Explanation of an Access List. Access control lists (ACLs) execute message clarifying to regulate the movement of messages across a network. A message is describing supplies security by restricting traffic into a connection, limiting user and device approach to a network, and restraining traffic from going away from a network.
Introduction
Access-list (ACL) could be a set of commands for managing network traffic and decreasing network rushes. ACLs are to purify the traffic supported by the set of controls outlined for the arrival or departure of the network.
Access-list (ACL) features:
- The set of directives outlined is compared serial-wise manners, with the primary line, secondary, tertiary, and so on.
- Will compare the message till it equals the rule. No more comparison occurs when will reach power and execute the rules.
- There is a suggested contradiction at the tip of each ACL(Access list) : if no circumstances or rules match, then reject the message.
Types of Access List
Mainly there are two different significant kinds of Access-list (ACL) specifically:
Standard Access-list
It is the Access list created for victimizing the supplied IP address only. These Access lists allow or deny the complete protocol suite. Which generally doesn’t discriminate among the IP traffic like protocol, TCP, UDP, HTTPS, etc. By victimization numbers $1-99$ or $1300-1999$, the router can be aware of it and understand it as a standard ACL and the specific address as the origin IP address.
Extended Access-list
Extended Access-list is the Access List that uses supply IP, Goal IP, origin port, and Goal port. We can mention which IP traffic should be permitted or denied for these Access Lists. These utilize range from $100-199$ and $2000-2699$.
Additionally, there are two classifications of access-list
Numbered Access List
Numbered access lists are the access list that can not be canceled once created; that is, if we would like to get rid of any rule from an Access-list then this cannot be permissible within the case of the numbered access list.
If we try to delete the direction from the access list, it will remove the entire access list. The numbered access list will be utilized with the pair standard and extended access lists.
Named Access List
A name is appointed to spot an access list in the named access list. It is permitted to remove a named access list, In contrast to the numbered access list. These will be utilized with standards and extended access lists like numbered access lists.
Standard Access List
Standard Access-list is less likely to be utilized as differentiated to expanded access-list because the whole IP protocol suite will be permitted or challenged for the traffic as it can’t discriminate among the various IP protocol traffic.
A. Features
- Standard Access-list has mostly appealed about destinations still not every time.
- The actual connection or sub-connection will be rejected during a standard access list.
- The Standard access list utilizes the scale $1-99$ and expanded scope $1300-1999$.
- The Standard access list is enforced using the source IP address at most.
- If numbered with standard Access-list will be utilized, then remember that can’t remove rules.
- Will remove will delete one in each foundation.
- However, when a standard Access-list is utilized, we get the accommodation to remove a rule from the access list.
B. Configuration
There may be a little topology during which there are three sections, particularly sales, finance, and marketing. The sales section encompasses a connection of 172.16.40.0/24, the Finance section includes a reference of 172.16.50.0/24, and the marketing section comprises an association of 172.16.60.0/24. Now, I wish to contest the connection between the sales and finance sections and permit others to succeed in that connection.
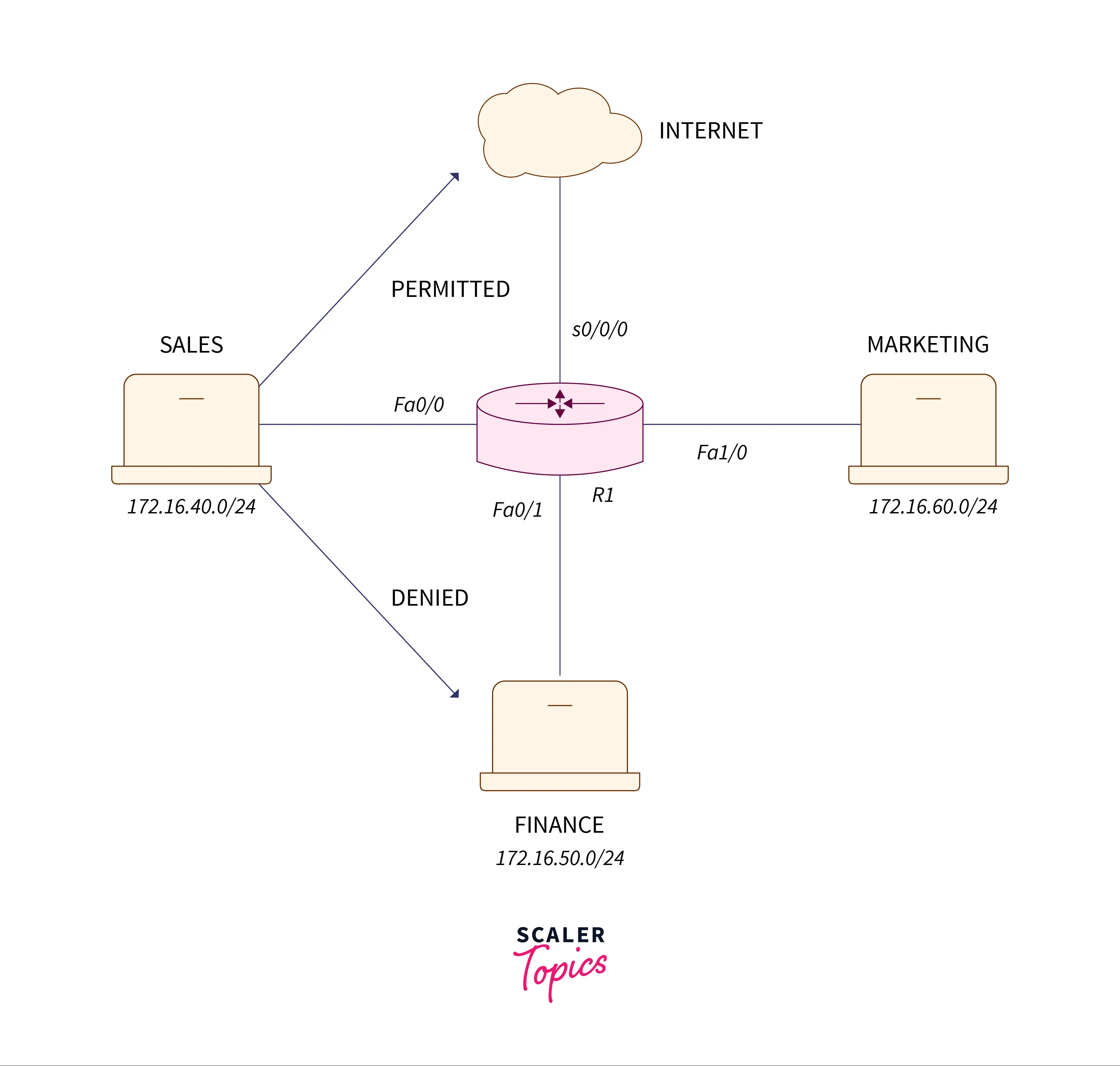
Currently, 1st customizing numbered standard access – list for challenging any IP network from sales to finance section.
R1# config terminal
R1(config)# access-list 10 deny 172.16.40.0 0.0.0.255You can’t identify the actual IP traffic allowed or refused in an extended access list. In addition, note that a wildcard vizard has been used ($0.0.0.255$, which implies Subnet vizard $255.255.255.0$). Ten is utilized from the quantity standard access-list range.
R1(config)# access-list 110 permit ip anyAs you know, there is an indirect contradiction at the tip of each access list which implies that if the traffic doesn’t equal any of the principles of the access list, then the traffic is to be released.
Framing implies that supply having any IP address traffic can reach the finance section, excluding the traffic that ties the above rules you have created.
R1(config)# int fa0/1
R1(config-if)# ip access-group 10 outNow, you got to use the access list on the intersection of the router :
As you keep in mind that the standard access-list is mainly appealed to the goal and here conjointly if you apply an access list about to the target, it will convince our requirement, therefore, outward to intersection fa0/1 has been used.
C. Example
Now, examining the constant topology, we will create a named standard access list.
R1(config)# ip access-list standard blockaclBy utilizing this instruction, we have created an access list named blockacl.
R1(config-std-nacl)# deny 172.16.40.0 0.0.0.255
R1(config-std-nacl)# permit anyAnd then the constant organization we have got wiped out in a numbered access list.
R1(config)# int fa0/1
R1(config-if)# ip access-group blockacl outExtended Access List
It is one of all the kinds of Access-list that is usually utilized because it can discriminate IP traffic so that the total traffic won’t be allowed or refused as just in a standard access list. These are the Access List that utilizes each supply and goal IP address and conjointly the port numbers to determine IP traffic. While in this kind of Access List, we will also point out which IP traffic ought to be permitted or refused. These empower the scales of $100-199$ and $2000-2699$.
A. Features
- The extended access list is usually claimed adjacent to the supply, however, not all the time.
- In the Extended access list, message training took place on the premise of supplied IP address, targeted goal IP address, and port numbers.
- In an extended access list, specific services are allowable or deniable.
- Extended Access List is generated from
100 – 199on a vast scale of2000 – 2699. - If a number with an extended Access list is utilized, then remember that rules can’t be removed.
- If any of the foundations are revoked, then the complete access list is removed.
- If a name with an extended Access-list is utilized, then we have the elasticity to cancel a rule from the access list.
B. Configuration
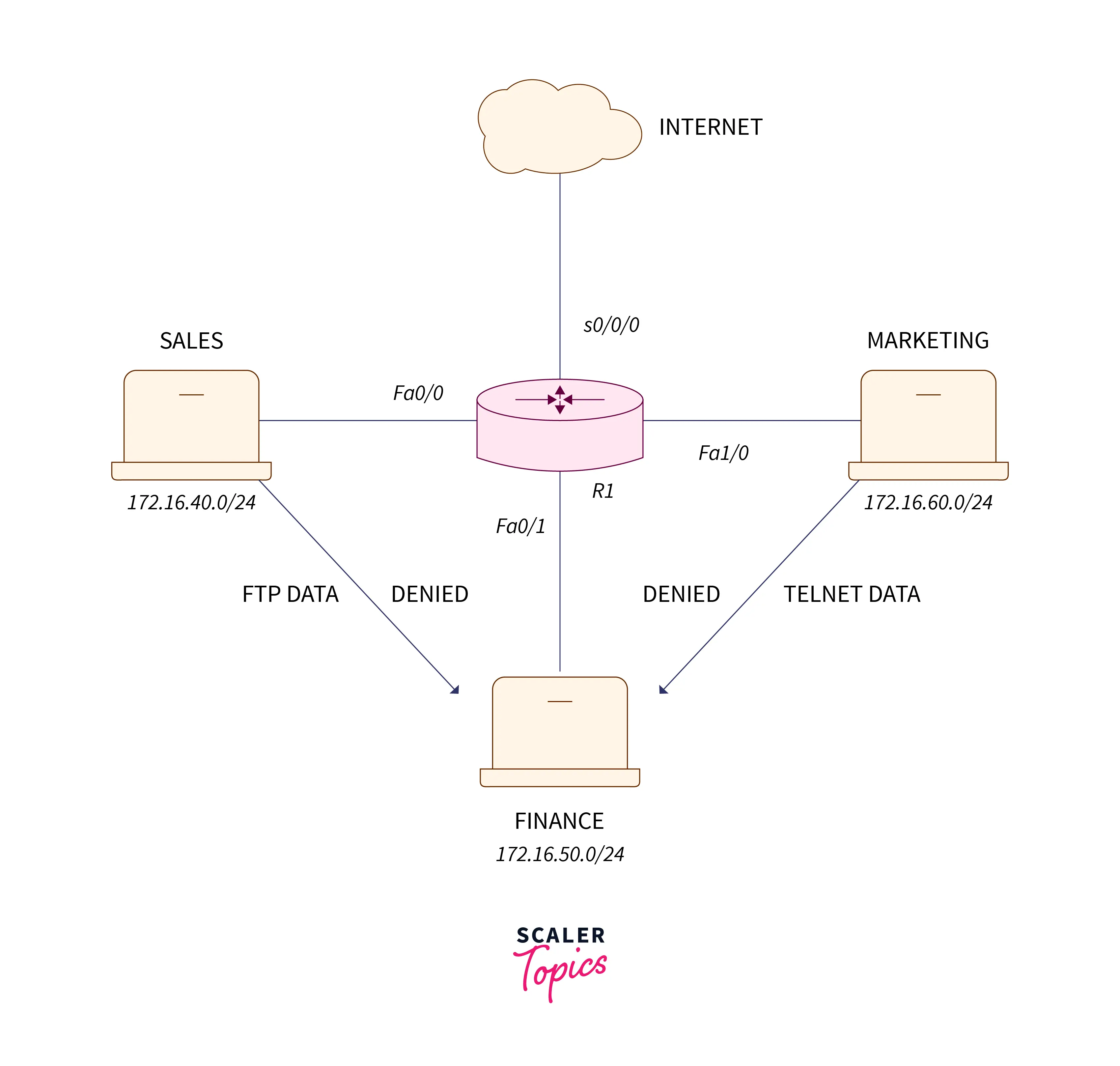
This is the small topology during which there are three different domains, particularly sales, finance, and marketing. The sales domain enforces a network of 172.16.10.40/24, the Finance domain comprises a network of 172.16.50.0/24, and the marketing domain holds a network of 172.16.60.0/24. Now, we would like to deny the FTP association from the sales domain to the finance section and reject telnet to the Finance domain from each one of the sales and marketing domains.
Therefore, the 1st configuring numbered extended access – list for refusing FTP association from sales to finance section.
R1# config terminal
R1(config)# access-list 110
deny tcp 172.16.40.0 0.0.0.255 172.16.50.0 0.0.0.255 eq 21In this, we tend to produce a numbered Access-list during which we tend to use a 110, which is utilized from the extended access-list scale and discard the sales domain (172.16.40.0)to create an FTP association to the finance domain (172.16.50.0).
Here, FTP utilizes TCP(Transmission Control Protocol) and port number 21. Henceforth, we have to clarify whether they allow or return the circumstances concerning the need. Also, after eq, we got to use the port range for the required application layer protocol.
Now, we have to refuse telnet interrelation to the finance domain from each sale and Marketing domain which suggests nobody ought to finance the department. Configuring for a similar.
R1(config)# access-list 110
deny tcp any 172.16.50.0 0.0.0.255 eq 23Here, we got used the keyword any, which suggests $0.0.0.0 0.0.0.0$, which is an IP address found in any subnet mask. As telnet usage port number 23, we got to identify port number 23 after eq.
R1(config)# access-list 110 permit ip anyNow, this can be the only necessary part. As we tend to grasp already, there is an implicit deny at the top of each access list which suggests that if the traffic doesn’t match any of the principles of Access-list, then the traffic is released.
Indeed, it implies that an origin having any IP address traffic can reach the finance domain except the traffic that it compares with the above rules that we created.
Now, we have to use the access list on the intersection of the router:
R1(config)# int fa0/1
R1(config-if)# ip access-group 110 outWe bear in mind that we have to use the extended access list as shut as conceivable to the origin; however, here, we have to apply it close to the destination as a result of we have to block the traffic from each of the sales and marketing sections.
Therefore, we have to use it close to the target goal here, or else we have to create a distinct access list for fa0/0 and fa1/0 incoming.
C. Example
Reviewing the identical topology, we will build a labeled extended access list.
R1(config)# ip access-list extended blockaclBy victimizing this instruction, we created an access list labeled blockacl.
R1(config-ext-nacl)# deny tcp 172.16.40.0 0.0.0.255 172.16.50.0 0.0.0.255 eq 21
R1(config-ext-nacl)# deny tcp any 172.16.50.0 0.0.0.255 eq 23
R1(config-ext-nacl)# permit ip anyAnd then the identical configuration we got finished in a numbered access list.
R1(config)# int fa0/1
R1(config-if)# ip access-group blockacl outReflexive Access List
Reflexive Access-list is an access list that enables the replies solely to the messages of the discussions initiated inside the network from the external network.
A. Working
When a discussion is initiated inside the network and goes surface the network through the router, effective Reflexive Access-list and Reflexive Access-list are activated. Therefore, it generates a short-term entry for the traffic that is initiated inside the connection and permits only those traffic from the external network that may be a part of the session (traffic created inside the web). This short-entry entry is disconnected once the session ends.
Characteristics of temporary entry:
- The arrival identifies the equivalent source and destination address because of the native outbound message that the message is going outside the network, excluding they are exchanged once coming back from outside the connection.
- The arrivals ought to have an identical source and target port variety because of the beginning departing message. Besides, they are interchanged once they come back from the outermost connection.
- The entry ought to have the coupled protocol because of the original departing packet.
B. Characteristics
- The reflexive Access list should be nested within the labeled Extended Access list.
- It cannot be claimed straight to an intersection.
- A short-term entry is created once a session starts and accordingly demolished once the session finishes.
- It does not have suggested denial at the tip of the Access list.
- Similar to an average access list, if one in all the circumstances matches, then no lots of arrivals are evaluated.
- The Reflexive Access list cannot be outlined with a numbered Access list.
- A reflexive Access list cannot be described with a labeled or numbered standard Access list.
C. Configuration
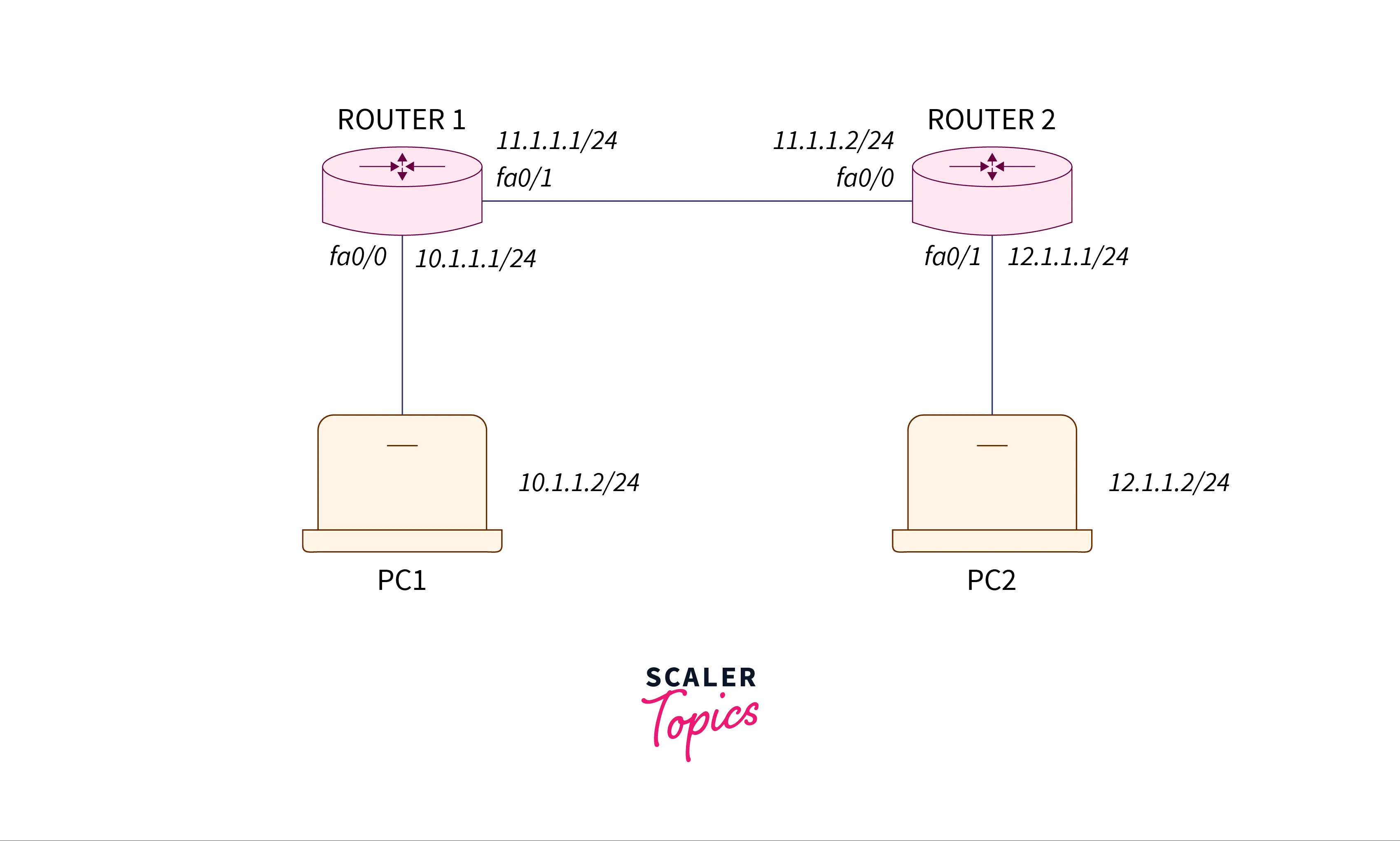
There are two routers, namely R1 (IP address – 10.1.1.1/24 on fa0/0 and 11. 1.1.1/24 on fa0/1),R2 (IP address-11.1.1.2/24 on fa0/0 and 12.1.1.1/24 on fa0/1) and Personal Computer1 (IP address-10.1.1.2/24) and Personal Computer2 (IP address-12.1.1.2/24).
Initially, we are going to offer routes, along with EIGRP, to any of all the routers so that Personal Computers can ping one another.
Configuring EIGRP on R1 :
router1(config)#router Eigrp 100
router1(config-router)#network 10.1.1.0
router1(config-router)#network 11.1.1.0
router1(config-router)#No auto-summaryConfiguring EIGRP on R2 :
router2(config)#router Eigrp 100
router2(config-router)#network 11.1.1.0
router2(config-router)#network 12.1.1.0
router2(config-router)#No auto-summaryNow, we are going to enable IP, TCP(Transmission Control Protocol), and UDP(User Datagram Protocol) traffic from within the system, (10.1.1.0 network) and evaluate the traffic returning from outside the shell of the network (12.1.1.0 and 11.1.1.0 network). Making Access list is tagged as reflexive for the within traffic going exterior.
router1(config)#ip Access-list extended reflexive
router1(config-ext-na)#permit ip any any reflect ip_database
router1(config-ext-nacl)#permit tcp any any reflect tcp_database
router1(config-ext-nacl)#permit udp any any reflect udp_databaseHere, we have allowed IP, TCP(Transmission Control Protocol), and UDP(User Datagram Protocol) traffic, and we have labeled it as ip_database, tcp_database, and udp_database.
Note:
Here, Reflexive is the name of the Access list and not a code word. Now, put this Access list to the departing of int fa0/1 of R1 so that the traffic going out the router ought to be permitted.
Now, appeal an access list for inward traffic that is traffic returning within the network. We should always enable only that traffic to come back within if it is triggered by the inside (10.1.1.0) connection.
router1(config)#ip access-list extended reflexive_in
router1(config-ext-nacl)#permit Eigrp any any
router1(config-ext-nacl)#evaluate tcp_database
router1(config-ext-nacl)#evaluate udp_database
router1(config-ext-nacl)#evaluate ip_databaseHere, we have authorized EIGRP traffic so that capabilities should be there among the routers. Otherwise, no traffic will be able to return within the ether network.
We have appraised the udp_databse, ip_database, and tcp_database so that traffic (TCP, UDP, or IP) is granted that has begun in the middle of the network. Now, apply this to terminal fa0/1 in the center of the direction as the result of the traffic returning at the internal level should be rated.
router1(config)#int fa0/1
router1(config-if)#ip access-group reflexive_in inD. Advantages
- Easy to execute.
- Provides more extensive management over the traffic coming back from the crust network.
- Supplies security from actual DOS charges and spoofing.
E. Disadvantages
- Some requisitions use active ports because failure will occur. As for reflexive Access-list, the origin and destination ports ought to be stable.
Time-Based Access List
The time-based access list is a sort of access list that permits network access on the premise of your time amount. It is helpful once you need to put restrictions on outward or arriving traffic at a specific time of the day or on particular days of every week.
For example, if we wish to deny staff access to the Internet during operating hours and permit access at lunchtime. In these situations, we can implement a Time-based access list rejecting access to the Internet.
Time-based Access Lists were found in Cisco IOS Software Release 12.0.1.T. to permit access management support at the time. It best works with NTP (Network Time Protocol) synchronization, however, it will work with router clock.
A. Procedure
To apply a Time-based access list, they are a standard procedure:
Define time range:1st, we must outline a time range that will trace with the assistance of the keyword absolute or regular.
Absolute :
describes a total time. For instance, if we wish to block ICMP(Internet Control Management Protocol) on a specific subnet for the final time from (Tuesday to Friday), then we can use the complete keyword.
Periodic :
describes a recurring time. For instance, if we wish to block ICMP on a particular subnet every weekday (Monday to Friday), we can use the frequent keyword.
Define an access list:
Within the next step, an access list will be outlined, during which we will apply our time range.
Access-list to an interface:
The access list can be applied to an intersection or line-vty in keeping with our needs.
B. Configuration
The general instruction for configuring time-based Access Lists is time-range, which is utilized to clarify the amount of your time which is often revenant, or a selected instance that happens solely once the Access List statement is valid.
R(config)# time-range time_range_nameUpon executing this instruction, you are placed in Access List sub-configuration mode, during which you can clarify a one-time only (absolute) or recurring (periodic) kind of time vary.
ROUTER(config-time-range)# absolute [start_time start_date][end_time end_date]
ROUTER(config-time-range)# periodic day_of_the_week hh:mm to [day_of_the_week] hh:mmabsolute:
Identify one fundamental period for which the time vary is legit; you will describe a starting time, an ending time, or both.
periodic:
Define a recurring absolute period for which the time scale is legit. After making time ranges, you want to activate them by putting the time scale parameter to the Access List statement :
Router(config)# access-list {100-199} {permit} protocol source-addr [source-mask][operator operand] destination-addr [destination-mask][operator operand] [established][log | log-input] [established][time-range name_of_time_range]The access list statement is processed only when the router falls through the specified amount.
C. Example
Suppose you would like to forbid the scholars to access the web throughout categories, except throughout lunch – between 12 PM and 1 PM and after school hours – from 3 PM to 7 PM when the school closes.
Note:
The time is framed in 24-hour time (hh: mm), wherever the hours vary from 0 to 23, and therefore, the minutes vary from 0 to 59. For instance, 3 PM is portrayed as 15:00.
R1(config)# time-range student-time
R1(config-time-range)# periodic weekdays 12:00 to 13:00
R1(config-time-range)# periodic weekdays 15:00 to 19:00
R1(config-time-range)# exit
R1(config)# access-list 100 permit ip 192.168.1.0 0.0.0.255 any time-range student-time
R1(config)# access-list 100 deny ip any any
R1(config)# interface FastEthernet 0/1
R1(config-if)# ip access-group 100 in
R1(config-if)# exitAccess list(ACL) one hundred permits students’ traffic to the web throughout lunch and when faculty hours between 3 PM and 7 PM.
Time-based ACLs allow access management supported time and date, offering granular social control of security policy. They get the time from the router’s system clock. Therefore you ought to use Network Time Protocol (NTP) to ensure the time is correct. Namely, Cisco routers should be designed to synchronize with the NTP server, providing the router with the right time and guaranteeing the time-based ACLs you planned to apply incorrectly.
D. Advantages
- Simple to execute.
- It produces the most significant control over the traffic to a director as the traffic can be refused or allowed on time.
Advantages of ACL
- Enhance network execution.
- It provides security because the administrator will track the access list consistent with the wants and deny the unwanted packets from coming into the network.
- Provides management over the traffic because it will allow or deny consistent with the requirement of the network.
Conclusion
- The standard Access-list is usually applied to the destination (but not always).
- The extended Access list is applied to the supply (but not always).
- We can assign just one ACL per interface per protocol per direction, i.e., just one incoming and outgoing ACL is permissible per interface
- We can’t remove a rule from AN Access-list if we tend to area unit exploitation numbered Access-list. It will be deducted from The complete ACL if we try to take away a practice. If we tend to exploit area unit exploitation named access lists, we can delete a particular direction.
- Every new rule further to the access list will be placed at the lowest of the access list, so before implementing the access lists, analyze the complete state of affairs rigorously.
- As there’s implicit deny at the top of each access list, we must always have a minimum of an allow statement in our Access list. Otherwise, all traffic will be restricted.
- Standard access lists and extended access lists cannot have identical names.