Have you ever seen http:// or https:// in a browser’s address bar while browsing a website? Both protocols allow a web server and a web browser to exchange data related to a specific website. What distinguishes these two, though? Well, https is secure since it has an extra s in it! The very short and concise answer to the question is that https is much more secure than http.
Scope
- This article discusses the difference between HTTP and HTTPS.
- This article briefly discusses HTTP and HTTPS separately.
- This article also discusses how to switch from HTTP to HTTPS.
- This article lists various advantages and disadvantages of both HTTP and HTTPS.
- This article also gives its opinion on which protocol is better, between HTTP and HTTPS.
What is HTTP?
HTTP stands for Hypertext Transfer Protocol. HTTP specifies a set of rules and standards that regulate how any information on the World Wide Web (WWW) can be transmitted. HTTP defines the standard rules by which web browsers and servers communicate.
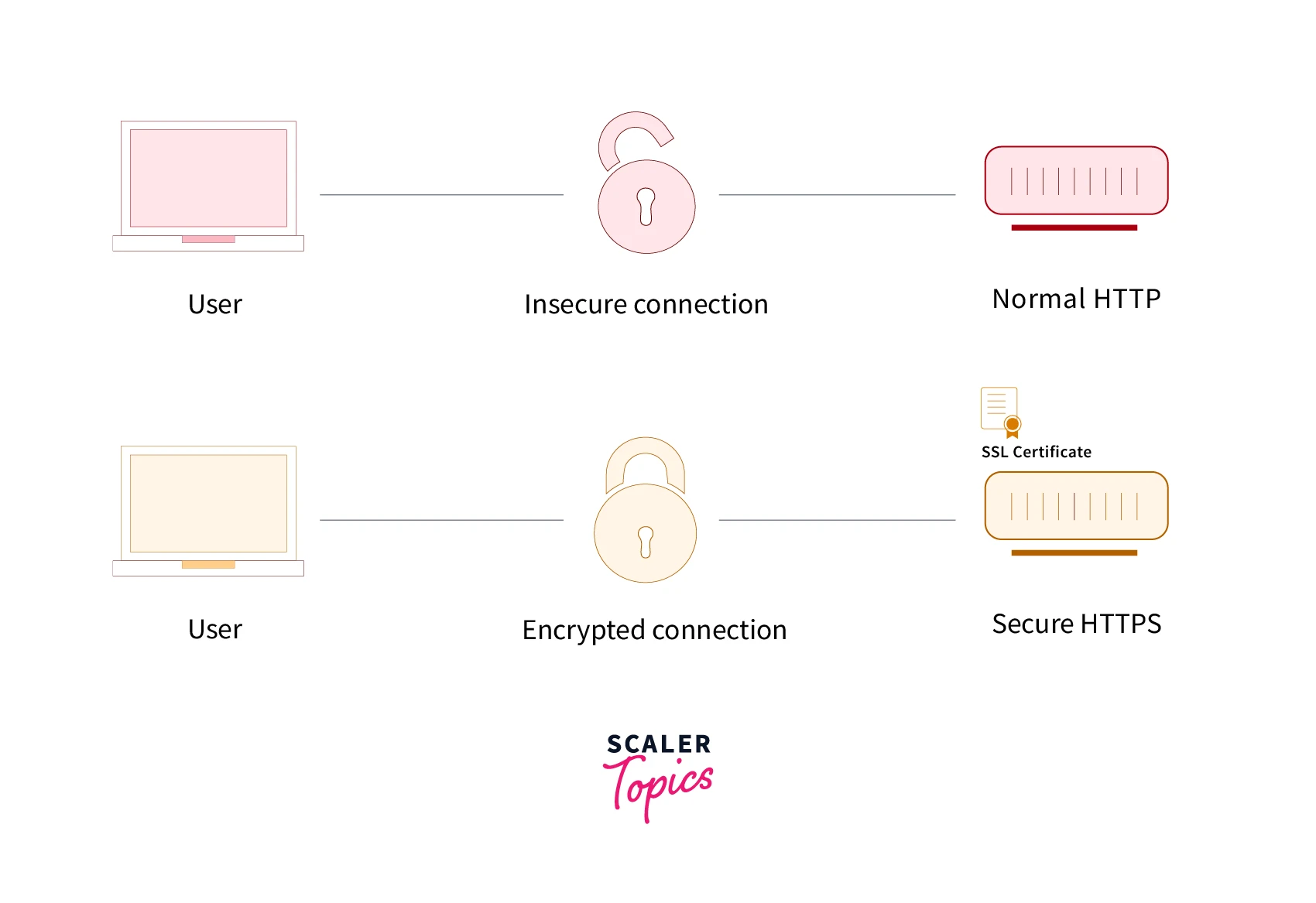
HTTP is an application layer network protocol constructed on top of TCP. HTTP employs Hypertext Structured Text to build a logical relationship between nodes holding text. HTTP (Hyper Text Transfer Protocol) is also known as a “stateless protocol” because each transaction is executed independently without having prior knowledge of the transactions. This means that once the transaction between the web browser and the server is completed, the connection is lost.
How does HTTP Work?
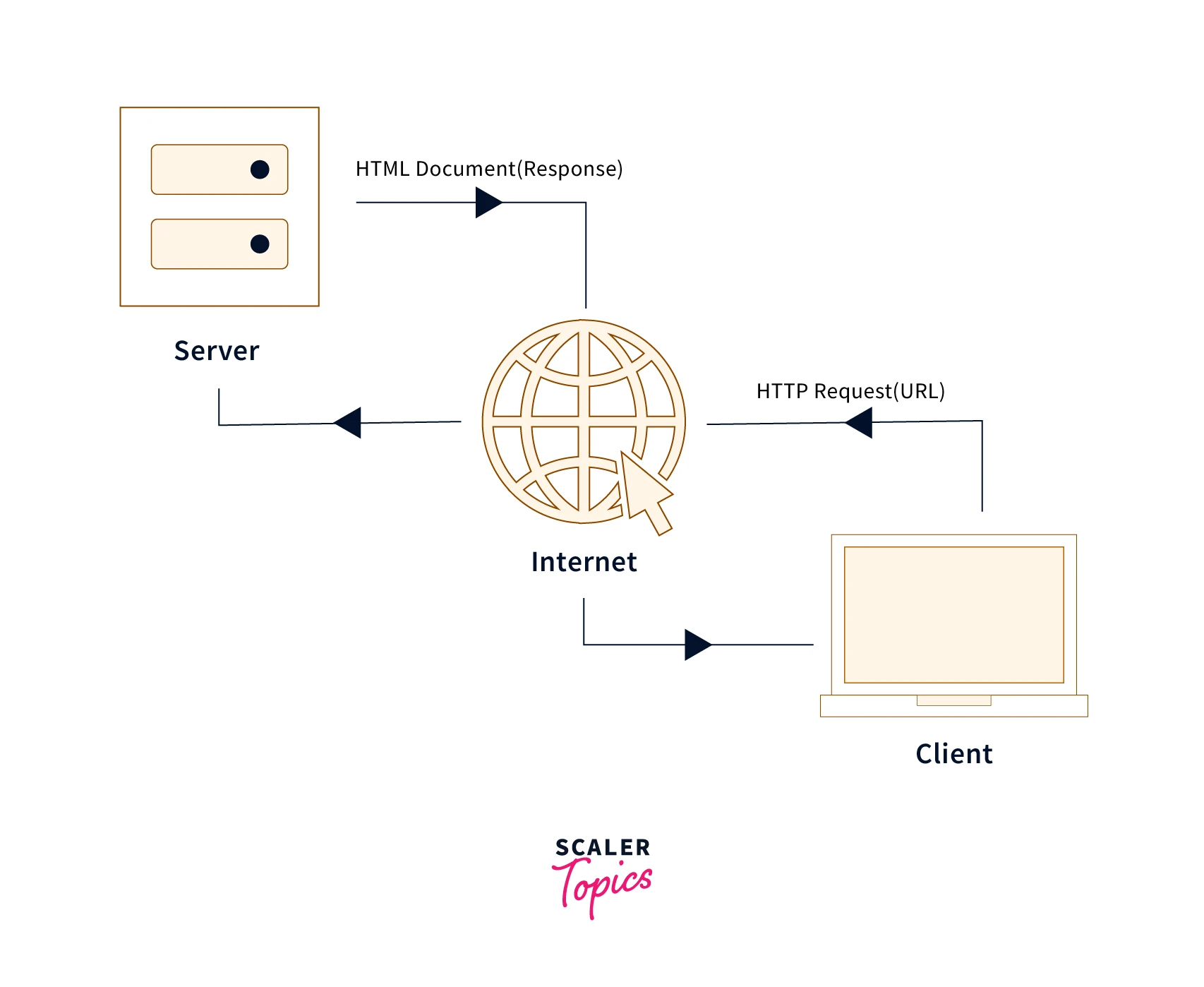
When a web user requests or interacts with a web page, their browser makes an HTTP request to the server, which hosts the website’s files. These requests are just text lines transmitted across the internet. The server then executes the request and returns an HTTP response after establishing a connection with the browser. This enables website users to access web pages.
HTTP Request/Response
As a user interacts with web resources, their browser sends HTTP requests. For instance, if a user clicks a hyperlink, their browser will send a sequence of “HTTP GET” requests to retrieve the information displayed on that page. When a user searches for “Difference between http and https” and this scaler topics article appears in the search results, their browser will create and send a sequence of HTTP requests to obtain the data required to render the page. These HTTP requests are forwarded to an origin server or a proxy caching server, producing an HTTP response. Answers to HTTP requests are known as HTTP responses.
What Does a Typical HTTP Request Look Like?
Simple lines of text that adhere to the HTTP protocol make up an HTTP request. A GET request might appear as follows:
The user’s browser creates this piece of text, which is transmitted via the internet. The issue is that information is transmitted in plaintext, meaning anyone keeping an eye on the connection can read it.
Using HTTP may become problematic, especially when consumers enter sensitive information into an untrusted website or web application. This information could be anything, such as a credit card number, a password, or any other data entered into a form. In HTTP, all this data is sent unencrypted for anybody to view. (When a user submits a form, the browser converts this into an HTTP POST request rather than an HTTP GET request.)
An origin server sends an HTTP response in response to an HTTP request, which generally looks likes:
Any user monitoring the session can view all requests and responses if a website utilizes HTTP rather than HTTPS. In essence, a malicious attacker can examine the language of a request or response to determine exactly what information is being requested, provided, or received. In this way, privacy and security are both compromised.
What is HTTPS?
HTTPS stands for Hypertext Transfer Protocol Secure. The security of the data is provided through the HTTPS protocol, not by the HTTP protocol itself. As a result, HTTPS is a secure variant of the HTTP protocol. For data communication, it employs port 443. It enables secure transactions by encrypting all connections with SSL (Secure Sockets Layer). It is a fusion of the SSL/TLS protocol and HTTP. It provides encrypted and secure network server identification.
| $HTTPS = HTTP + SSL$ |
|---|
HTTP also establishes a secure encrypted connection between the server and the browser. It provides data security in both directions. This assists you in preventing the theft of potentially sensitive information. Transport Layer Security (TLS), often known as a Secure Sockets Layer (SSL), is the encryption protocol used by HTTPS. This protocol utilizes an asymmetric public key infrastructure mechanism and employs the two distinct keys listed below:
- Private Key:- This key is accessible via the web server, which the website’s owner administers. It decrypts information that has been encrypted with the public key.
- Public Key:- Everyone has access to this key. It changes the data to an encrypted format.
TLS (Transport Layer Security) is simply a more secure, updated version of SSL. We generally refer to our security certificates as SSL because it is a more commonly used term.
To understand HTTPS better, let’s take an example.
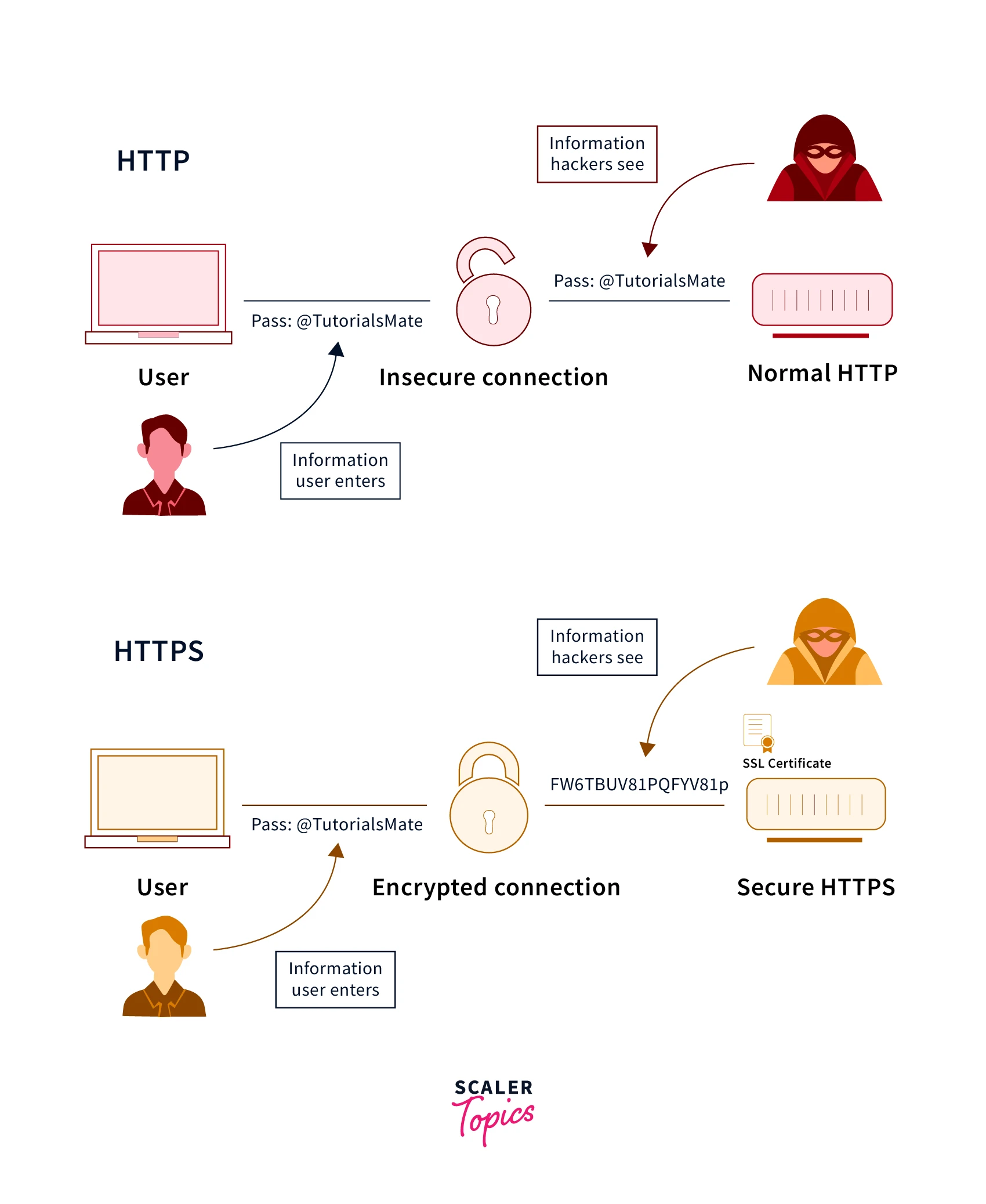
Suppose we search for scaler.com. If a user uses HTTP, then the attacker monitoring the session can easily see the entire content. But in case he utilizes the HTTPS, then the attacker will see some hashed encrypted code like:
Fw6T8UV81pQfyV81pIn HTTPS, How does TLS/SSL Encrypt HTTP Requests and Responses?
Public key cryptography is a technique used by TLS to enhance security. It consists of two public and private keys, with the public key being distributed to client devices via the server’s SSL certificate. The client and server use the public and private keys to agree on new session keys to encrypt further communications once the client and server establish a connection.
Then, using these session keys, all HTTP requests and responses are encrypted so that anyone intercepting communications can only see a hashed code or random string of characters rather than the plaintext.
TLS encrypts data transferred over the internet so that eavesdroppers and hackers cannot see what you send, which is especially beneficial for private and sensitive information like passwords, credit card numbers, and personal communications.
Types of SSL/TLS Certificates Used with HTTPS
Generally, there are five types of SSL/TLS certificates used with HTTPS, and these are as follows:
- Domain validation:- Typically, domain validation verifies the authenticity of the individual. This confirms that the applicant for the certificate actually owns the domain. It may take a few minutes to many hours to complete this validation.
- Organization Validation:- Organization validation, often known as a certification authority, confirms domain ownership and identifies the owners. This implies that an owner can be requested to present personal identification documents as confirmation of identity.
- Extended Validation:- The highest level of validation is referred to as extended validation. This covers domain ownership, confirming the identity of the owner, and checking the validity of business registration paperwork.
- Wildcard:- A wildcard certificate should be used for the best protection of all first-level subdomains, such as blog.domain.com or offer.domain.com. A website’s subdomains are protected by wildcard in addition to the validations mentioned above.
- Multi-Domain:- An SSL certificate helps safeguard several domains. For instance, if we need to secure several domains, we can get this kind of certificate, ultimately reducing the cost of purchasing a certificate for each site.
How does HTTPS Help Authenticate Web Servers?
Authentication is the process of confirming that a person or computer is who they claim to be. HTTP is based on the idea of trust rather than identity verification. The creators of HTTP had concerns other than security at the time and did not consciously decide to trust all web servers implicitly. But authentication is crucial on the modern internet.
A private key certifies server identity in the same way as an ID card does for an individual. When a client establishes a channel with an origin server (for example, when a user navigates to a website), possession of the private key that corresponds to the public key in the SSL certificate of the website proves that the server is the authentic host of the website. Several attacks that could occur in the absence of authentication are prevented or helped to block by this, including:
- BGP hijacking
- Domain spoofing
- On-path attacks
- DNS hijacking
The certificate authority who issued the SSL certificate also digitally signs it. This demonstrates that the server is indeed who it seems to be.
HTTP vs HTTPS: Detailed Comparison
Let’s have a look at the detailed comparison between HTTP and HTTPS in tabular form:
| Basis of Comparison | HTTP | HTTPS |
|---|---|---|
| Full form | HTTP stands for Hyper Text Transfer Protocol. | HTTPS stands for Hyper Text Transfer Protocol Secure. |
| Format | In a web browser, it is written as http://. | In a web browser, it is written as https://. |
| Definition | HTTP is recognized as the World Wide Web’s (WWWs) foundation for data transfer. | HTTPS is simply HTTP with additional security certificates that enable data transmission on the internet to be more secure. |
| Port number | HTTP uses port number 80 by default for data transmission. | On the other hand, HTTPS uses port number 443 by default for data communication. |
| Layer Utilization | HTTP works on the application layer. | While on the other hand, HTTPS works on the transport layer. |
| Speed | As there is significantly less computational overhead in HTTP, the websites’ speed is very fast compared to HTTPS. | Website speed is slower on HTTPS due to redirects and data encryption. However, you can utilize HTTPS to construct accelerated mobile pages (AMP), increasing website speed for smartphone and tablet viewers. |
| Security | HTTP is vulnerable to attacks such as man-in-the-middle and eavesdropping. | HTTPS is very safe as compared to HTTP. |
| SEO | HTTP webpages are not given preference by Google. | Google gives HTTPS websites precedence since they are secure. |
| Encryption/Decryption | In HTTP, plain text is sent, which can be accessible by hackers. There is no encryption of the data. | In HTTPS, we send encrypted data that hackers cannot decipher. Encryption and decryption are utilized in HTTPS websites, which makes them safe and reliable. |
| Application | It is more suited for information-consuming websites, such as personal blogs or portfolios. | It’s ideal for websites that collect sensitive information like credit/debit card numbers, personal information, banking applications, and so on. |
HTTP or HTTPS, Which is Better?
There is no doubt that HTTPS has several benefits, which somehow puts it above HTTP in terms of which protocol is superior. But somehow, who doesn’t want their website to be as secure as possible? Who wouldn’t want to win over their users’ trust?
The fact is that taking sensitive information from users requires HTTPS, which is a requirement on its own. The following are some other ways that HTTPS is superior to HTTP:
- HTTPS allows you to implement a web push notifications service.
- It improves website rankings, as HTTPS is important for SEO.
- HTTPS makes you eligible for developing
progressive web apps (PWA), which help in turning a website into a play store mobile app for Android.
Things We Should Know Before Switching from HTTP to HTTPS
Although adopting HTTPS over HTTP has several benefits, if the transition from HTTP to HTTPS is not done properly, there may be some problems. The process typically includes the four steps listed below:
- Purchasing an SSL certificate from a reliable Certificate Authority.
- Installing on a hosting account for a website.
- Make changes to the root’s .htaccess file to configure 301 redirects.
- Make changes to the
robots.txtfile and notify the search engines folder.
Robots.txt is a text file located in the root directory of a website that describes which website pages and files you want (or do not want) search engine crawlers and spiders to visit. Usually, website owners desire to be found by search engines; however, there are instances when this is unnecessary. For example, if you keep sensitive data or wish to save bandwidth by not indexing (excluding heavy pages with images).
The procedure described above is a little challenging, even though it sounds simple. Nowadays, many hosting providers provide SSL certificate configuration in their services, which may be a preferable choice. There are other expenses, though. When moving to HTTPS, you should put the following practices into practice:
- Notify Google of your HTTP to HTTPS transition.
- For all resources, use relative URLs.
- To enable Google to crawl HTTPS-based websites, make sure that the HTTPS site is reachable through
robots.txt. - Track changes both before and after switching from HTTP to HTTPS.
How to Switch From HTTP to HTTPS?
Now let’s look at the steps to switch from HTTP to HTTPS. The control panel for your hosting account allows you to do this.
- Log in to your account using login credentials and go to the hPanel. Scroll to the Advanced section and select SSL.
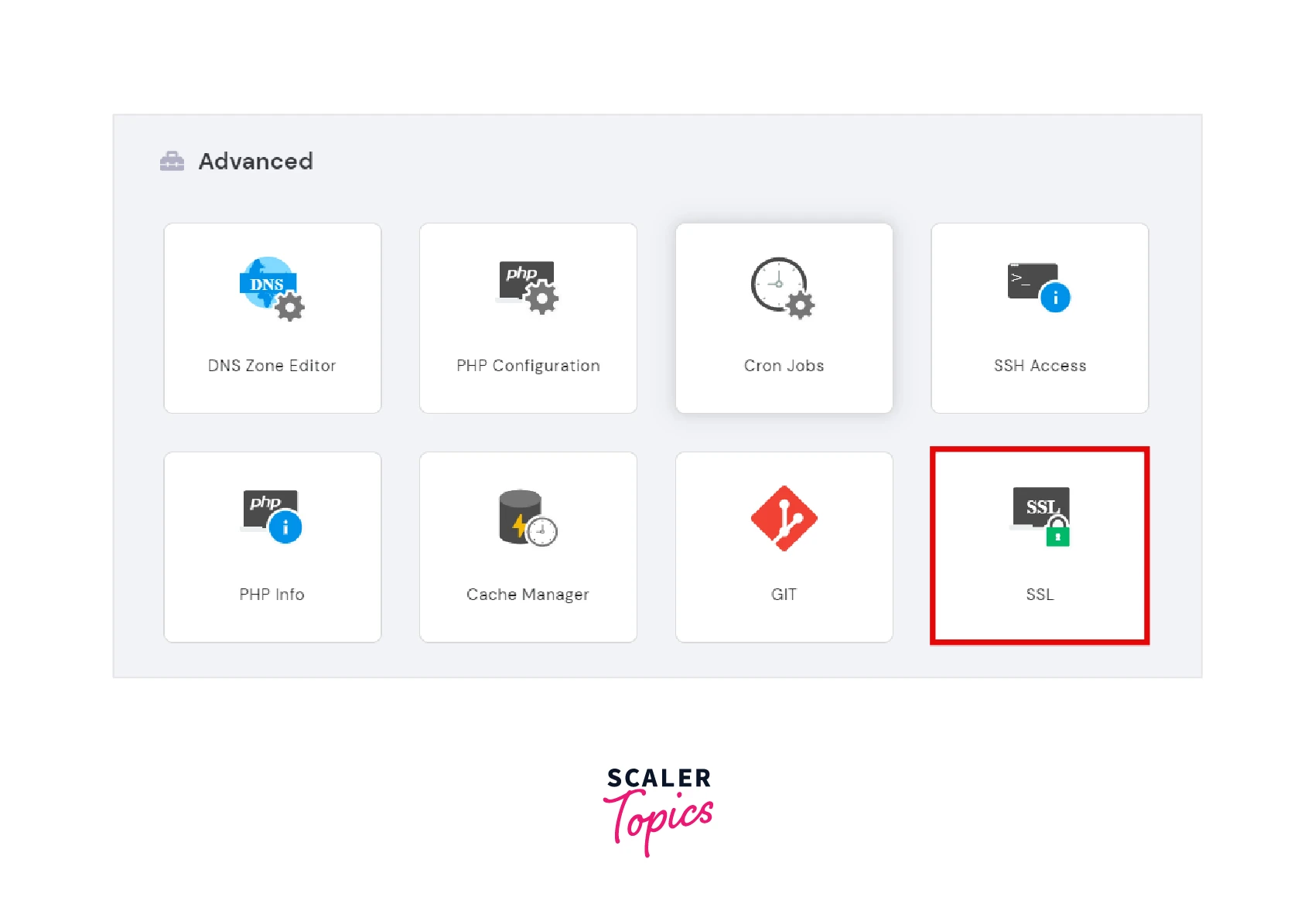
- Check that the certificate’s status is active, then click the Force HTTPS button.
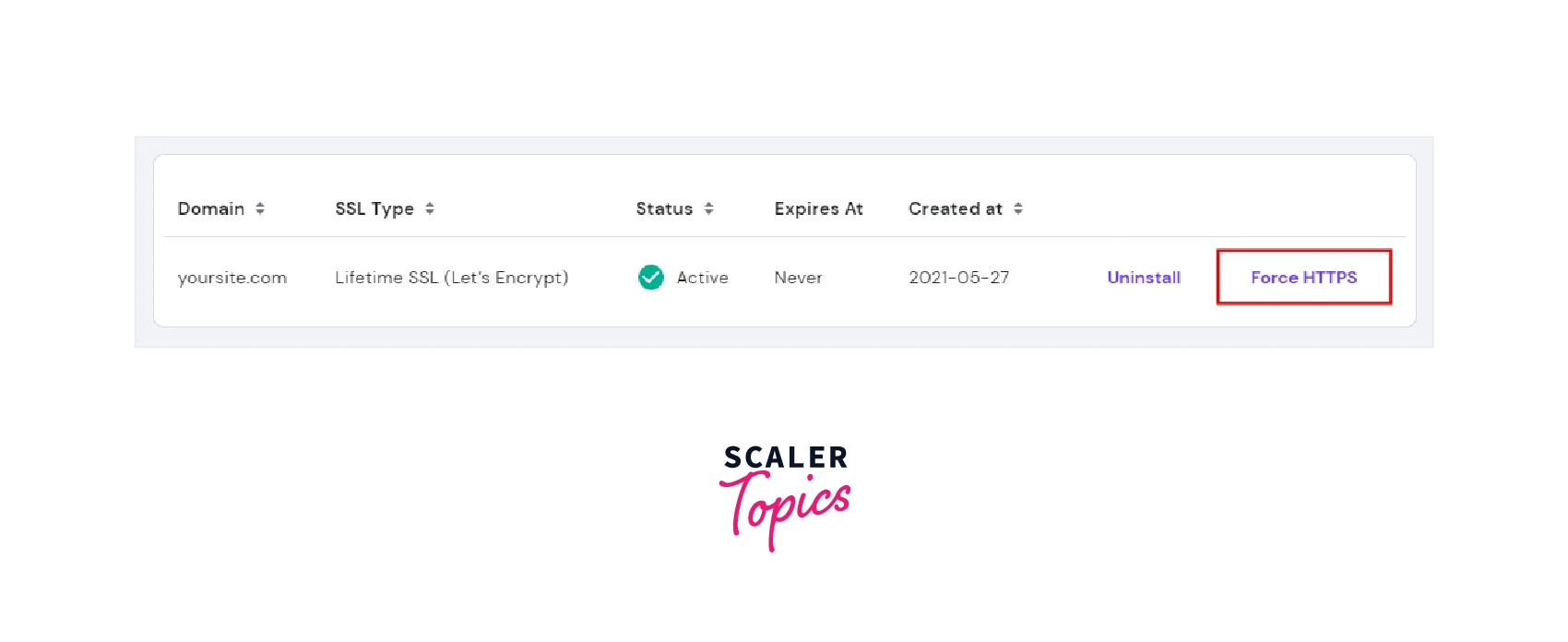
- Wait for the success message to display.
Advantages of HTTP
- Addressing:- Advanced addressing is used by HTTP. It assigns IP addresses to computers with names that are easily recognized on the World Wide Web. Compared to the traditional technique of assigning an IP address with a series of digits, this allows the general public to connect to the internet simply.
- Accessibility:- When any website is loaded for the first time, all HTTP pages get stored in the internet caches, known as the page cache. As a result, the content loads swiftly when the page is revisited.
- Security:- Each file in HTTP is downloaded from a separate connection and then closed. As a result, no more than one webpage element is transferred. As a result, the possibility of interception during transmission is reduced.
- Flexibility:- When an application requires more capabilities, HTTP can download extensions or plugins and display the necessary information. Acrobat Reader and Flash players are examples of this.
- Latency:- The handshaking process in HTTP will begin only after the connection is established. So, there will be no handshaking procedure in response to a request. This drastically minimizes connection latency.
Disadvantages of HTTP
- There is no privacy because anybody can view content.
- Data integrity is a significant concern because unauthorized users can alter the content. As a result, the HTTP protocol is insecure because no encryption mechanisms are used.
- It’s unclear who you’re referring to. Anyone who intercepts the request can obtain the password and login credentials.
Advantages of HTTPS
- Reliability:- Visitors can always trust that a website is security-conscious because of the green padlock that shows on the URL. Customers are more likely to transact when the site is reliable.
- Encryption:- One of the key benefits of HTTPS is its data encryption. Data transmitted over HTTPS is always encrypted. The information is, therefore, extremely safe. Even if the hackers succeed in obtaining those details, they will be unable to use them because the data has already been encrypted.
- Verification:- A certificate ensures that their policies and website policies are always consistent. If not, users will be informed that the connection is unsafe. As a result, if you utilize HTTPS, users may ensure that their data is transferred to the correct location and not to any unauthorized sites. This fosters trust among prospective customers who are attempting to transact business online.
- Data Validation:- Through handshaking, HTTPS performs the data validation process. All data transfers and their constituents, such as the sender and receiver, are verified. The data transfer happens only after the validations are successful. If not, the processes are terminated.
- Protection:- In contrast to HTTP, which saves data on the client system, HTTPS does not save any user data on the client system. Therefore, there is no chance of data theft in a public area.
- Search Engine Optimisation (SEO):- One of Google’s ranking signals is having an HTTPS connection. A website with an HTTPS certificate will be ranked higher than one without. Sites that frequently deal with passwords, usernames, and money transactions tend to choose HTTPS.
Disadvantages of HTTPS
- Performance:- Many computations are necessary to encrypt and decrypt data over HTTPS connections. As a result, the website’s speed is decreased due to the delayed response time.
- Cost:- You must get an SSL certificate when you switch to HTTPS. Although the website hosting provider issues multiple SSL certificates, they must be renewed annually for an annual fee. Other than that, there are ways to obtain a free SSL certificate, but it is not advised for security reasons.
- Computational Overhead:- Additional computing overheads are generated from servers and browsers due to the work involved in encrypting and decrypting data. Although a connection setup produces additional latency, these overheads are typically not noticeable. However, this can become a problem if your HTTPS connection manages several HTTPS connections at once.
- Accessibility:- Some proxy and firewall systems prevent users from accessing HTTPS websites. This can be both purposeful and unintentional. The admins might have forgotten to set up HTTPS access if it wasn’t intentional. This can sometimes be intentionally done as a security measure.
Conclusion
- HTTP stands for
Hypertext Transfer Protocol. HTTP specifies a set of rules and standards that regulate how any information on theWorld Wide Web (WWW)can be transmitted. HTTP (Hyper Text Transfer Protocol)is also known as a “stateless protocol” because each transaction is executed independently without having prior knowledge of the transactions.- HTTPS stands for
Hypertext Transfer Protocol Secure. The security of the data is provided through the HTTPS protocol, not by the HTTP protocol itself. As a result, HTTPS is a secure variant of the HTTP protocol. Transport Layer Security (TLS), often known as aSecure Sockets Layer (SSL), is the encryption protocol used by HTTPS.- HTTPS utilizes an asymmetric public key infrastructure mechanism and employs the two distinct keys listed below:
- Public Key
- Private Key
- There are five types of SSL/TLS certificates used with HTTPS, and these are as follows:
- Domain validation
- Organization Validation
- Extended Validation
- Wildcard
- Multi-Domain
- There is no doubt that HTTPS has a number of benefits, which somehow puts it above HTTP in terms of which protocol is superior. So after this article, we can conclude that HTTPS is way better than HTTP.
