Access Control Lists (ACLs) are a collection of permit-and-deny restrictions, also known as rules, that offer security by preventing unauthorized users from accessing particular resources and granting authorized users access. Additionally, ACLs can govern traffic flow, limit the information in routing updates, and determine which types of traffic are sent or denied. ACLs often sit in a router that acts as a firewall or a router that connects two internal networks.
:::
:::section{.scope}
Scope
- This article discusses Access Control List in detail with its various features.
- This article also discusses the various Access Contol lists (ACLs) types.
- This article covers various points related to ACLs, such as components of ACLs, how to implement them, Configuring Access Control Lists, and rules for ACLs.
- This article compares Linux ACL with Windows ACL.
- This article also compares RBAC (Role Based Access Control) with ACL.
- This article also lists various advantages and limitations of ACL.
:::
:::section{.main}
What is an Access Control List (ACL)?
The term “access-list” refers to a set of rules for managing network traffic and mitigating network threats. ACLs filter network traffic based on a set of rules defined for incoming or outgoing traffic. Access control lists are also installed in routers and switches, where they function as filters to govern which traffic is allowed access to the network.
A security attribute on each system resource identifies the access control list for that resource. Every person who has access to the system has a place on the list. The most typical privileges for a file system ACL are the ability to read a file or all the files in a directory, write to the file or files, and run if the file is executable or program it. Network interfaces and operating systems (OSes), such as Linux and Windows, are likewise equipped with ACLs. Access control lists are used to either forbid or permit specific types of traffic on the network. They frequently distinguish between traffic based on its source and destination.
ACLs were initially the only means of achieving firewall security. Today, there are many different kinds of firewalls and ACL substitutes. Organizations nevertheless continue to utilize ACLs in conjunction with technologies like virtual private networks (VPNs), which let users choose which traffic should be encrypted and sent over a VPN tunnel.
Features of Access Control Lists(ACLs)
- The defined set of rules is matched line by line, starting with the first line, then the second, then the third, and so on.
- The packets are only matched until they match the rule. Once a rule matches, no additional comparisons are made, and the rule is executed.
- Every ACL includes an implicit denial, meaning that the packet is discarded if no condition or rule matches.
Once the ACL is built then, it should be applied to the interface’s inbound or outbound traffic:
- Inbound Access Lists:- When an access list is applied to an interface’s inbound packets, the packets are processed according to the access list before being routed to the outward interface.
- Outbound Access Lists:- When an access list is applied to an interface’s outbound packets, the packet is routed before being processed at the outbound interface.
:::
:::section{.main}
Use of Access Control List
- Access control lists are used to manage access rights to a computer network or system. They control the flow of data into and out of a particular device. They could be endpoint devices that users access directly or network devices that serve as network gateways.
- Depending on their function, various users have varied levels of privilege on a computer system. For instance, a user who is logged in as the network administrator may have read, write, and edit permissions for a sensitive file or other resources. On the other hand, a guest user might just have read permissions.
- To increase network efficiency and give network managers more precise control over users on their computer systems and networks, access control lists can help organize traffic. ACLs can be used to block malicious traffic and hence increase network security.
:::
:::section{.main}
How Does Access Control List Work?
Each ACL contains one or more access control entries (ACEs), each containing a user’s name or group of users. A role name, such as programmer or tester, can also be used for the user. The access privileges for each user, group, or role are specified in a string of bits known as an access mask. The access control list for an item is typically created by the system administrator or the object owner.
ACL-enabled routers and switches act like packet filters, transferring or denying packets based on filtering criteria. As a Layer 3 device, a packet-filtering router utilizes rules to determine whether traffic should be allowed or denied access. It decides this based on the source and destination IP addresses, the destination and source ports, and the packet’s official procedure.
:::
:::section{.main}
Types of Access Control List
Generally, there are two types of Acess Control Lists (ACL), and they are as follows:
- Standard Access List:- These are the Access lists created solely with the originating IP address. These ACLs allow or deny access to the whole protocol suite. They make no distinction between IP traffic types such as
TCP,UDP,HTTPS, and so on. The router will recognise numbers1-99or1300-1999as a standard ACL and the given address as the source IP address. - Extended Access List:- These ACLs use the source IP, the destination IP, the source port, and the destination port. We can specify which IP traffic should be allowed or refused using these ACLs. Their use ranges are
100-199and2000-2699.
There are two more categories of ACL:
- Numbered Access List:- These are the access lists that cannot be erased once formed, i.e., removing any rule from an Access-list is not authorized in the case of the numbered access list. If we try to remove a rule from the access list, the entire access list gets released. Both standard and extended access lists can use the numbered access list.
- Named Access List:- A name identifies an access list in this form of the access list. Unlike a numbered access list, a named access list can be deleted. These, like numbered access lists, can be combined with standard and extended access lists.
:::
:::section{.main}
Components of Access Control List
ACL entries are made up of several parts describing how the ACL handles various forms of traffic. Here are a few instances of typical ACL elements:
- Sequence Number:- The sequence number identifies the ACL entry with a specific number.
- ACL Name:- This uses a name rather than a number to identify an ACL. Some ACLs permit both letters and numbers.
- Comments:- Some routers allow you to enter comments, which you can use to give more comprehensive information.
- Statement:- You can use a wildcard mask or address to approve or disapprove a source with a statement. A wildcard mask determines which components of an IP address are determined by a system.
- Network Protocol:- This gives administrators the ability to accept or reject traffic based on a network protocol, such as
IP,TCP,User Datagram Protocol,NetBIOS, orInternet Control Message Protocol, for instance. - Source or destination:- The source or destination component specifies the destination or source IP address as a range of addresses or a single IP address. It can also accept any address.
- Log:- Some ACL devices preserve a log of objects recognized by the ACL.
- Other criteria of advanced ACLs:- With some more sophisticated ACLs, you can limit traffic based on IP precedence, type of service (ToS), or priority as determined by its Differentiated Services Code Point (DSCP). A networking architecture called DSCP enables the management and classification of network traffic.
:::
:::section{.main}
How to Implement an Access Control List?
To correctly implement ACL on your router, you must understand how traffic enters and exits it. You define the rules from the perspective of the router’s interface. This is distinct from the networks. For example, if traffic flows into a router, it also flows out of a network; hence the perspective influences how the traffic’s motion is portrayed.
An ACL must be applied to the router’s interface to serve its intended purpose. The router’s hardware determines the forwarding and routing decisions, which results in a faster operation.
When adding an ACL entry, put the source address first, followed by the destination address. When the entry is presented in this format, the router knows to read it. The source is where the traffic comes from to the “outside” of the router. The destination is the location of the data packets after they have passed through the router.
The following is the fundamental syntax for creating a standard numbered access control list on a Cisco router:
Router (config)# access-list (1300-1999) (permit | deny) source-address (source-wildcard)The parts of the syntax are explained below:
- The ACL IP number range is specified by (
1300-1999). This gives the ACL a name and specifies the type of ACL. - (
permit | deny) defines whether to allow or reject the packet. - The source IP address is specified by source-address.
- The wildcard mask is specified by (source-wildcard).
A wildcard mask instructs a router on which bits of an IP address are available for a network device to examine and see whether they match the access list.
:::
:::section{.main}
Where to Place an Access Control List?
Many administrators choose to deploy ACLs on a network’s edge routers. This allows them to filter traffic before it enters their system. To accomplish this, deploy an ACL-enabled routing device between the demilitarised zone (DMZ) and the internet. Devices like application servers, web servers, VPNs, and Domain Name System (DNS) servers may exist within the DMZ.
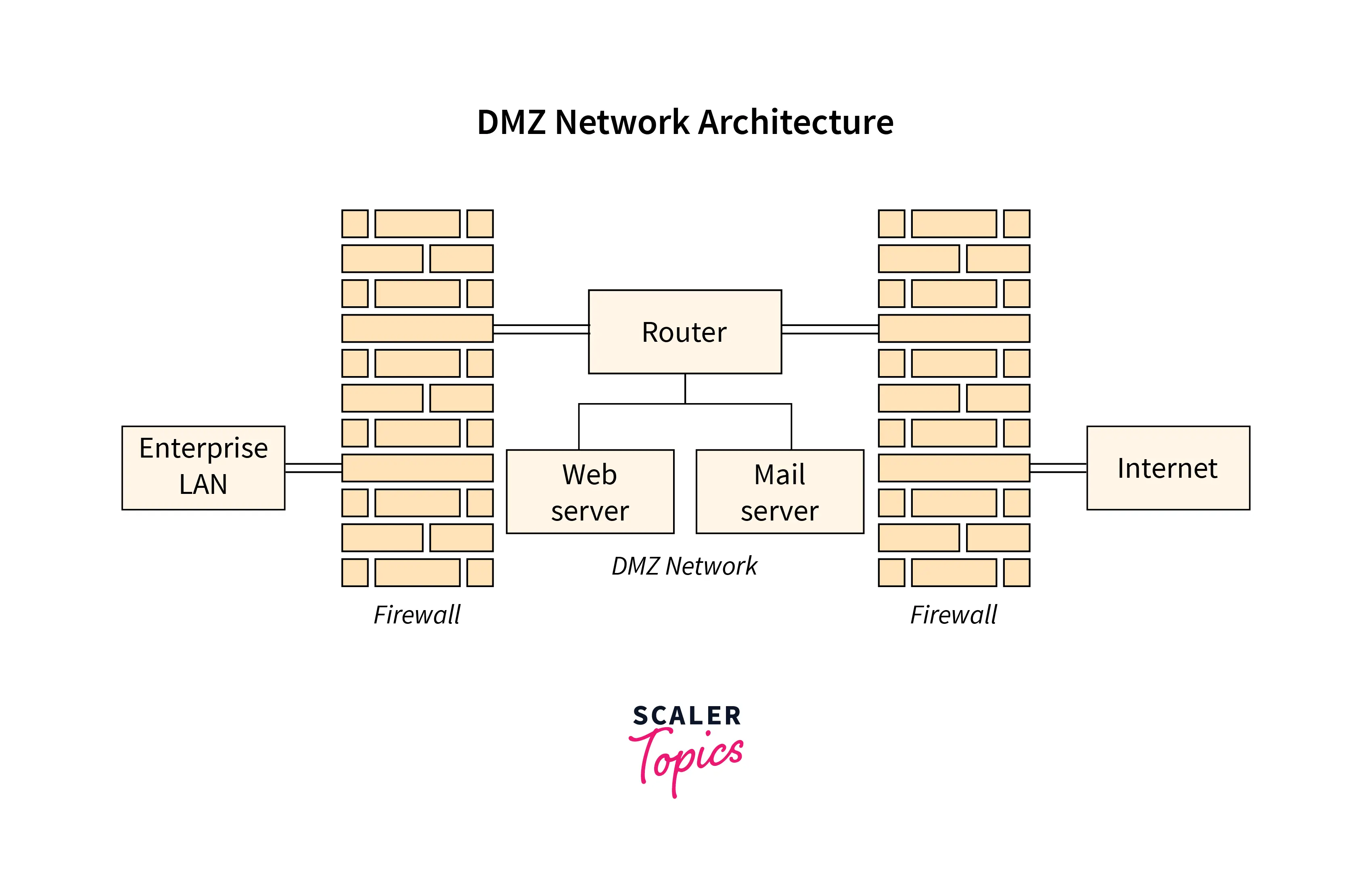
You can also put an ACL between the DMZ and the rest of your network. If you employ an ACL between the internet and the DMZ, as well as between the DMZ and the rest of your network, the configurations will be different—each setting tailored to protect the devices and users that follow after the ACL.
:::
:::section{.main}
Configuring Access Control Lists
The steps to configure Access control lists are as follows:
- Firstly create a
MAC ACLby providing a name. - Then create an
IP ACLby specifying a number. - Create new ACL rules.
- Set the match criterion for the rules.
- Finally, apply the ACL to one or more interfaces.
:::
:::section{.main}
Rules for ACL
- Generally, the standard Access list is used near the destination (but not always).
- Typically, the extended Access-list is applied near the source (but every time, it is not true).
- We are only allowed to assign one ACL per interface, protocol, and direction, meaning that each interface can only have one inbound and one outbound ACL.
- The names of extended and standard access lists cannot be the same.
- Before implementing the access lists, thoroughly analyze the entire scenario because every newly added rule will be placed at the end of the access list.
- If we are utilizing a numbered Access list, we cannot remove a rule from the list. The entire ACL will be deleted if we attempt to remove a rule. We can remove a particular rule if we’re using named access lists.
- Every access list has an implied denial at the conclusion, therefore, we need at least a permission statement there; otherwise, all traffic will be denied.
:::
:::section{.main}
ACL Best Practices
Let’s look at the few best practices to maintain tight security and the blocking of questionable traffic:
Document Your Work
Document your reasons for introducing ACL rules, their purposes, and the date you added them. A comment is not required for every rule. You have the option of providing a brief explanation for a group of rules, a detailed justification for a single rule, or a hybrid of the two. Developers should ensure the current rules are well-documented so that no one has to wonder why a rule is in place.
ACL in Order
Most often, the engine enforcing the ACL starts at the top of the list and moves its way down. This has implications for determining what an ACL will do with a particular data stream. Organizations use ACLs because they operate quickly and have less computational overhead than stateful firewalls. When attempting to provide security for quick network interfaces, this is crucial. However, the longer a packet stays in the system while being checked against the ACL rules, the poorer the performance.
The key is to place the rules you expect to be activated at the top of the ACL. Working from the broad to the specific, make sure the rules are logically organized. You should be aware that the first rule will act on each packet it triggers; you may pass a packet through one rule while intending to block it through another. Consider how you want the sequence of events to unfold, especially when adding new rules.
ACLs Everywhere
Almost all security or routing equipment enforces ACLs on every interface. This makes sense because the interfaces that make up your campus network and those that confront the outside world cannot be subject to the same rules. However, because interfaces are similar, you do not want all of them to be ACL-protected and some to be exposed. The use of an ACL on all interfaces is required for inbound ACLs, specifically the rules that determine which addresses can transfer data into your network. These are the rules that make a significant difference.
:::
:::section{.main}
Linux ACL vs. Windows ACL
- Linux allows you to modify the kernel, which Windows does not allow. However, because you can modify the kernel of Linux, you may require specialist knowledge to manage the production environment.
- Although Windows provides a reliable platform, it is not as flexible as Linux. When it comes to application integration, Windows is more straightforward than Linux.
- Microsoft is the only source that releases patches for Windows. With Linux, you have the option of using an open-source organization for patches or waiting for a patch to be released by a commercial Linux supplier.
:::
:::section{.main}
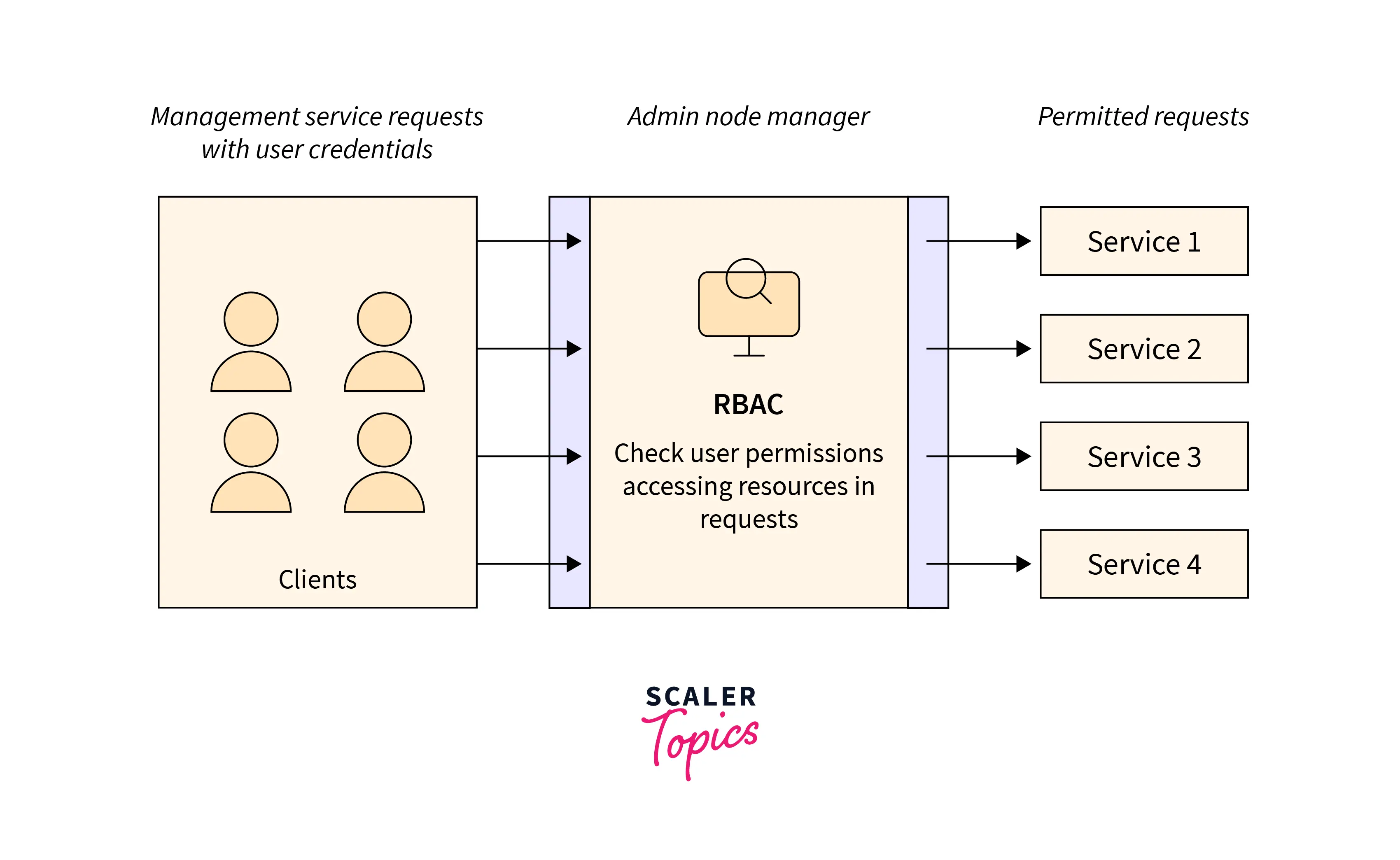
RBAC vs ACL
To handle security at a granular level, developers can employ role-based access list (RBAC) systems. Rather than emphasizing the user’s identity and determining whether or not they should be allowed to see something in the application, RBAC manages security based on the user’s role within an organization. For instance, instead of granting authorization to person X, an architect in New York, RBAC would grant permission to a position for architects in the United States. Person X could be one of several users with that job. As a result, RBAC ensures that only certain people can access critical information, as it grants all approvals based on roles.
RBAC is often regarded as the preferred method for corporate applications. In terms of administrative overhead and security, RBAC outperforms ACL. ACL is best suited for implementing security at the user level. RBAC can be used to provide a company-wide security system that an administrator monitors. For example, an ACL can grant write access to a file but cannot specify how the file might be modified.
:::
:::section{.main}
Advantages of Using ACL in Networking
- Performance:- Compared to alternative technologies that provide the same purpose, ACLs offer performance advantages. Access control lists don’t affect routing device performance because they are configured directly on the forwarding hardware of the device. In contrast, a stateful inspection firewall is a different piece of software that might result in performance reduction. Additionally, managing network traffic makes networks more effective.
- Simplified user identification:- User identification is made more accessible with an access control list. ACLs guarantee that authorized users and traffic can only access a system.
- Control over network:- By using Access Control Lists(ACLs), administrators can have more precise control over user and traffic permissions on a network at numerous points along the network. They assist in regulating traffic moving between internal networks and access to network endpoints.
:::
:::section{.main}
Limitations of ACL in Networking
Apart from the various advantages that ACL provides, it has some limitations. These limitations are platform-dependent.
- Not more than
100ACLs. - There are
8–10rules per ACL at most. - The order of the rules is critical: when a packet matches more than one rule, the first rule takes precedence. Furthermore, once an ACL is defined for a given port, all traffic not specifically permitted by the ACL is refused access.
- The system supports ACLs configured solely for inbound traffic.
MAC ACLsandIP ACLscannot be used on the same interface by the system.- You can configure the mirror or redirect properties for a specific ACL rule but not both.
- There may not be enough counter-resources supported by a hardware platform to log every ACL rule. An ACL can have an unlimited number of logging rules, but the number of actually logged rules is unknown until the ACL is applied to an interface. Furthermore, hardware counters that become accessible after an ACL is implemented are not allocated retroactively to rules that could not be logged (the ACL must be unapplied and re-applied). Rules that cannot be logged remain active in the ACL to allow or deny a matched packet.
:::
:::section{.summary}
Conclusion
- Access Control Lists (ACLs) are a collection of permit-and-deny restrictions, also known as rules, that offer security by preventing unauthorized users from accessing particular resources and granting authorized users access.
- ACLs were initially the only means of achieving firewall security. Today, there are many different kinds of firewalls and ACL substitutes.
- Generally, there are two types of Acess Control Lists (ACL):
- Standard Access List
- Extended Access List
- There are two more categories of ACL:
- Numbered Access List
- Named Access List
- Sequence Number, ACL Name, Comments, Statement, Network Protocol Source or destination and log are various components of the Access Contol List.
- To handle security at a granular level, developers can employ role-based access list (RBAC) systems. Rather than emphasizing the user’s identity and determining whether or not they should be allowed to see something in the application, RBAC manages security based on the user’s role within an organization.
- The fundamental syntax for creating a standard numbered access control list on a Cisco router:
Router (config)# access-list (1300-1999) (permit | deny) source-address (source-wildcard)