CRAM stands for Challenge Response Authentication Mechanism and it is a set of protocols used for authenticating a user by giving them a challenge and access is provided to the user only if they answer the challenges correctly.CAPTCHA is one example of Challenge Response Authentication.
Introduction
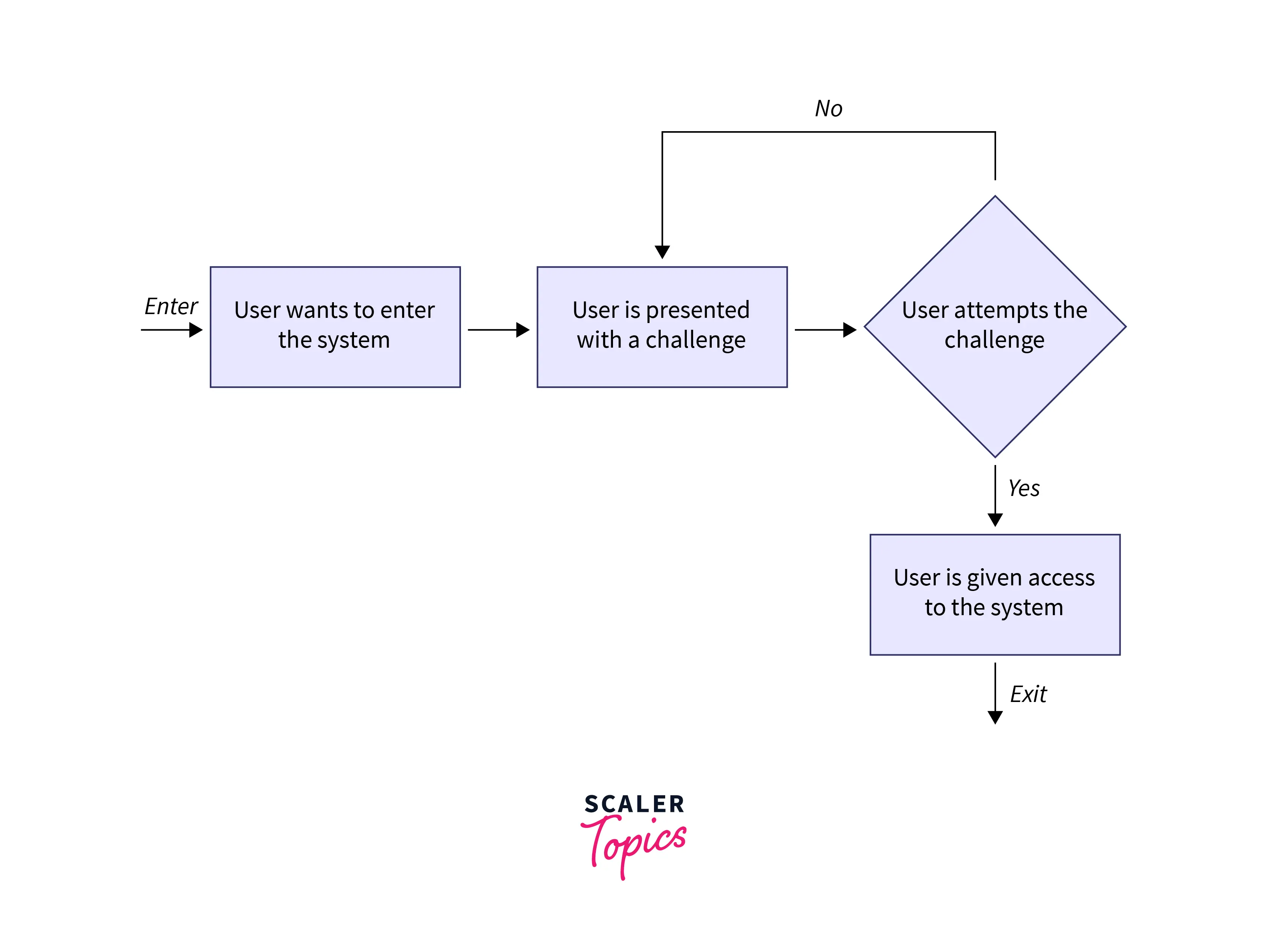
The Challenge Response Authentication mechanism is abbreviated as CRAM and is most often used for authentication of the actions. CRAM is considered a set of protocols in which on one side there is a challenge that is to be answered and on the other side, there is a correct answer that is to be required to validate or to check the challenge so that authentication can be done.
- If we look at CRAM in the simple form then challenges response authentication comprises two components that are response and the question.
- The main aim of this question and challenge is the need for a response from which only authorized users are aware.
- Challenge Response Authentication Protected digital material access is provided to those users who will properly answer the question.
- The main aim of CRAM is to provide limited access and control and limited use of digital resources so that only users that are authorized will access and only authorized activities will be performed.
Refer to the below image for the flow diagram of the CRAM
Types of Challenge Response Questions
There are two types of challenge-response questions:
- The first type of challenge-response question is the static question as the name of this question suggests that it will consider the static approach while selecting the challenge. The user can authenticate himself by selecting his challenge. For instance, we will take the use case of forgetting the password for an email account. In this situation, the Static challenge is the security question that the user has saved at the time of registration. Those questions’ correct answers are not expected to change with time.
- The Second type of challenge-response question is the dynamic question. In this question, the dynamic approach is to be considered while selecting the challenge and for the authentication. In this, we will randomly choose the challenge by making a pre-assumption that the user will be aware of the correct answer for that challenge and consider that the user is real.
How Challenge Response is Used?
Challenge Response Authentication just acts as a barrier to the protection of assets from unauthorized access, users, activities, and programs. Challenge Response forces cyber security attackers to satisfy the set of challenges when they try to bypass the security barrier and try to access the content.
For the establishment of multi-factor authentication processes, commercial banks use challenge-response authentication. This user identity is authenticated by using different CRAMs.
Password and code sent to a specific email ID is an example of a two-factor authentication process.
Different Use Cases of Challenge Response Authentication
The main purpose of using Challenge Response Authentication is to provide login authentication however, there are two major areas in which Challenge Response Authentication is used which are given below
Human Verification
- When the user logs into the page sometimes the user is asked to complete some challenges and these challenges are to prove that the person trying to log in is not a robot.
- These types of challenges are created to block the programs(not users) from accessing the web pages.
- Let’s understand it with an example this is used by many e-commerce websites for verifying the human so that robots cannot buy a huge amount of supplies automatically.
- These bots use fraudulent or stolen data for purchase and also limit the regular user experience.
- To avoid this and ensure the security and safety of the website Challenge Response Authentication is one of the ways.
- A common type of challenge for the verification of humans is selecting an image that contains a particular object or an item such as stairs.
- (Completely Automated Public Turing test to tell Computers and Humans Apart)
CAPTCHAis another example that is used to verify whether the user is a human or a robot
Machine Learning Training
- The ability of machine learning to complete multiple tasks simultaneously is one of the biggest advantages of machine learning.
- ML and artificial intelligence software are used in cyber security to comb systems for dangerous or suspicious behavior.
- Challenge Response Authentication helps solve a complex problem by testing and training the machine learning models.
- Puzzles for human verification are provided to some of the ML programs and answers to those puzzles are made and compared with the answers of humans.
- After that ml program informs about its future decision-making by learning from the examples of humans.
Examples of Challenge Response Authentication Systems
Some of the commonly used examples of challenges response authentication are given below:
CAPTCHA
This is used to differentiate between humans and bots, CAPTCHA was developed to prevent boards from doing spam, and it also prevents the registration of fake new accounts and genuine user accounts hacking.
Refer to the below image for the CAPTCHA
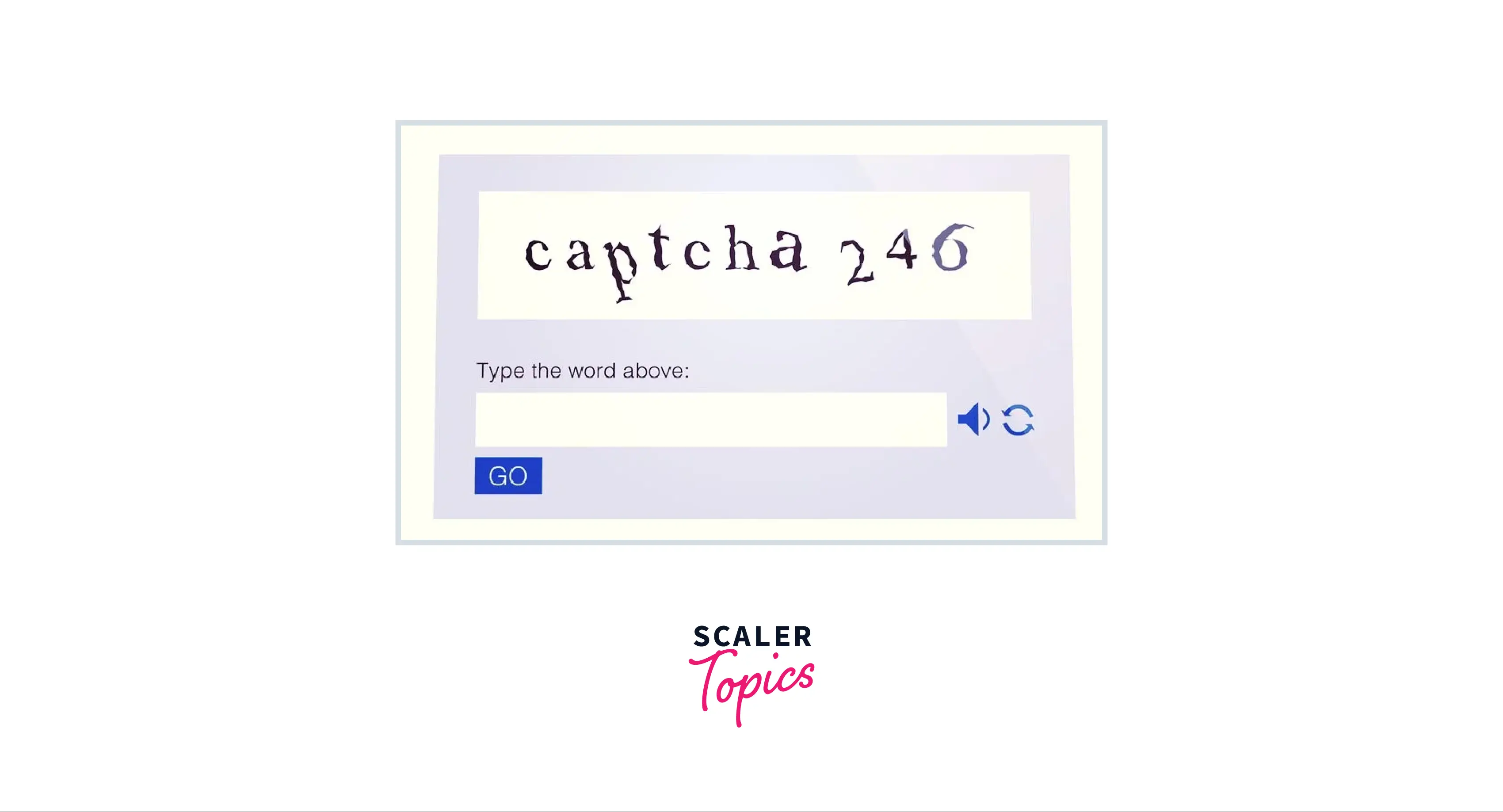
Refer to the below image for the CAPTCHA
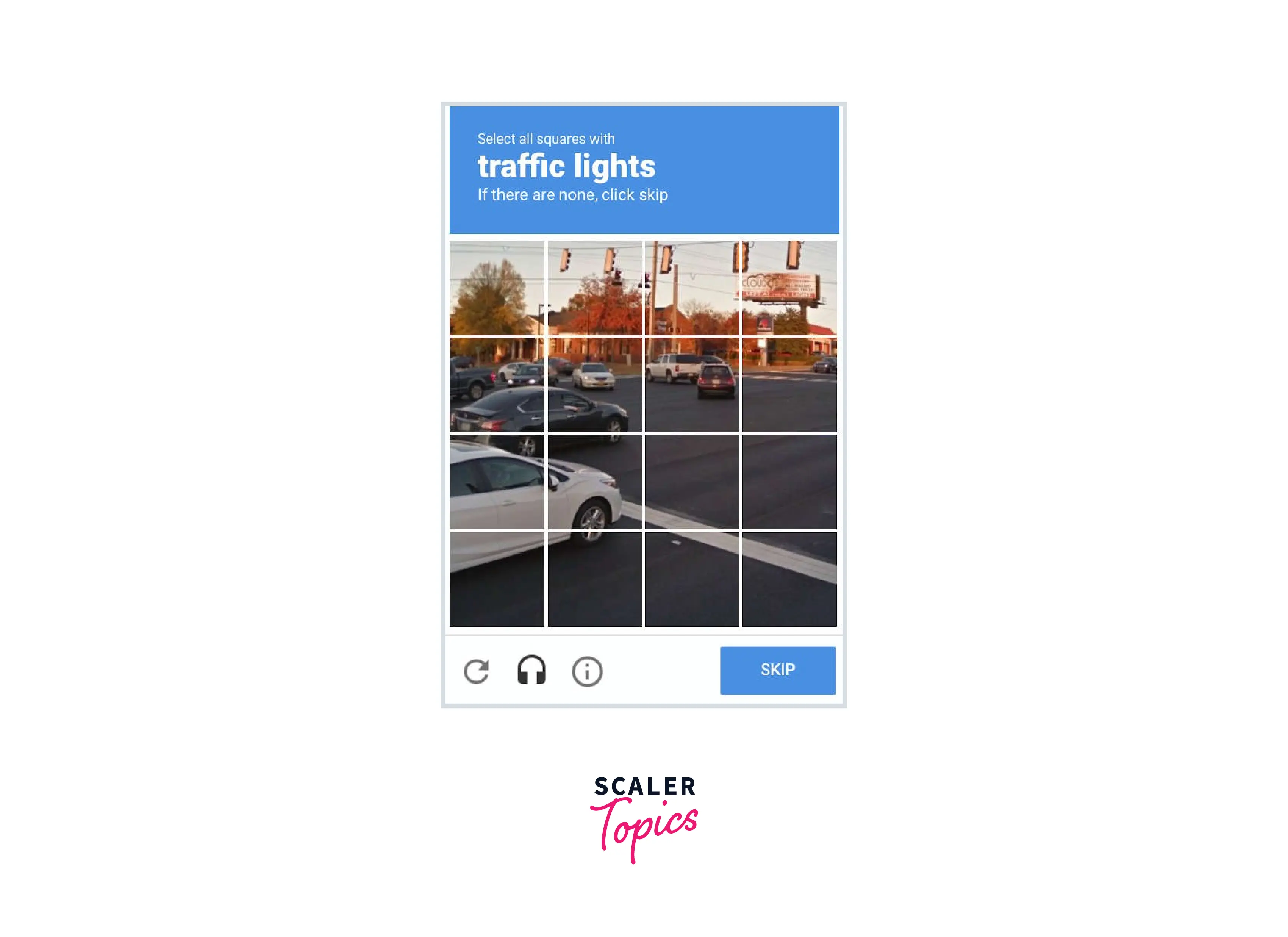
Refer to the below image for the CAPTCHA
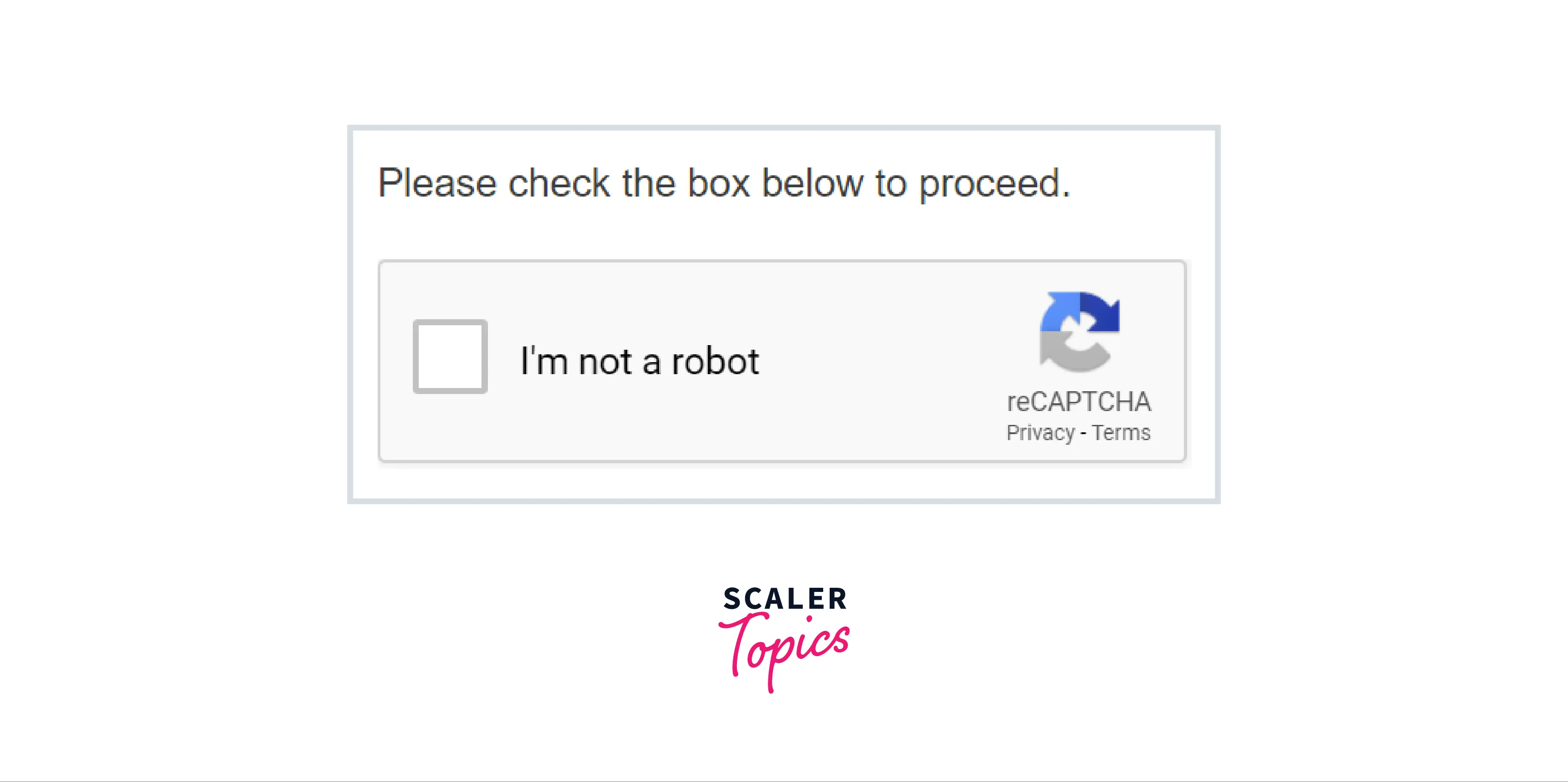
Password
The password entered by the user is validated with the correct password by the server.
Refer to the below image for the password
Biometrics
For authentication of the user, the biometric details of the user are matched with the biometric details of the user issued in the authentication system. Biometric details of the user may involve iris or fingerprint scans.
Refer to the below image for the Biometrics

Refer to the below image for the Biometrics

Salted Challenge Response Authentication Mechanism (SCRAM)
The hashed challenge is used when the user can use the password once only. The hash provided by the user is matched by the server with the already saved hash so that password is protected from the exposure which can cause through the replay or the man-in-the-middle attacks.
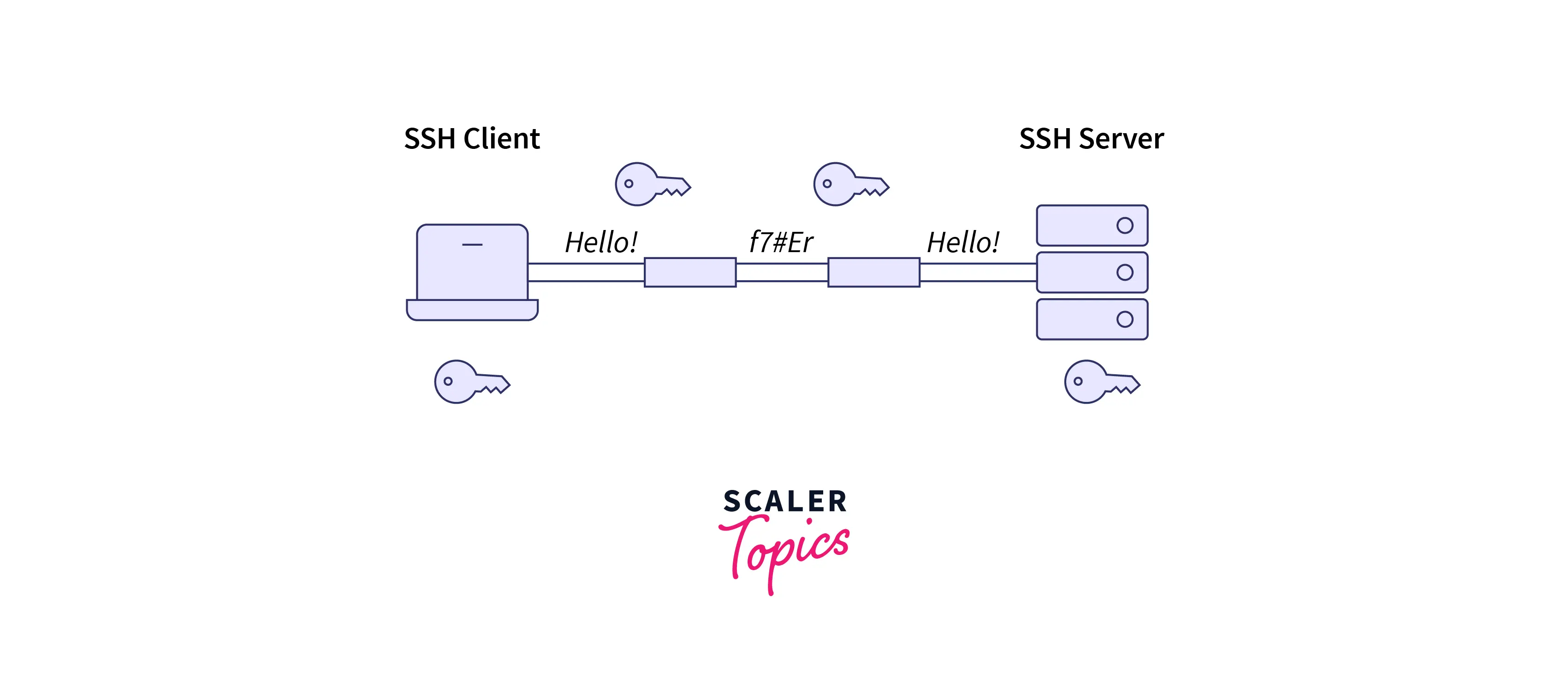
SSH (Secure SHell)
SSH is one of the cryptography network protocols that allows network services operation security on an unsecured network. It uses a public interest structure for authentication of the communication session between different servers.
Refer to the below image for the SSH
Zero-Knowledge Password-Proof Systems
This is also one of the cryptographic methods that are used for verifying passwords between two users without mutual sharing of their passwords. In this system, the party has to prove that it knows about the credential by using cryptography without transmitting the credentials.
OATH Challenge-Response Algorithm
It is created with the initiative of open authentication and it is considered a cryptographically stronger CRAM protocol.OATH algorithm has the capability of identifying the server.
In this algorithm, code is provided by the website on which the client tries to log in, then the client has to enter this provided code into the token, and then another code is returned as a response. And the client has to enter this code for successful login.
YubiKey
HMAC-SHA1 and Yubico OTP are used in this method for authentication. In yubiKey, yubiko OTP encrypted code is created by yubika OTP using the key of stored AES.
It provides extra security and saves time.
The Yubico-enabled authentication app works across many Operating Systems such as Windows, macOS, Linux, iOS, and Android.
Other Non-cryptographic Protocols
Challenge Response protocol keeps the knowledge of secret values with this it also asserts other things.
For example, CAPTCHA is one of the variants of the Turing test which determines whether the user is human or a bot. In early times for CAPTCHA verification, a challenge is sent to the user and that challenge is the distorted image and the user has to type the text given in the image. Because the image is distorted so the optical character recognition of the image becomes difficult and the passing of the computer as a human is prevented.
Cryptographic Techniques
At the time before the internet non-cryptography authentication methods were adequate, at that time when the system asked for the password then there was a surety that this was the system that was trying to access and nobody on the channel was trying to eavesdrop( eavesdropping is intercepting, deleting, or modifying the data transmitted between two devices by the hacker) by observing the password entered by the user. More sophisticated approaches are required to address the problem of insecure channels. Two-way authentication is involved in many cryptographic solutions.
Password can be used as an encryption key for transmitting some of the randomly generated information in the form of a challenge and from the other end response is received in the encrypted form which is obtained by applying some predefined function to the original data with will prove that the challenge can be depicted.
Those hashed or encrypted exchanges do not reveal the password to the eavesdropper. But they provide enough information to the eavesdropper to deduce the password, the brute force attack, or the dictionary attack. The possibility of a replay attack is guarded by making use of the randomly generated information for every attack and the malicious intermediate simply stores the information that is exchanged and transferred and this stored information is used later to make a fool of one end into thinking it has authenticated for an attempt of new connection from the other.
Some Examples of Cryptographic CRAMs
- CRAM-MD5
- SCRAM – Salted Challenge Response Authentication Mechanism
Common Attacks on Challenge Response Authentication Mechanism (CRAM)
- Eavesdropping
- Phishing Attacks
- Browser Poisoning Attacks
- Brute-Force Attacks
- Pharming Attacks
- Dictionary Attacks
- Man-In-The-Middle Attacks
- DNS Cache Poisoning Attacks
- Trojans Attacks
- Man-In-The-Phone Attacks
- Reusable password attacks
- Zero-knowledge password proof
Limitations of CRAMs
- New variants of CRAM use cryptography so for authentication hash value of the password is matched instead of the original main password. This has the disadvantage of a large number of collisions.
- The Main problem of CRAM is the repetition of the user password. When the Password entered by the user is sent to the server then it is not able to recognize whether the user is real or not.
Best Practices for Challenge Response Authentication
Well, Implementation, design,n, and deployment of the interactive challenge-response authentication system of an organization have a significant impact on its overall effectiveness. To ensure high-quality challenge-response authentication, businesses must consider the following best practices and guidelines:
- Implementation of an automated enrollment system, for inviting users so that they can complete their challenge-response profiles.
- Avoid answering those questions that can be guessed or researched.
- Data used for authentication purposes must be in encrypted form, especially the answers given by users for personal challenge questions.
- If a user fails in the authentication procedure, then after a specified number of failed attempts that user’s account is locked.
- Questions that are used must be a combination of user-selected and standardization questions. User-generated questions are more unique as compared to user-selected questions, although they are difficult to guess.
- There must be multiple tiers of questions: First, ask standard questions to the user. If the first set of questions is answered correctly then, ask the user-generated questions.
- Try not to ask more than six questions to the user during the authentication process, it may make the user frustrated.
- Avoid displaying the answers to challenging questions. It may expose them to malicious eavesdroppers.
- Questions are created in such a way that is easily remembered by the user.
Conclusion
- CRAM is the set of protocols that provide limited access and control and limited use of digital resources so that only users that are authorized ed will access and only authorized activities will be performed.
- Static and Dynamic questions are the two types of questions of CRAM.
- Human verification and Machine learning training are the different use cases of the CRAM
SSH,Password, andCAPTCHAare some examples of CRAM.- Brute-Force Attacks, Pharming Attacks, Dictionary Attacks, Man-In-The-Middle Attacks, and DNS Cache Poisoning Attacks are some of the common attacks of the CRAM.