Domain Name System poisoning and spoofing are kinds of cyberattacks that use DNS server susceptibility to redirect traffic aside from permissible servers on the way to fraud. When you’ve proceeded to a defrauding page, you may be at a loss on how to resolve it — even with being the exclusive one who can. You’ll be required to know precisely how it works to safeguard yourself.
DNS spoofing and, by extension, DNS cache poisoning are amidst additional misleading cyber threats. Unaccompanied by understanding how the World Wide Web links you to websites may cheat you into anticipating a hacked web page; in several instances, it should simply be on your device. Worse, cybersecurity suites can hardly finish the number of DNS spoof-linked threats.
Scope
- This article discusses What is DNS Spoofing or DNS Poisoning?
- This article also discusses How Does DNS Caching Works and how Attackers poison DNS cache.
- This article briefly focuses on Why is DNS Spoofing a Problem and Examples of DNS spoofing Attacks.
- This article also covers DNS Spoofing vs. DNS Poisoning and How to Prevent DNS spoofing and cache poisoning.
What is DNS Spoofing or DNS Poisoning?
DNS (Domain Name Service) spoofing is the method of poisoning appearances on a DNS server to divert a selected user to a malicious website below the attacker’s control.
The DNS attack generally occurs during a public Wi-Fi setting nevertheless will happen in any state of affairs wherever the attacker can poison ARP (Address Resolution Protocol) tables and force selected user systems into exploiting the attacker-controlled machine because of the server for a particular web page. It’s the primary step during an enlightened phishing attack on public Wi-Fi, and it may also trick clients into installing malware on their systems or divulging sensitive data.
DNS cache poisoning invades false information into a DNS cache so that DNS doubts come back with wrong feedback and clients are managed to the incorrect web pages. DNS cache poisoning is additionally referred to as ‘DNS spoofing.’ IP addresses are the ‘chamber numbers’ of the World Wide Web, allowing web obstruction to appear in the correct places. DNS determiner caches are the ‘campus directory,’ When they deposit defective information, the block goes to the incorrect spots until the cached data is rectified.
Note:-
This does not detach the essential web pages from their IP addresses.
How Does DNS Caching Work?
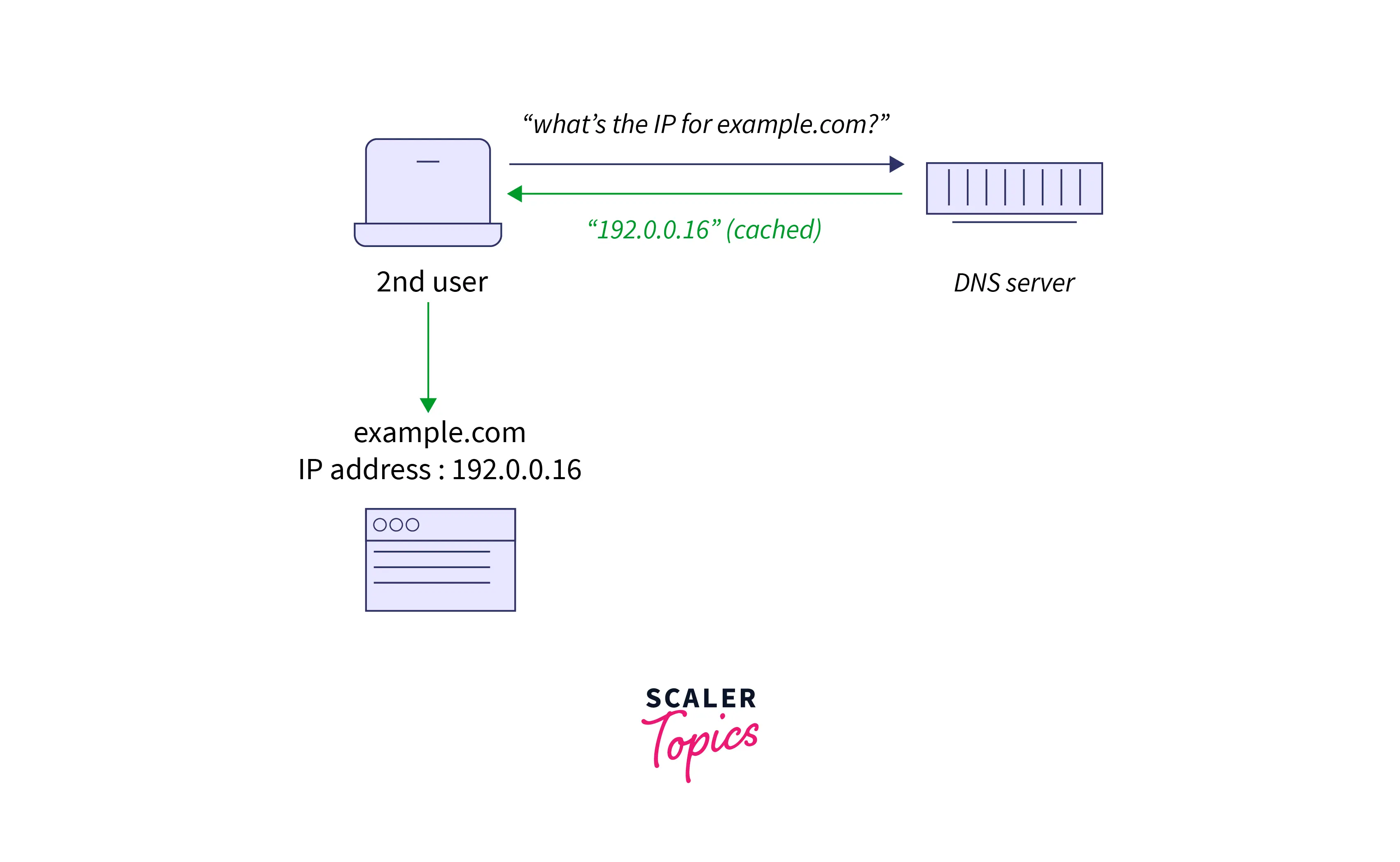
A DNS resolver will reclaim feedback to IP address doubts for a particular quantity of your time. During this means, the resolver can acknowledge upcoming doubts much more swiftly, with no need to speak with the various servers concerned in the default DNS resolution method. DNS resolvers snatch answers in their cache for a long because the selected time to live (TTL) related to that IP address permits them to.
DNS Uncached Feedback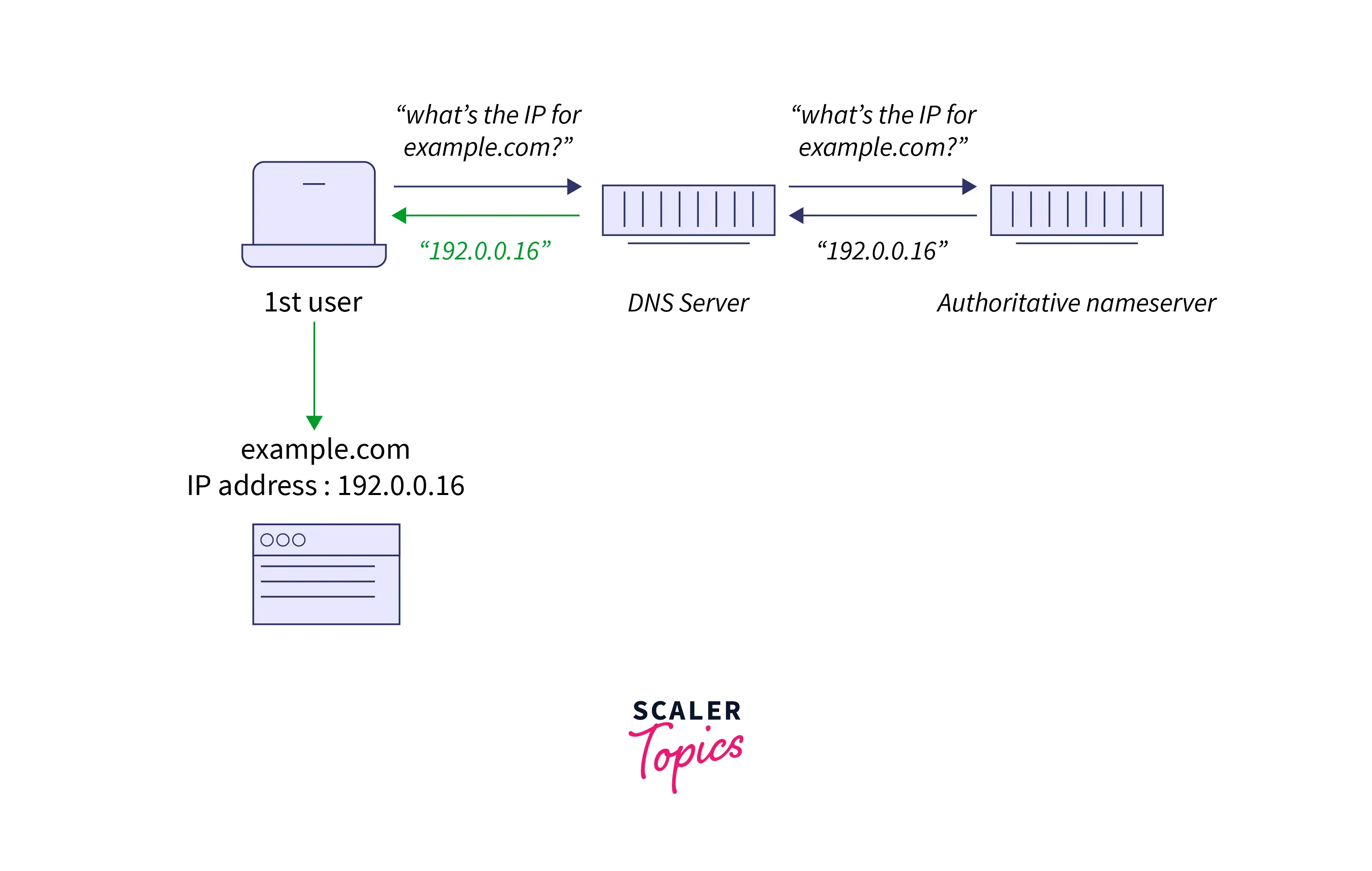
DNS Cached Feedback
How Do Attackers Poison DNS Caches?
An appeal to a DNS resolver and then manufacture the response. Once the DNS resolver inquiries a nameserver. It can potentially result from DNS servers utilizing UDP rather than TCP; presently, there is no authentication for DNS data.
DNS Cache Poisoning Method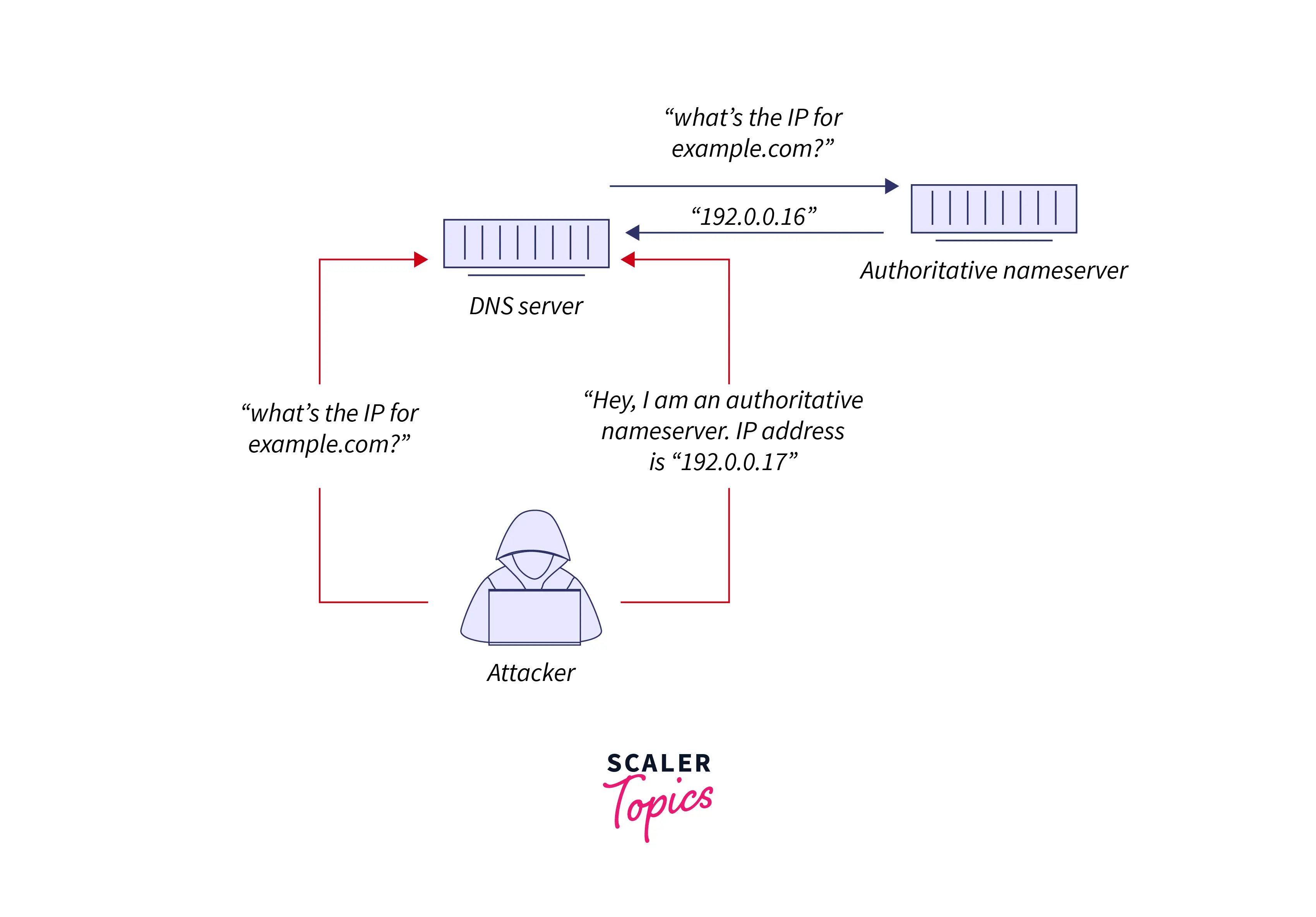
Poisoned DNS Cache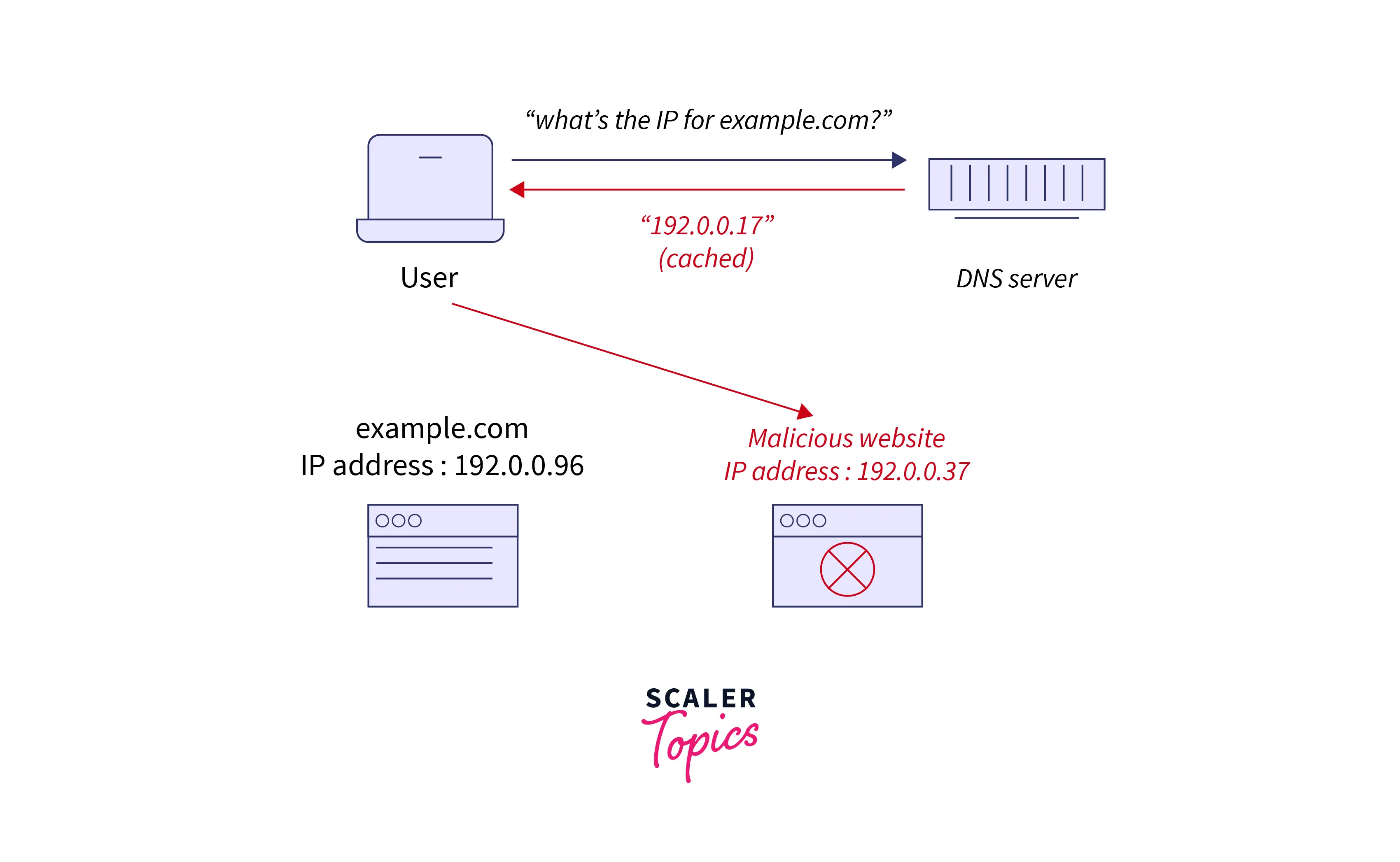
Alternatively, using TCP protocol, which needs each transmitting party to execute a ‘handshake’ to begin communication and confirm the recognition of the devices, DNS appeals, and reactions, use UDP(User Datagram Protocol).
With UDP, there is no assurance that interconnection is open, that the recipient is prepared to accept, or that the sender is who they say they are. UDP is susceptible to shaping for this reason – an attacker can dispatch a message via UDP and act as if it’s an answer from an authorized server by casting the header information.
If a DNS resolver accepts a forged reaction, it collects and caches the information uncritically. As a result, there is no other path to authorize if the data is collected and comes from a trusted source. DNS was designed in the starting days of the Internet when the sole parties linked to it were colleges and analysis centers. There was no cause to expect anyone to attempt to unfold fake DNS data.
Even with these significant susceptibility factors in the DNS caching method, DNS poisoning attacks don’t seem simple. As a result, if the DNS resolver will indeed query the authoritative nameserver, attackers have a couple of milliseconds to send the incorrect or fake response before the genuine reply from the authoritative nameserver appears.
Attackers even have to either apprehend or guess a variety of things to hold out DNS spoofing attacks:
DNS queries don’t seem to be cached by the targeted DNS resolver so that the resolver can question the authoritative nameserver.
What port is the DNS resolver victimizing – they are accustomed to using the equivalent port for every question; however, currently, they use a unique, random port anytime.
The request ID range Which reliable nameserver will the inquiry go to? Attackers may conjointly gain access to the DNS resolver in another approach. If a poisonous party operates or gains physical access to a DNS resolver, it can additionally simply alter cached information.
In networking, a port could be a virtual purpose for transmission reception. Computers have numerous ports, every port with its port range, and for computers to communicate with each other, particular ports must be selected for certain types of communication. For example, HTTP protocols consistently go to port 80, and HTTPS always utilizes port 443.
Why is DNS Spoofing a Problem?
Because users usually fall victim to phishing in a DNS spoofing attack, it’s a warning to data privacy. The spoofed website turns on attacker goals. For instance, if an attacker needs to thieve banking data, the primary step is to search out a preferred banking website, transfer the code and styling files, and transfer it to the hostile machine utilized to hijack associations.
However, individuals who utilize the authorized website arrive at the banking domain in their browsers, opening the poisonous webpage instead. Most attackers check and certify that the spoofed website is superior; however, often, a few minor errors offer the spoofed website away. For instance, the poisonous website generally has no encryption authentication installed, so the interrelation is cleartext.
An unencrypted relation could be a clear red flag that the hosted website is not a banking website. Browsers alert clients that an interrelation is not encrypted, but several clients ignore the warning and fill in their login credentials (username and password).
Following the user’s access to the spoofed webpage, any data filled into the site, involving password, social security number, and personal contact details, is dispatched to the attacker. With sufficient stolen data, an attacker could open different accounts under the selected victim’s name or verify them into recognized funds to steal additional data or money.
Examples of DNS Spoofing Attacks
Following are several other ways attackers will execute a DNS spoofing attack. A few of the foremost general examples incorporate:
- DNS Server Accommodation
A DNS server accommodation is one of the general strategies for DNS spoofing. During this situation, an associate attacker obtains admission to the DNS server and introduces a fake DNS entry. When the faux IP address is within the system, it controls traffic far from the legitimate website to the hostile one.
A popular instance of this kind of attack occurred in 2018 once hackers came to terms with Amazon’s Route 53 DNS server and community Google DNS servers. Succeeding in acquiring access, they abruptly rerouted 1,300 IP addresses to malicious phishing websites outlined to steal client data. One of the most significant aims was the cryptocurrency webpage MyEtherWallet. Attackers dispatched clients seeking to access their virtual wallets to a phishing webpage and took around $152,000 throughout the two-attack window.
- Man-in-the-Middle (MIM) Attack
A man-in-the-middle attack is a kind of malware that spammers use to obstruct virtual traffic or information transfers and hijack vital data. To accomplish this attack, an attacker expropriates a client’s DNS appeal before it extends an authorized server and redirects to an incorrect IP address. This not barely dispatches a spoofed outcome back to the client and contaminates their system; however, it may poison the DNS server that collected the beginning request. - DNS Cache Poisoning
DNS cache poisoning is comparable to spoofing however grabs the attack one step additional by damaging a system’s DNS resolver cache. DNS resolvers are outlined to save lots of IP address feedback for a particular amount once the beginning request is, permitting them to reply to future demands much more quicker.
Hackers will poison the resolver cache by fixing keep information directly or tricking it into storing a solid response. For example, an associate assaulter might amend the keep information processing address for Twitter.com to one that results in a faux website they own. Once the user searches for Twitter.com, the resolver uses the cast information to send them to a fake website when they struggle to access it.
DNS Spoofing vs. DNS Poisoning
DNS spoofing and DNS poisoning area units are similar. However, they need distinguishable characteristics. They each trick users into divulging sensitive knowledge, which might lead to a targeted user putting in a malicious software package. Each DNS spoofing and its poisoning risks can affect user knowledge privacy and the security of a website affiliation as users communicate with servers on public Wi-Fi.
Poisoning DNS cache changes entries on resolvers or DNS servers wherever scientific discipline addresses area units. Using the poisoned DNS server’s entries will redirect any user from any location on the net to a malicious attacker-controlled website. The poisoning might affect world users counting on the poisoned server.
DNS spoofing could be a broader term that describes attacks on DNS records. Any attack that changes DNS entries that force users to access an attacker-controlled website would consider spoofing, together with poisoning entries. Spoofing could lead to a lot of direct attacks on a neighborhood network where an associate assaulter will poison the DNS records of vulnerable machines and steal knowledge from business or non-public users.
How to Prevent DNS Spoofing and Cache Poisoning?
When wanting to forestall DNS spoofing, user-end protections square measure restricted. Website owners and server suppliers square measure a small amount of additional authorization to guard themselves and their users. To suitably keep everybody safe, each party should attempt to avoid spoofs.
Here’s the way to stop for website house owners and DNS service providers:
- DNS spoofing detection tools.
- The Domain name system security extensions.
- End-to-end secret writing
Here’s the way to stop for end clients:
- Do not press on a spacious link you don’t acknowledge
- Frequently examine your pc for malware
- Blush the DNS cache to unravel poisoning
- Use a Virtual non-public Network (VPN)
Anticipation Points for Website keeper and DNS Server Distributor
As an internet site holder or DNS server distributor, the management to protect clients is absolutely in our hands. You’ll implement numerous protecting tools and protocols to hold hazards out. Throughout these given resources, you’d be smart enough to utilize a number of the following:
- DNS is spoofing perception tools: As the same as an end-user security product, these perception tools dynamically scan all information collected before delivering.
- The Domain name system security extension (DNSSEC): a DNS
certified reallabel; the DNSSEC system assists keep DNS activity original and spoof-free. - End-to-end encryption: Encrypted information dispatched for DNS feedback and answers holds criminals out as they won’t be prepared to correspond to the characteristic security guarantee for the authorized website.
Prevention Tips for End Users
Clients are significantly vulnerable to these. To disregard being a victim of a DNS poisoning attack, we ought to follow these straightforward tips:
- Do not press on a spacious link you don’t acknowledge, which includes email, text messages, or links on social media. Tools that shorten URLs will mask link destinations, avoiding the maximum amount attainable. To be particularly safe, continuously value more highly to enter an address into your address bar manually. However, solely do, once you’ve confirmed that it’s official and legit.
- Frequently examine your pc for malware Whereas you’ll not be ready to notice DNS cache poisoning, your security software package can assist you in uncovering and taking away any secondary infections. Since spoofed sites will deliver every kind of malicious program-program, you ought to continuously scan for viruses, spyware, and other hidden problems. The inverse is additionally attainable, as malware might deliver spoofs. Continuously employ a native program instead of a hosted version since poisoning might spoof web-based results.
- Blush the DNS cache to unravel poisoning. Cache poisoning stays in your system for a long time unless you clean out the infected knowledge. This method may be as straightforward as a gap in the Windows “Run” program and writing “`ipconfig /flush DNS” as your command. Mac, iOS, and automata even have flush choices. These square measures are typically found in an exceedingly “network settings reset” possibility, toggling airplane mode, via device bring-up, or in an exceedingly specific native application program address. Hunt your specific device’s methodology for steering.
- Use a Virtual non-public Network (VPN). These services provide an associated encrypted tunnel for all your network traffic and the personal DNS servers that completely use end-to-end encrypted requests. The result offers servers that square measure much more resilient against DNS spoofing and requests that can’t be interrupted.
Conclusion
- As is currently the case with most systems, your DNS will be eligible for regular system updates. Mostly, Ensuring you run these updates so you utilize the best recent version of your DNS is extraordinarily vital since these updates typically embody new security protocols and fixes to any known vulnerabilities. In addition, staying on the latest version can make sure you will still receive updates in the future.
- DNS spoofing is one of the foremost troublesome styles of cyberattacks to discover; however, there square measures many methods you’ll be able to use to guard yourself and your data. Consider putting in a reliable antivirus code or a VPN to secure your online activity and preclude the future world.
- The best detection protocols use regular observation to seem sure as shooting warning signs. Two of the most significant warning signs square measure.
- (1) a rise in DNS activity from one supply to a few single domains, which might indicate a Birthday attack, and
- (2) a rise in DNS activity from one supply regarding multiple domain names, which might indicate an attempt to search out an entry purpose for DNS poisoning.
- Another vital detection maneuver is leading user coaching to assist users in becoming aware of potential risks. Whereas DNS poisoning attacks are troublesome for even well-trained users to identify, robust coaching will facilitate stemming the unfolding of bound spells.
- Internet services can utilize DNSSEC (DNS security) to shield from DNS satirizing. When a space proprietor sets up DNS sections, DNSSEC adds a cryptographic mark to the passages expected by resolvers before they acknowledge DNS queries as accurate.