ARP stands for Address Resolution Protocol. It is a crucial communication protocol in the Internet protocol suite. It is used for discovering the data link layer address, such as a MAC (Media Access Control) address, corresponding to a given network layer address (typically IPv4). In Internet Protocol Version 6 (IPv6) networks, the functionality of ARP is provided by the Neighbor Discovery Protocol (NDP).
What is ARP Protocol?
ARP hunts the hardware address i.e. Media Access Control (MAC) address of a host machine from its known Internet Protocol (I.P.) address. ARP is implemented with several combinations of the data link and network layer technologies, such as Chaosnet, IPv4, Xerox PARC Universal Packet (PUP), DECnet, FDDI, Frame Relay, and Asynchronous Transfer Mode (ATM), X.25.
The Address Resolution Protocol is based on the request-response model, which means that Its messages are directly encapsulated by a data link layer protocol. It is never routed across internetworking nodes but instead communicated within the boundaries of a single network.
The Address Resolution Protocol uses quite a simple format of a message consisting of one address resolution response or request. The packets are propagated as raw payload at the data link layer of the underlying network. The size of the ARP message depends on the sizes of the network layer and link-layer addresses.
How does Address Resolution Protocol Work?
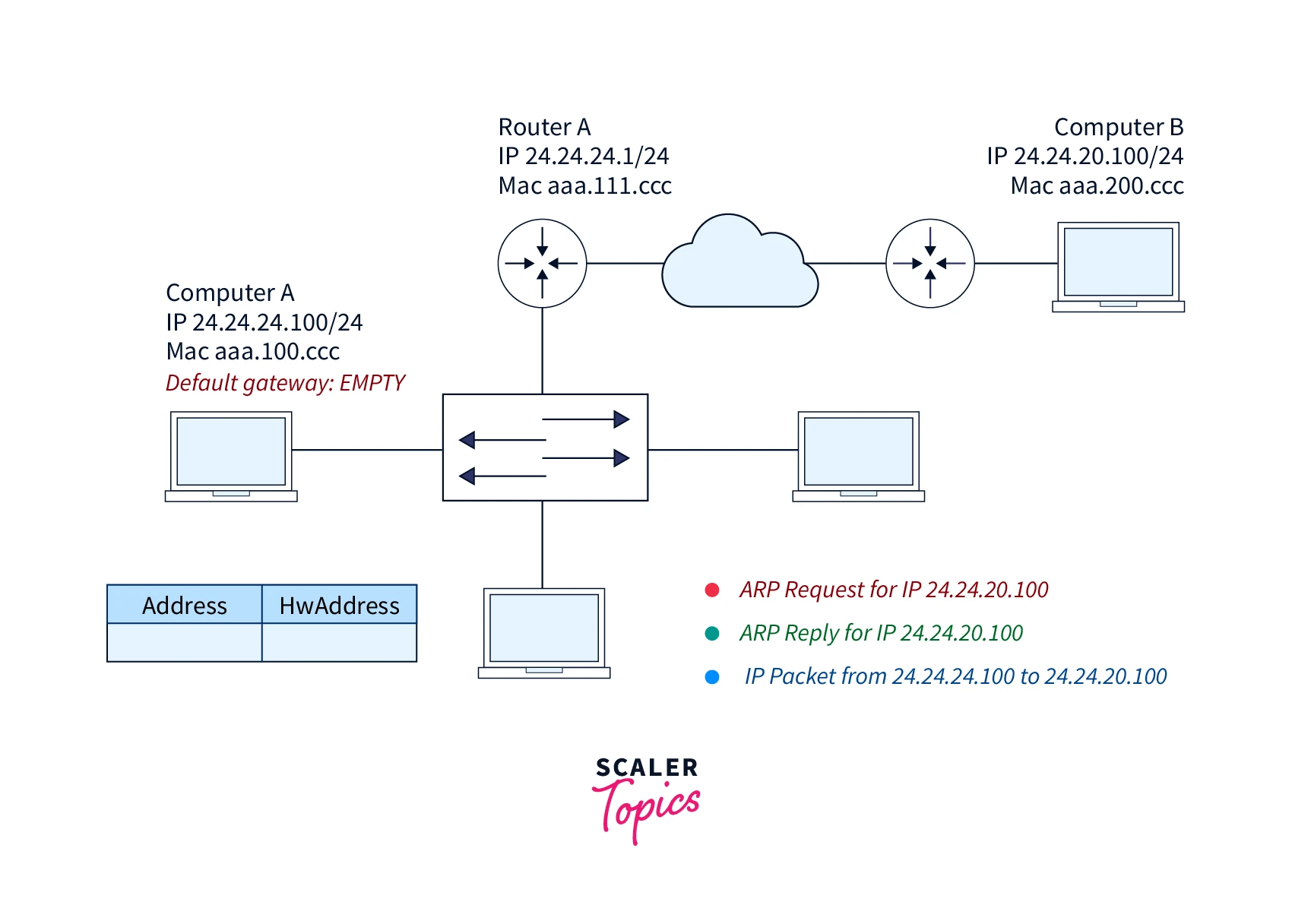
When the source at the network layer wants to find out the MAC address of the destination device it looks first for the physical MAC address in the ARP table/cache. If found, then the MAC address will be used for communication. If the physical address is not found in the ARP cache/table, then the source device will produce a message for the ARP request, in which the source specifies its own IP address and MAC address, and destination IP address. The destination MAC address remains blank since the source is trying to find it.
The source device then broadcasts the ARP request message to the Local Area Network (LAN). The broadcasted ARP request message is received by every other device on the LAN. Now all devices will compare their own IP address with the destination IP address. For any device, if both the IP addresses match, then that device is the destination device and will send an ARP Reply message. If the two IP addresses do not match, that device will simply drop the packet.
The ARP Reply message consists of the MAC address of the destination device. The destination device updates its ARP table. The destination device stores the hardware MAC address of the source because it will need to contact the source device soon. Now the source and the destination devices switch roles, i.e., the source becomes the destination and vice versa as well, and the ARP Reply message is sent.
The ARP reply message is unicasted and not broadcasted since the sender device knows the MAC address of the receiver device (initially the source device). When the destination receives the ARP reply message it comes to know about the source (previously the destination device) MAC address and it also updates its ARP cache.
ARP Packet Structure
Following are the components of the ARP packet format:
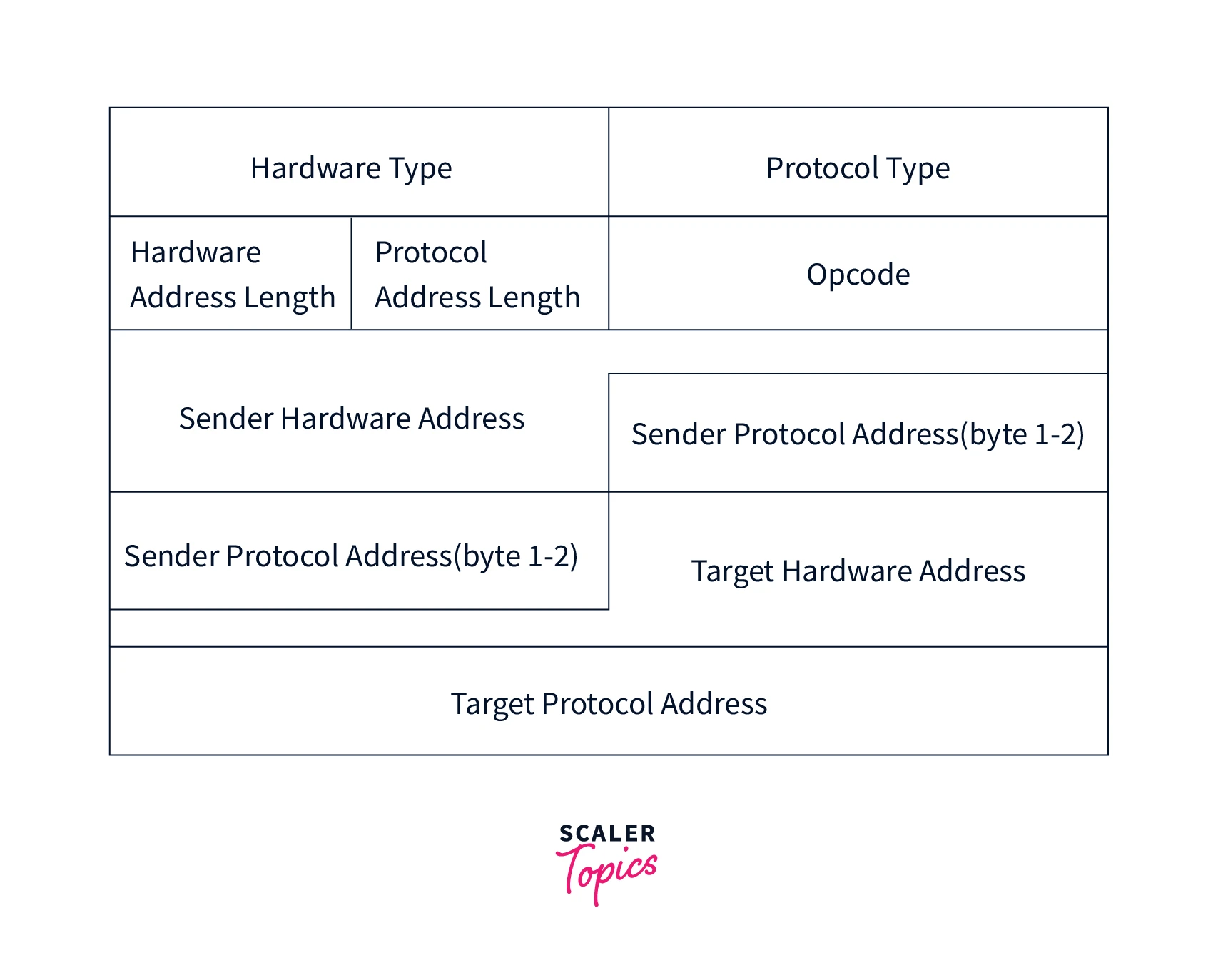
1. Hardware Type
This is for specifying the type of hardware being used in the local network to transmit the Address Resolution Protocols message.
2. Protocol Type
This field is assigned a fixed number. For an instance, IPV4 has 2048.
3. Hardware Size
This represents the length of the MAC address in bytes. For example, the ethernet has a 6 bytes long MAC address.
4. Protocol Size
It represents the length of the IPV4 logical address, which generally is 4 bytes long.
5. OpCode
This is the length of the logical address in bytes. It indicates the nature of the ARP message. An ARP reply message holds the value of 2, while an ARP Request message is assigned the value of 1.
6. Sender MAC address
The hardware MAC address of the source device.
7. Sender IP address
The network layer address of the source device.
8. Target MAC address
This field works only during the reply phase and does not hold any value during the request phase. It stores the hardware MAC address of the receiver device.
9. Target IP address
The network layer address of the receiver device.
Types of Address Resolution Protocols
Address Resolution Protocol is of the following four types:
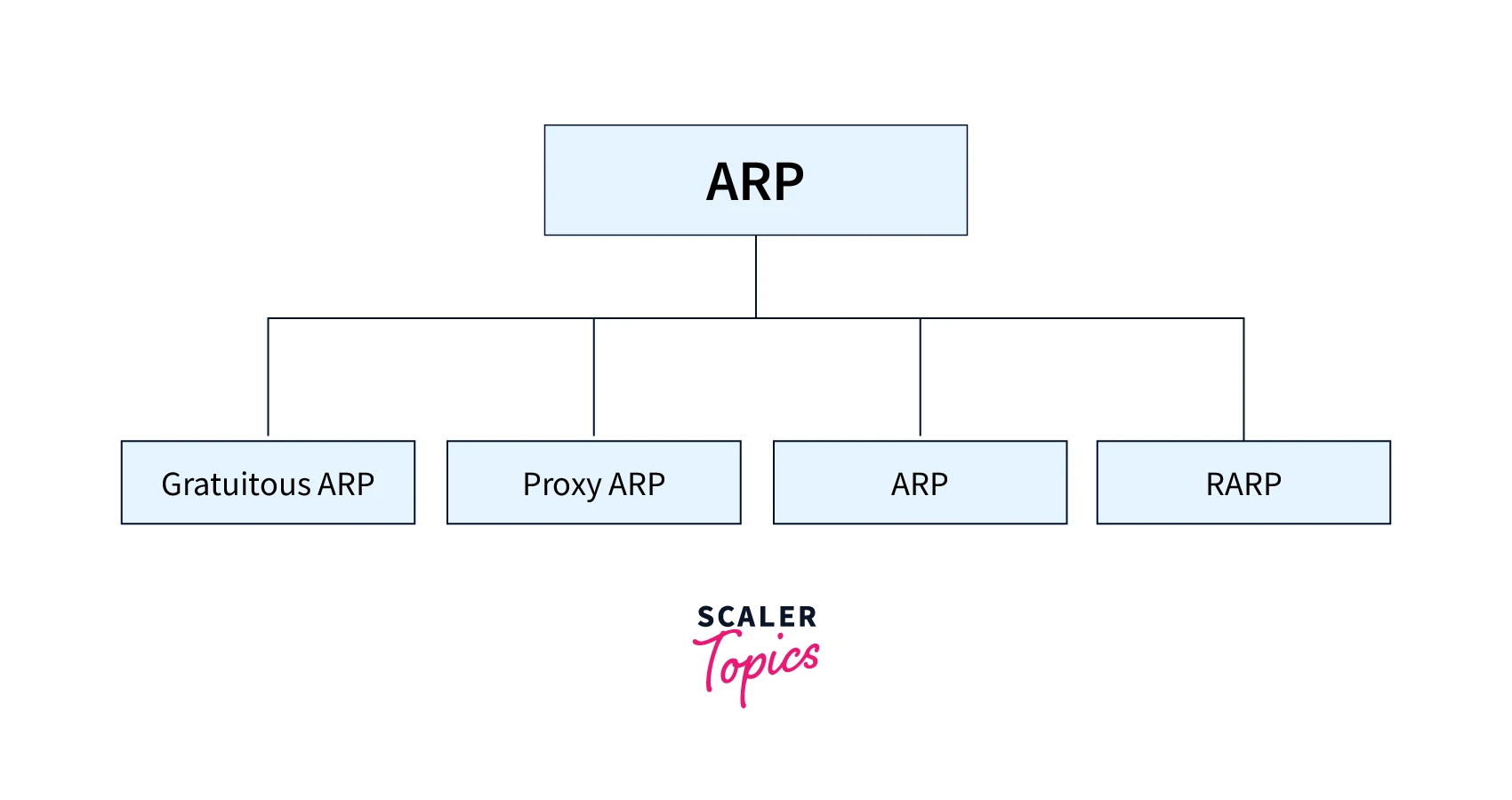
1. Proxy ARP
In Proxy ARP a layer-3 device may respond to ARP requests for a target not situated in the same network as the sender. A router configured with Proxy ARP responds to the ARP and maps the physical MAC address of the router with the target IP address and makes the sender think that it has reached its destination. In the backend, the proxy router transmits its packets to the correct destination since these packets have the required information.
As an instance, suppose a host ‘x’ wants to transmit data to another host ‘y’ not on the same network as x, then x transfers an ARP request message to obtain a MAC address for y. The router responds with its own physical MAC address to x, disguising itself as the destination. When the data is sent by x to the destination, it will transfer to the gateway so that it transmits to y. This is how proxy ARP operates.
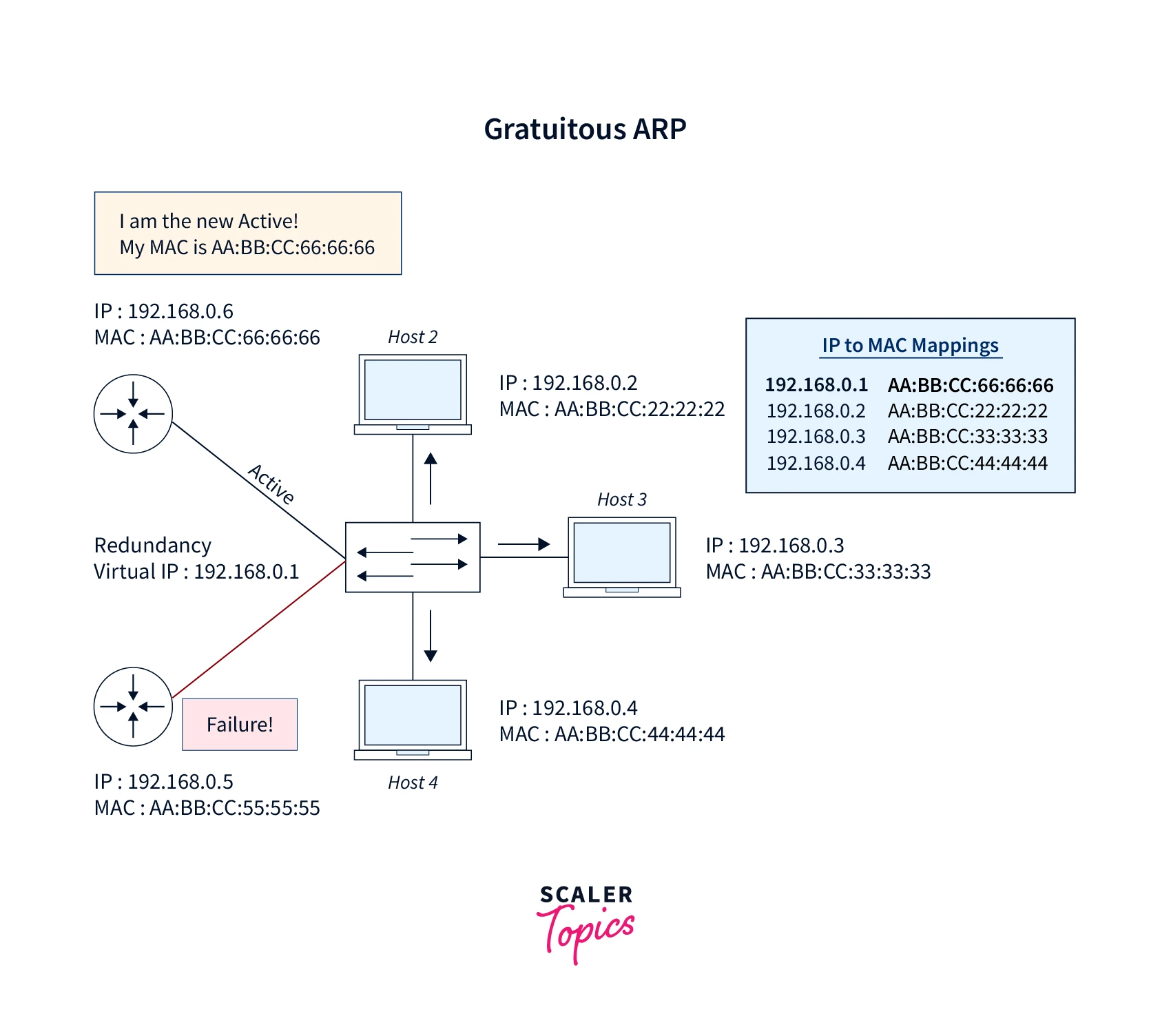
2. Gratuitous ARP
Gratuitous ARP helps in identifying duplicate IP addresses. It is a broadcasted ARP request for the router’s IP address. If a switch or router sends an ARP request to get its IP address but does not receive any ARP response, no other node will be able to use the IP address allocated to that router/switch. But still, if a switch or router transfers an ARP request for its IP address and does receive an ARP response, other nodes use the IP address allocated to the router/switch. Following are some use-cases of Gratuitous ARP:
It is used for updating the ARP cache or table of other devices.
Gratuitous ARP also checks if the host using the duplicate IP address or the original IP address
3. Reverse ARP
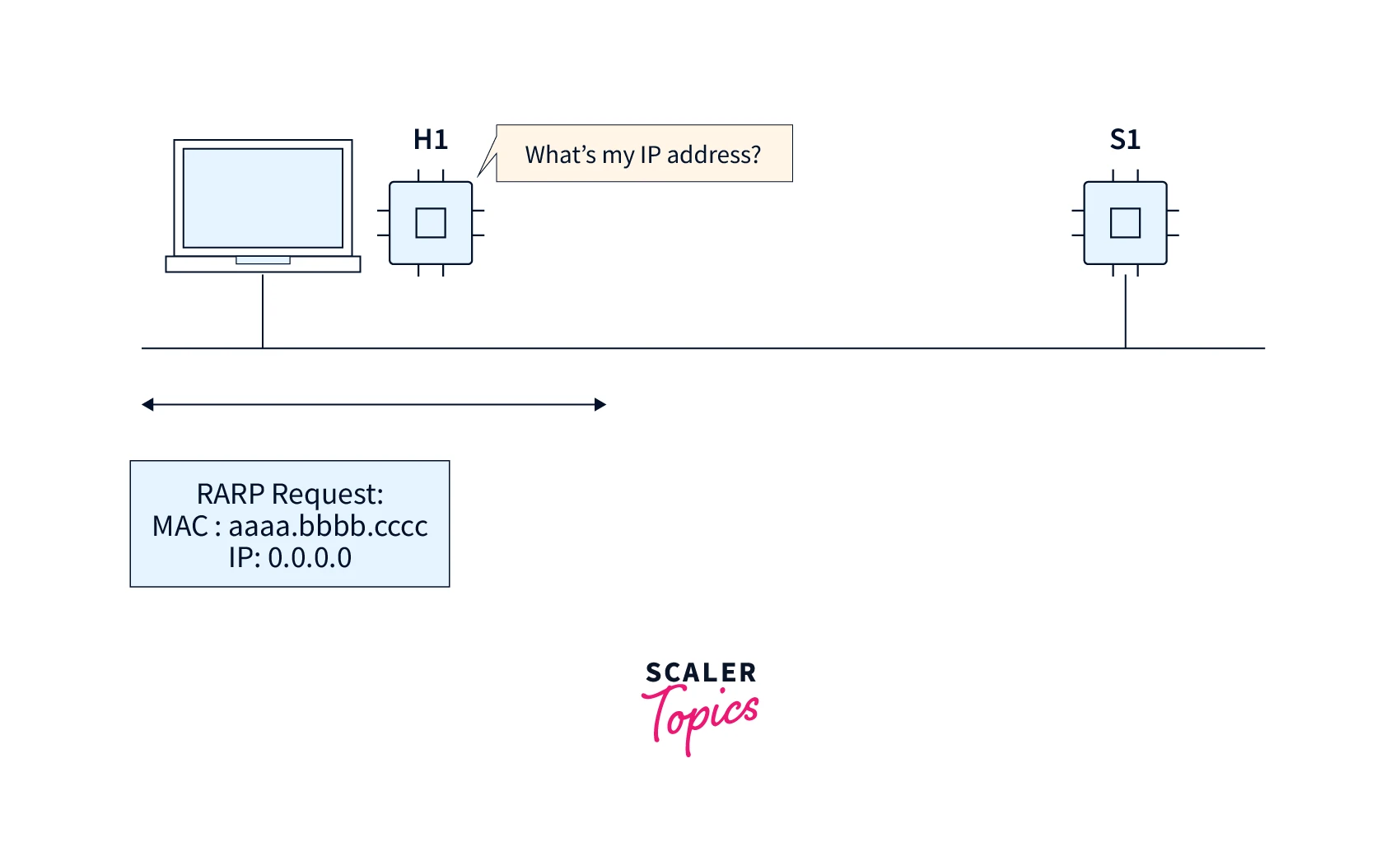
RARP is a networking protocol that a client system uses in a LAN for requesting from the ARP gateway router table, its IPv4 address. The network administrator creates a table in the gateway router which is required for obtaining the MAC address corresponding to an IP address. If a machine does not have any memory for storing the IP address (ex, a new setup system), then the user has to discover the device’s IP address.
The device broadcasts a RARP packet that includes the MAC address of the device in the address field of both the receiver as well as the sender hardware. There is present a host within the local network known as the RARP-server. It is prepared to respond to such broadcast packets. The RARP server attempts to locate a mapping table entry in the IP to MAC address. If any such entry matches the item in the table, the RARP server then transmits the response packet along with the IP address to the requesting computer.
4. Inverse ARP
IARP, as the name suggests, is and does the opposite of the ARP. It is required for finding the network layer address of a node from its data link layer address. These are primarily used for ATM networks, frame relays etc were often using Layer 2 signaling, Layer 2 virtual circuit addressing is acquired. The relevant Layer 3 addresses are available when using these virtual circuits. The packet format of IARP is similar to that of ARP, but with different operational codes.
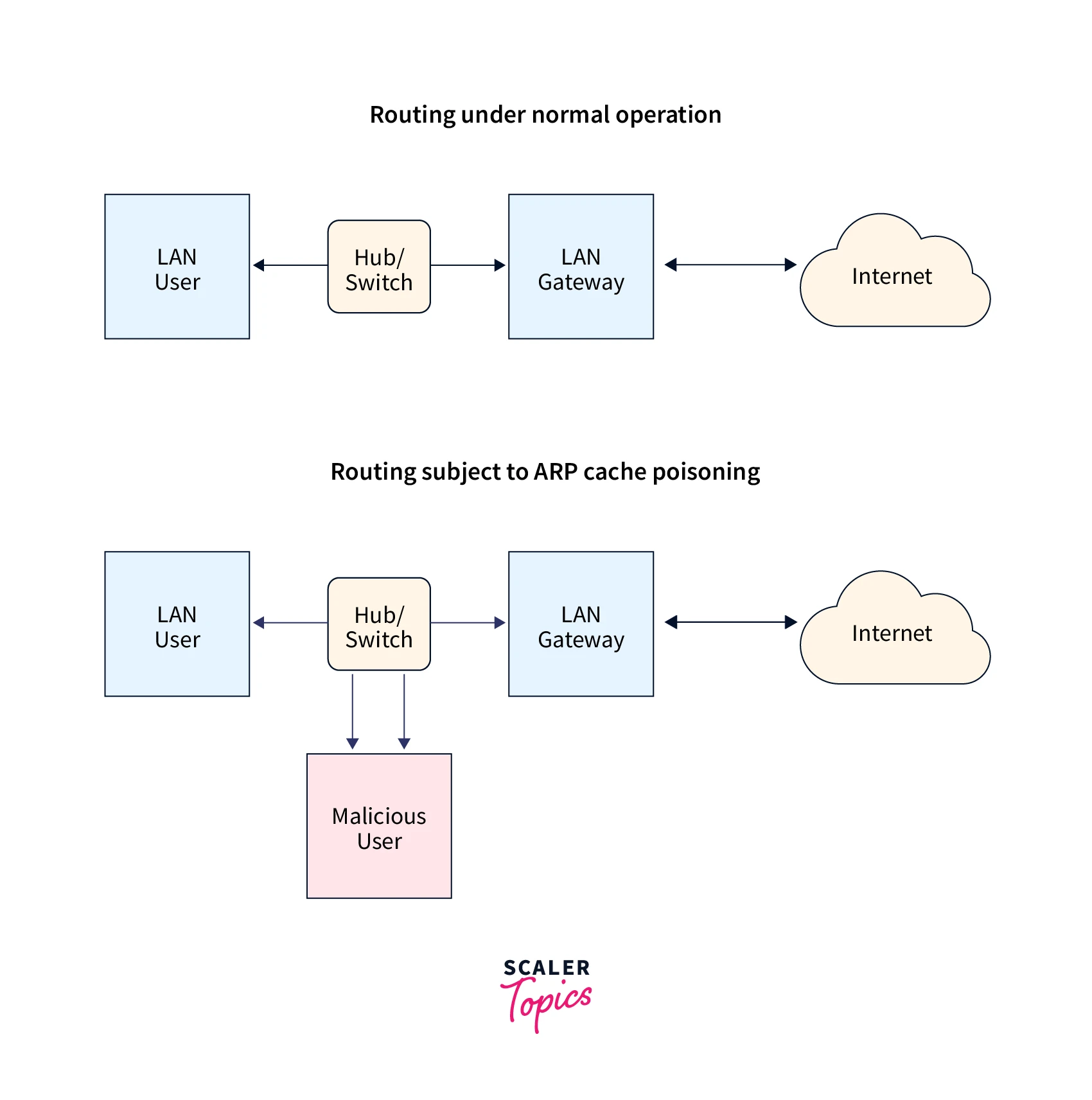
What is ARP Spoofing?
ARP spoofing is also referred to as ARP cache poisoning and ARP poison routing. It is a technique using which an attacker sends a spoofed Address Resolution Protocol message onto a LAN. Usually, the goal is to associate the MAC address with the IP address of some other host (the default gateway, etc). This leads to any traffic meant for that IP address being sent to the attacker instead.
ARP cache poisoning enables an attacker to modify the traffic, intercept data frames on a network, stop all traffic, etc. Often the ARP spoofing attacks are used as a means of opening a window for other attacks, such as man in the middle, denial of service (D.O.S.), session hijacking attacks, etc. The attack affects only networks that use ARP. Also, it is required that the attacker possesses direct access to the targeted local network segment.
How to Avoid ARP spoofing?
- Using static ARP tables.
- Taking secure managed Ethernet switches.
- Controlling physical access to the place of business.
- Isolating the network by concentrating all the important resources in a dedicated network segment.
- Encryption reduces the severe damage caused by ARP spoofing.
History and Future of ARP
The address resolution was an issue significant from the very start of the development of the TCP/IP model. A large early part of the development of IP was conducted on the then-fledgling Ethernet LAN technology (even before Ethernet was officially standardized as IEEE 802.3). It became essential to create a way to map IP addresses to Ethernet addresses for enabling communication over Ethernet networks.
There were observed two possible methods: direct mapping and dynamic resolution. But since IP addresses are only 32 bits long while Ethernet addresses are 48 bits long, thus direct mapping was immediately ruled out. Thus was developed the TCP/IP Address Resolution Protocol (ARP), which is described in one of the earliest of the Internet RFCs still in common use: RFC 826, An Ethernet Address Resolution Protocol, published in 1982.
Since ARP was genuinely developed for Ethernet, it denotes a nexus between the most popular layer three internetworking protocol and layer two LAN protocol, even today, two decades later. But it was realized that even if Ethernet was a common way of transporting IP, it may not turn out to be the only one. Thus ARP was set as the general protocol.
128 bits long IPv6 addresses use the Neighbor Discovery protocol instead of ARP, for acquiring the configuration information. Even though less common as compared to IPV4, the use of IPv6 is increasing. Neighbor Discovery works in the second layer of the OSI reference model. For discovering the neighboring nodes, it uses Internet Control Message Protocol 6.
Alternatives to ARP
Instead of ARP, the IPv6 protocol utilizes the NDP (Neighbor Discovery Protocol) and its extensions (Secure Neighbor Discovery, etc). Instead of using an active protocol, computers maintain lists of known addresses. In NDP, every system maintains a database of the Layer 3(IP addresses, etc) to Layer 2 (Ethernet MAC addresses, etc) address mappings.
This database id primarily maintained by interpreting the ARP packets from the local network link. For the same reason, it is also referred to as the ARP cache. In early times, in order to maintain the mapping between addresses, other methods were used, for example centrally maintained lists, static configuration files, etc.
ARP Stuffing
ARP Stuffing means a user “stuffing” a static ARP entry into their local computer system’s ARP cache, with the desired IP address of the device they want to configure. ARP stuffing can be used by networked cameras, networked power distribution devices, and other similar embedded systems which lack a user interface. It is used for making an initial network connection, although there is no involvement of any ARP protocol. ARP stuffing is a solution to a problem in network management of consumer devices, precisely the allocation of IP addresses of ethernet devices where:
- The user is unable to control
DHCPor other similar protocols. - The device does not possess a user interface to configure it.
- The computer of the user is unable to communicate with it because it does not have a suitable IP address.
ARP stuffing, as a solution works as follows: an IP address is stuffed manually into the address table of the user’s computer system. Then special packets are sent to the device. Then the IP address is adopted by the device, and the user may then communicate with the device by web protocols or telnet for completing the configuration. Most of the time, such devices have a technique to shut this procedure once the device begins operating normally since it is susceptible to Denial of Service attacks.
ARP Relationship with DHCP and DNS and How Do They Differ?
Both ARP and DNS (Domain Naming System) are special protocols used for running the internet, but it’s difficult to compare them. ARP is needed for packet transfers. DNS is not needed but reduces complexity. The Domain Name System is a decentralized and hierarchical naming system for resources connected with the network.
DHCP (Dynamic Host configuration protocol) is a network protocol. It is used for automatically assigning the IP address to a computer system or any other device on each LAN network. DHCP can use ARP. The RFC (Request For Comment) for DHCP mentions that when a device is offered an IP address by the DHCP server, the device can pass the address through to determine whether any other device on the network uses the address. If a conflict arises, the device must refuse the IP address offered and request an offer of a unique new address.
Conclusion
- ARP (Address Resolution Protocol) is a crucial communication protocol in the Internet protocol suite used for discovering the data link layer address, such as a MAC (
Media Access Control) address, corresponding to a given network layer address. - ARP is implemented with several combinations of the data link and network layer technologies, such as
Chaosnet,IPv4,Xerox PARC Universal Packet (PUP),DECnet,FDDI,Frame Relay, andAsynchronous Transfer Mode(ATM), X.25. - Following are the components of the ARP packet format: Hardware Type, Protocol Type, Hardware size, Protocol Size, OpCode, Sender MAC address, Sender IP address, Target MAC address, and Target IP address.
- ARP is of the following four types: Inverse, Reverse, Proxy, and Gratuitous.
- ARP spoofing is also referred to as ARP cache poisoning and ARP poison routing. It is a technique using which an attacker sends a spoofed Address Resolution Protocol message onto a LAN.
- 128 bits long IPv6 addresses use the Neighbor Discovery protocol instead of ARP, for acquiring the configuration information.
- ARP stuffing can be used by embedded systems that lack a user interface for making an initial network connection.
