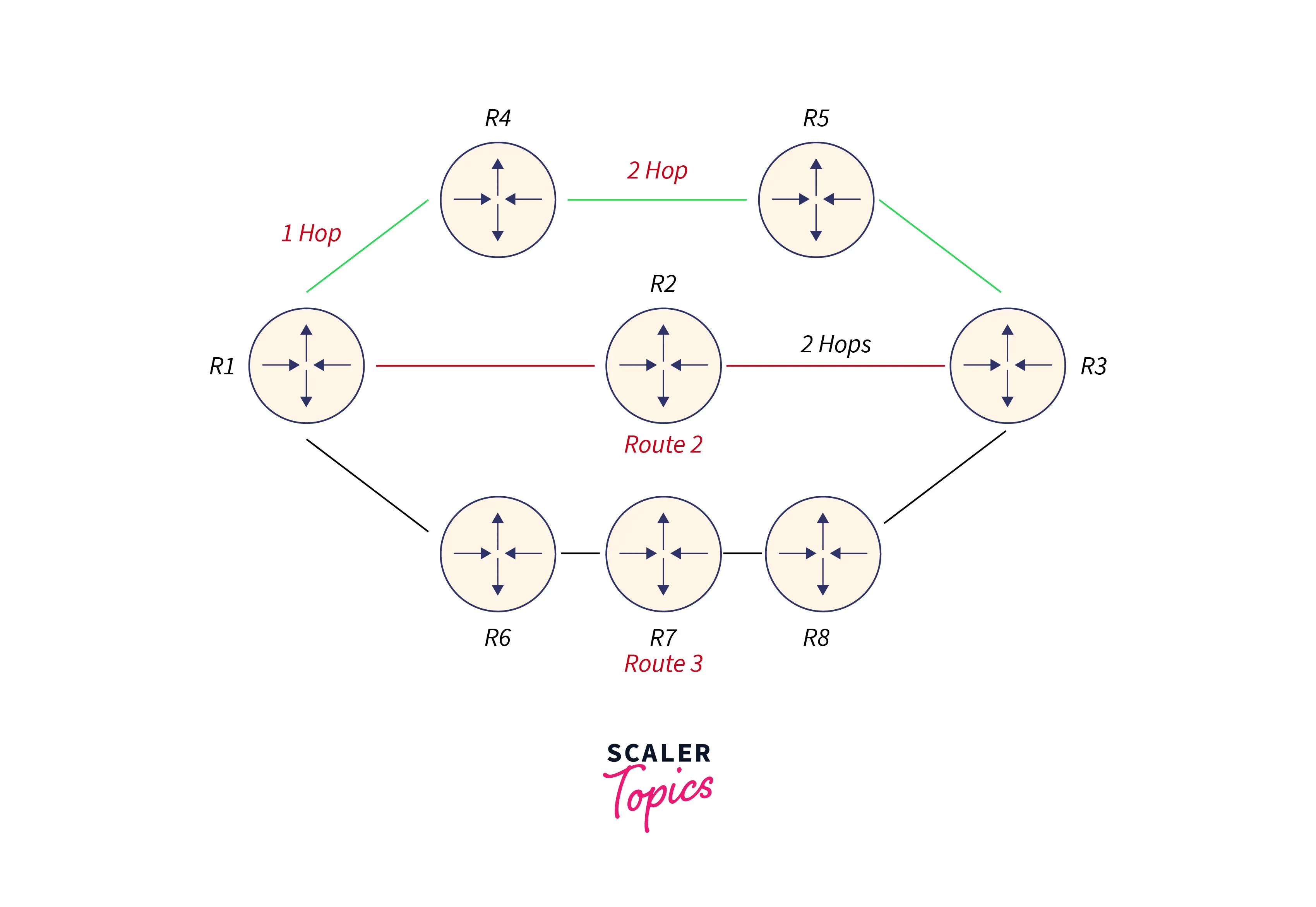
In a network with eight routers, if Router 1 wishes to transfer data to Router 3, Router 3 must first be configured. The route with the fewest hops will be selected if the network is set up with RIP. The aforementioned network contains three routes, namely Routes 1, 2, and 3. Route 2 will be chosen by a RIP because it has the fewest hops—2, as opposed to Route 1’s three and Route 3’s four hops.
Benefits of RIP
The benefits of a RIP protocol are as follows:
- It is simple to set up.
- It is less intricate.
- Less of the CPU is being used.
Disadvantages of RIP
A few of RIP’s drawbacks are as follows:
- Using the hop count measure, the route is selected in RIP. If a better-bandwidth path is available, it would not be used in this case. Let’s use a concrete example to help us grasp this situation.
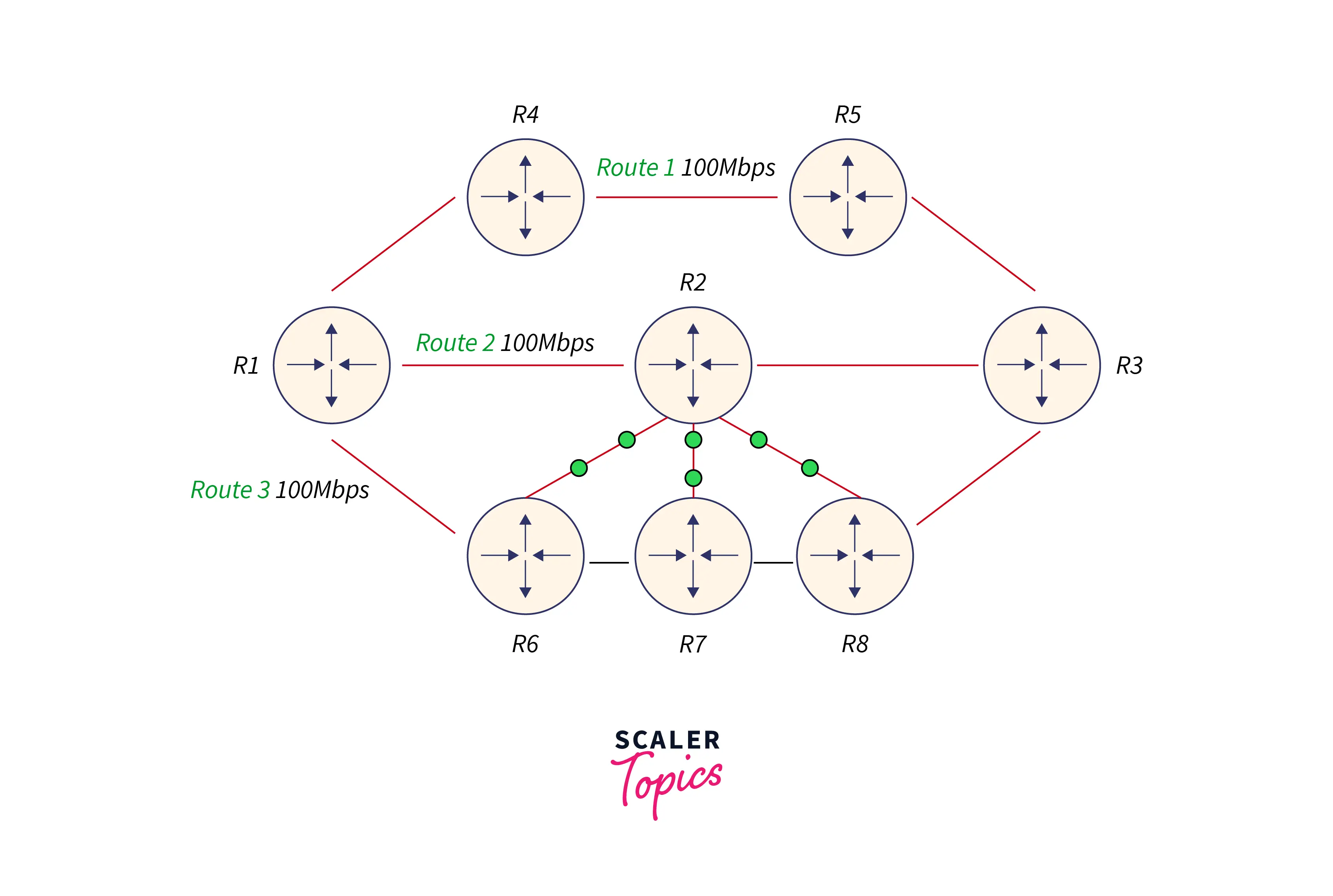
We can see that Route 2 was selected since it had the fewest hops in the above image. Data may be transferred to Route 1 for free and more quickly; but, because of the tremendous traffic, data is sent via Route 2, which slows it down. This is one of RIP’s main drawbacks.
- Since the RIP is a classful routing protocol, it is incompatible with the
VLSM (Variable Length Subnet Mask). A protocol that excludes the subnet mask information from routing updates is the classful routing protocol. - It generates a lot of traffic by broadcasting the routing modifications throughout the whole network. The routing database in RIP is updated every 30 seconds. Every time an update happens, it sends a copy to every neighbor but the one who initiated the update. There is a lot of traffic created by sending updates to every neighbor. A split-horizon rule is what this one is called.
- It has a slow convergence issue. It frequently takes minutes for the system to stabilize or choose an alternate route when a router or connection dies; this issue is referred to as slow convergence.
- The maximum number of hops that a RIP can support is 15, therefore a RIP can support up to 16 hops.
- The administrative separation factor is 120. (Ad value). When compared to a protocol with a higher Ad value, the protocol with a lower Ad value is more dependable.
- Since the RIP protocol has the greatest Ad value among the routing protocols, it is less dependable.
Enhanced Interior Gateway Routing Protocol
On a computer network, the sophisticated distance-vector routing protocol known as Enhanced Interior Gateway Routing Protocol (EIGRP) is used to automate routing configuration and choices. Only Cisco routers may use the protocol, which was created by Cisco Systems as a proprietary protocol. While reserving key EIGRP capabilities, like EIGRP stub, required for DMVPN and large-scale campus deployment, strictly for themselves, Cisco chose to enable other companies to freely implement a restricted version of EIGRP with certain of its related benefits, such as High Availability (HA). RFC 7868, which was released with informational status in 2016 and did not become a standard on the Internet Standards Track, contained the implementation-related information that was required. This allowed Cisco to continue to manage the EIGRP protocol.Interior Gateway Routing Protocol (IGRP) was superseded by EIGRP in 1993. The Internet Protocol’s switch to classless IPv4 addresses, which IGRP could not handle, was one of the main causes of this.
EIGRP is a distance vector and link state routing protocol that makes use of the Diffusing Update ALgorithm (DUAL) (based on research from SRI International) to increase protocol effectiveness and help avoid calculation mistakes when attempting to establish the optimum path to a faraway network. Five metrics—bandwidth, load, latency, dependability, and MTU—are used by EIGRP to assess the path’s value. Five distinct messages are used by EIGRP to interact with its neighbor routers. They are Hello, Update, Query, Reply, and Acknowledgement messages in EIGRP.
Features
The characteristics listed below are supported by EIGRP:
CIDR (Classless Inter-Domain Routing)with variable length subnet masking support. In the absence of auto summary being enabled, routes are not summed at the classful network border.- Support for load balancing across several parallel connections between locations.
- Being able to switch between several login credentials.
- Between two routers, there is MD5 and SHA-2 authentication.
- When a route is updated, topological modifications are sent rather than the complete routing table.
- Periodically checks for open routes and, if any modifications have been made, propagates the new routes to nearby routers.
- Runs distinct routing processes for
Internet Protocol (IP), IPv6, IPX, and AppleTalk usingprotocol-dependent modules (PDMs). - Adherence to IGRP routing protocols’ backward compatibility.
EIGRP Advantages
- EIGRP may route several various layer protocols when using protocol-dependent modules.
- The EIGRP setup was designed to be simple to set up.
- EIGRP may be activated using a network command and an EIGRP Autonomous number.
- Within 200 ms, EIGRP will converge.
- Uneven cost load balancing is carried out using the EIGRP protocol.
- It will show the differences between the links if the destination has more than one connection.
- EIGRP’s Manual Route Summarization capability is one of its more sophisticated ones. It increases stability and minimizes the size of the routing table.
Cons of EIGRP
- The CISCO network equipment supports the EIGRP routing protocol.
- EIGRP is a distance vector routing technique that depends on routes given by neighbors.
- Due to its inability to be extended, it cannot handle upcoming apps.
Open Shortest Path First (OSPF)
In an OSPF network, each router or system maintains a link-state database that is identical and contains information on the topology of the area. Link-state advertisements (LSAs), which each router or system in the area gets from every other router or system in the same area as well as LSAs it makes on its own, are used to create each system’s link-state database. A packet known as an LSA provides data on neighbors and path expenses. Each router or system computes a shortest-path spanning tree with itself as the root using the SPF method based on the link-state information.
The following are some major benefits of OSPF:
- OSPF is more suited for handling huge, diverse internetworks than distance-vector routing algorithms like the
Routing Information Protocol (RIP). When the network topology changes, OSPF may quickly recalculate the routes. - By dividing an
Autonomous System (AS)into areas and maintaining distinct area topologies, you may use OSPF to reduce the amount of OSPF routing traffic and the size of each area’s link-state database. - Multipath equal-cost routing is offered by OSPF. By employing various next hops, redundant routes may be added to the TCP stack.
- The Hello protocol is used by routers or other devices in an OSPF network to deliver Hello packets through their OSPF interfaces to locate neighbors once they have checked that their interfaces are operational. Routers or other devices with interfaces to the shared network are referred to as neighbors. The next step is the establishment of adjacencies, which involves nearby routers or systems exchanging link-state databases.
- To determine the optimum route between the source and the destination router using it is own Shortest Path First,
Open Shortest Path First (OSPF)is a link-state routing protocol. As one of theInterior Gateway Protocols (IGP)or the protocol that tries to move the packet within a sizable autonomous system or routing domain, OSPF is designed by theInternet Engineering Task Force (IETF). It is a network layer protocol that employs AD value 110 and operates on protocol number 89. OSPF employs the multicast addresses224.0.0.5and224.0.0.6for routine communication and updating thedesignated router (DR)andbackup designated router, respectively (BDR).
OSPF declares The OSPF-operating device transitions through many stages. These are the states:
- Down – The interface is in this state when no hello packets have been received.
- Keep in mind that The Downstate does not imply that the interface is offline physically. It denotes that the OSPF adjacency procedure has not yet begun in this case.
- The greeting packets from the other router have been received, and the router is in the INIT state.
- 2WAY – Both routers have received hello packets from other routers when they are in the 2WAY state. Connection in both directions has been achieved.
BGP Communities
For tagging routes and changing the BGP routing policy on upstream and downstream routers, BGP communities offer extra functionality. On each property, BGP communities can be added, deleted, or updated selectively as the route moves from router to router.RFC 4360, released in 2006, added an extended format and increased the capabilities of BGP communities. Extended BGP communities offer organization for different kinds of data and are frequently used for VPN services.
Devices running IOS and NX-OS by default do not announce BGP communities to peers. The BGP address-family configuration command neighbor IP-address send-community [standard | extended | both] is used to enable communities on a neighbor-by-neighbor basis, and NX-OS devices utilize the neighbor address-family configuration command send-community [standard | extended | both]. Unless all of the optional extended keywords are specified, standard communities are delivered by default.
To EBGP peers, regular BGP communities must be advertised using the neighbor address-family configuration command send-community-ebgp, and extended BGP communities must be advertised using the command send-extended-community-ebgp. IOS XR automatically advertises BGP communities to IBGP peers. If both community formats are to be sent to an EBGP peer, both instructions are necessary.
The four well-known BGP communities are as follows:
- Internet: inform all BGP neighbors about the prefix.
- No-Advertise: don’t inform any BGP neighbors about the prefix.
- No-Export: don’t let any eBGP neighbors know about the prefix.
- Avoid promoting the prefix outside of the sub-AS, local-AS (this one is used for BGP confederations).
BGP communities may be used in a variety of ways, as you have seen. They are crucial for tagging routes, modifying traffic, and carrying out different operations on the BGP properties of routes that match particular communities.
As a service provider, you may work with your clients to establish a specific policy that will be applied to their prefixes using communities; this provides your clients the ability to modify the policy of a prefix simply by changing the community attribute value without your assistance.
Conclusion
- A numerical value can be set to a particular prefix and advertised to other neighbors as the BGP community attribute. After analyzing the community value after receiving the prefix, the neighbor will decide whether to filter or adjust additional properties.
- To determine the optimum route between the source and the destination networks,
Routing Information Protocol (RIP)employs hop count as a routing statistic. It operates on the Network layer of the OSI architecture and is a distance-vector routing protocol with an AD value of 120. Port 520 is used by RIP. EIGRP, a dynamic routing protocol, is employed to determine the most efficient path for a packet to travel between any two layers.EIGRPemploysprotocol 88and operates at the network layer of theOSI architecture. The optimum route between two layer 3 devices (routers or layer 3 switches) using EIGRP is determined using metrics.- As a link-state routing protocol, OSPF allows routers to communicate topological details with their closest neighbors. A link state routing system like
OSPFhas the primary benefit of enabling routers to determine routes that meet certain requirements since it has comprehensive topology knowledge. - Communities can be used to identify a group of prefixes that have something in common. These marks can be used by upstream providers to implement a standard routing strategy, such as filtering or designating a particular local preference.