What Are Open Ports and How Do They Work?
A port is a communication endpoint where all network communications begin and end. A port recognizes a specific process or service and is assigned a number based on its specialized function. Network ports allow devices to communicate with each other remotely over the internet, regulating how information or data flows to a computer from the internet or other application. In other words, network ports act as gates that allow data to flow into a network.
Despite how complicated the term “port’ sounds, you presumably already have some experience with them. For instance, if you’ve ever installed a home router, you’ve probably heard of TCP/IP or Dynamic Host Configuration Protocol (DHCP), which enables the device to communicate with the internet. Ports are nothing, but they act as a gateway allowing devices, services, and networks to share information and communicate with each other.
In simpler words, ports allow devices to specify what to do with data received over a similar network connection. For example, email is routed through a different port (port 25) than webpages or webpages (port 80). A port that is currently in use cannot be used by another service and will return an error message. The figure above shows the port’s significance in communication between two devices.
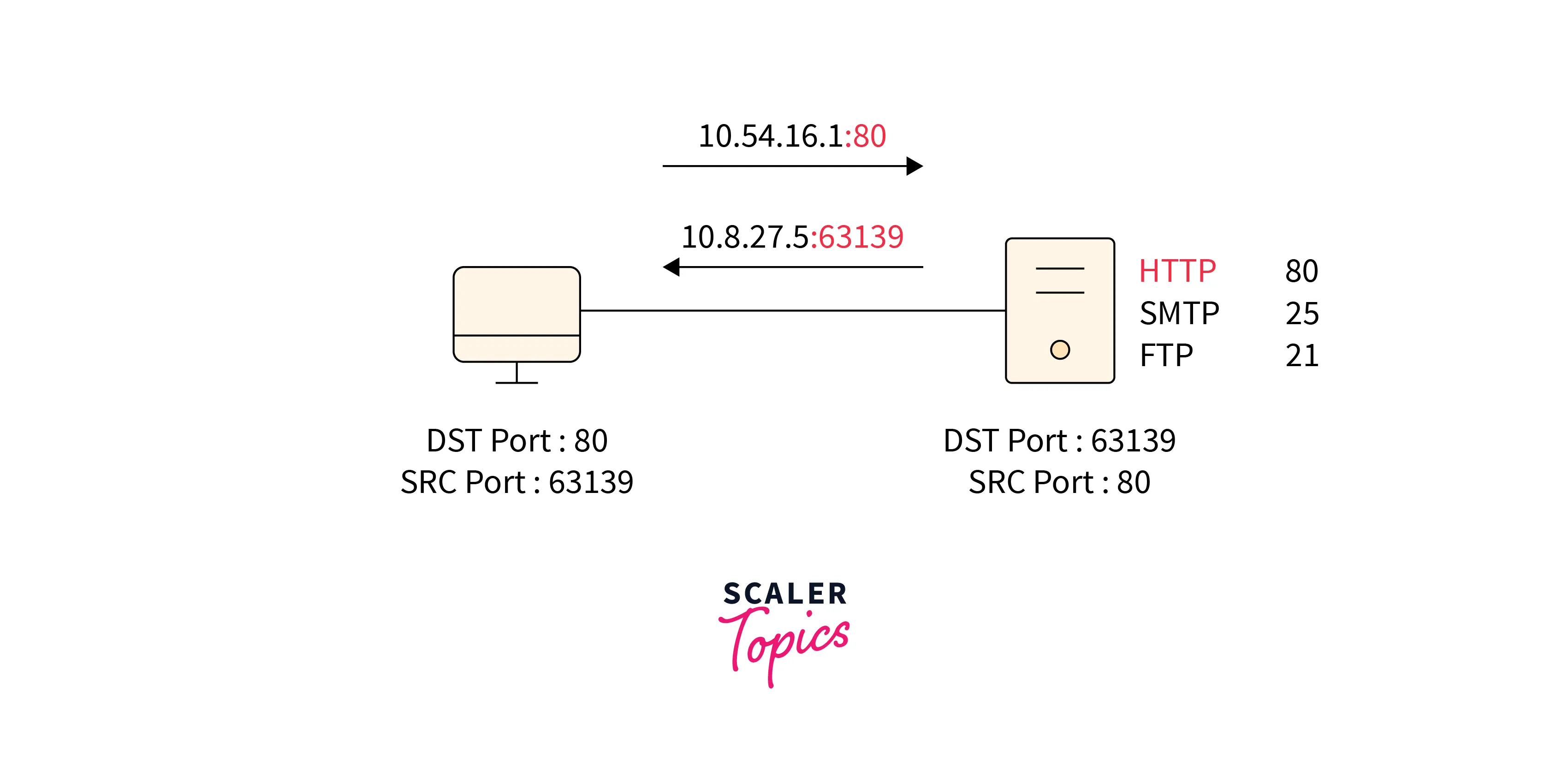
Two of the major protocols of the transport layer, TCP and UDP, use ports to send and receive data packets. A TCP or UDP port number currently accepting packets is referred to as an open port. In other words, it is supported by a system that receives communication. On the other side, a closed port rejects or simply ignores the packets.
What Makes Open Ports Dangerous?
Consider a fence around a house to visualize whether a port is unsafe or secure. There is a gate on every fence. This gate is identical to the port, and the fence around the house represents the security and privacy boundaries of the system. This gate can be locked or unlocked. If you leave the gate open, anyone can access your yard, putting your house in danger. If you lock the gate, only the authorized person will be able to enter your yard, increasing the security of your home.
Network ports function in the same way. Although each IP address can have up to 65,353 distinct ports, most of them are numerically named and known to cyber criminals. For example, here is a list of the most popular and widely used ports and the services they enable:
| Port Number | Protocol | Application |
|---|---|---|
| 20 | TCP | FTP data |
| 21 | TCP | FTP Control |
| 22 | TCP | SSH |
| 23 | TCP | Telnet |
| 25 | TCP | SMTP |
| 53 | UDP,TCP | DNS |
| 67,68 | UDP | DHCP |
| 69 | UDP | TFTP |
| 80 | TCP | HTTP |
| 110 | TCP | POP3 |
| 443 | TCP | SSL |
| 16,384 to 32,767 | UDP | RTP (Real-Time Transport Protocol)-based Voice and Video |
Cybercriminals frequently attempt to exploit these ports to access networks since they are public-facing, similar to a fence gate around a house. Cybercriminals look for open ports in the same way that a thief looks for unlocked gates. Once they know which ports are open, they use a botnet, or a large number of victim computers connected across the internet, to send a flood of information to them, comparable to trying to push 100 people through a fence gate. The network is overloaded by this traffic, making it unable to support ongoing business operations.
Attackers can simply exploit flaws in applications that listen on a port. Hackers can penetrate a network by exploiting security flaws in older, unpatched software, as well as weak credentials and misconfigured services. Some ports are not meant to be exposed to the public. For example, the Server Message Block (SMB) protocol, which operates on TCP ports 139 and 445, is enabled by default in Windows machines. It is only intended for file and printer sharing and remote administration. Due to multiple weaknesses in earlier versions of the SMB protocol, it was used by malicious attackers in the well-recognized WannaCry ransomware attack.
How to Secure Open Ports
Let’s look at some of the important points to secure open ports.
Identify Open Ports
You can’t protect what you don’t recognize has to be protected. Scanning your IT stack, including applications and any network-connected devices, to identify what ports are open and whether the configurations are appropriate is the first step in safeguarding risky ports.
Scan Network Ports Regularly
On clients’ networks, we must run a process that searches for dangerous open services, such as unencrypted legacy ports, so administrators can shut them down or replace them with a secure version. Every port on every managed device is subjected to a weekly assessment to determine which ones must be restricted due to risk.
Access Ports Using a Secure Virtual Private Network (VPN)
A VPN (Virtual Private Network) conceals your IP address by routing it through a specially configured distant server maintained by a VPN host. So, if you use a VPN to surf the web, the VPN server becomes your data source. This means that your ISP and other third parties cannot know which websites you visit or what data you send and receive online. If a company uses RDP (Remote Desktop Protocol), it must utilize an end-to-end encrypted virtual private network (VPN) connection to access RDP rather than leaving it open to the internet. Users must first connect to the VPN before they may access your RDP. In this manner, the VPN must first be attacked and bypassed before the attackers can gain access to a miscellaneous RDP connection.
Use Multi-factor Authentication
MFA (Multi-factor authentication) is a security mechanism that needs several ways of authentication from distinct categories of credentials to validate a user’s identity for a login or other transaction. Multifactor authentication combines two or more separate credentials: what the user knows, such as a password; what the user owns, such as a security token; and what the user is, which is verified using biometric means. Multi-factor authentication (MFA) dramatically aids in the security of an open service. Even if there is a credential leak or a brute-force attempt, the miscellaneous attackers will be faced with an additional code or authentication technique that they cannot bypass.
Implement Network Segmentation
Network segmentation is the process of dividing a more extensive network into smaller segments or subnets. If your camera system has an open DVR (Digital Video Recorder) connection, you can secure it by isolating it from the rest of your network. Even if someone manages to hack this DVR, they won’t be able to access your server, workstations, or other important data.
How to Manage Our Attack Surface?
Open ports allow services and applications to work correctly. On the other hand, certain ports may offer security risks to your network. Your attack surface (the total number of possible locations that attackers can target) should be kept to a minimum. A detailed network evaluation can help you detect risks in your physical and digital surroundings, such as unused, exposed ports. Some open ports are harmful to your system and should be closed. Let’s look at some points that will guide you to manage and protect your service area.
- Understand port usage:- Most businesses do not require every port on every IP address to be open. Many scanning programs that detect open ports also provide information on whether the open ports are being used.
- Know what services use ports:- On your network, many services will connect to various ports. To understand port utilization, you need to find out what protocols or processes are using the port. If your system administrator discovers a procedure or protocol he or she is unfamiliar with, it may point to a security flaw.
- Close the riskiest ports:- The
Internet Assigned Number Authority (IANA)provides details about which ports are targeted by hackers and which services use particular ports. With this knowledge, you may more effectively secure ports that could be dangerous while keeping the ones required for business operations operational.

The figure above divides the various range of ports category-wise.
Conclusion
- A port is a communication endpoint where all network communications begin and end. A port recognizes a specific process or service and is assigned a number based on its specialized function.
- Ports enable device-to-device communication. Applications and services that interact with the internet essentially wait for connections from outside sources by listening on ports. Without ports, hosts cannot communicate with one another across the internet.
- Attackers can simply exploit flaws in applications that listen on a port. Hackers can penetrate a network by exploiting security flaws in older, unpatched software, as well as weak credentials and misconfigured services.
- Some of the important points to secure open ports.
- Identify open ports.
- Scan network ports regularly.
- Access ports using a secure virtual private network (VPN).
- Use multi-factor authentication.
- Implement network segmentation.
- We must run a process on clients’ networks that searches for dangerous open services, such as unencrypted legacy ports. This also helps to identify the ports that are already affected, so administrators can shut them down or replace them with a secure version.
