In controlled access protocols, communication on a shared medium is regulated to prevent data collisions. Each station consults with others to determine which has the transmission right, allowing only one node to send data at a time. This method ensures efficient data transfer without conflicts. The three primary controlled access techniques are Reservation, Polling, and Token Passing, each playing a pivotal role in maintaining network integrity and data flow.
Reservation
- In this method of controlled access protocol, first of all, the station is required to make a reservation, then only it can transmit the data on the shared medium.
- There are two types of periods in the timeline
- At first, there is a fixed time length in the interval of reservation.
- The second is the data transmission period of the variable frame.
- The interval of the reservation depends on the number of stations on that particular medium.
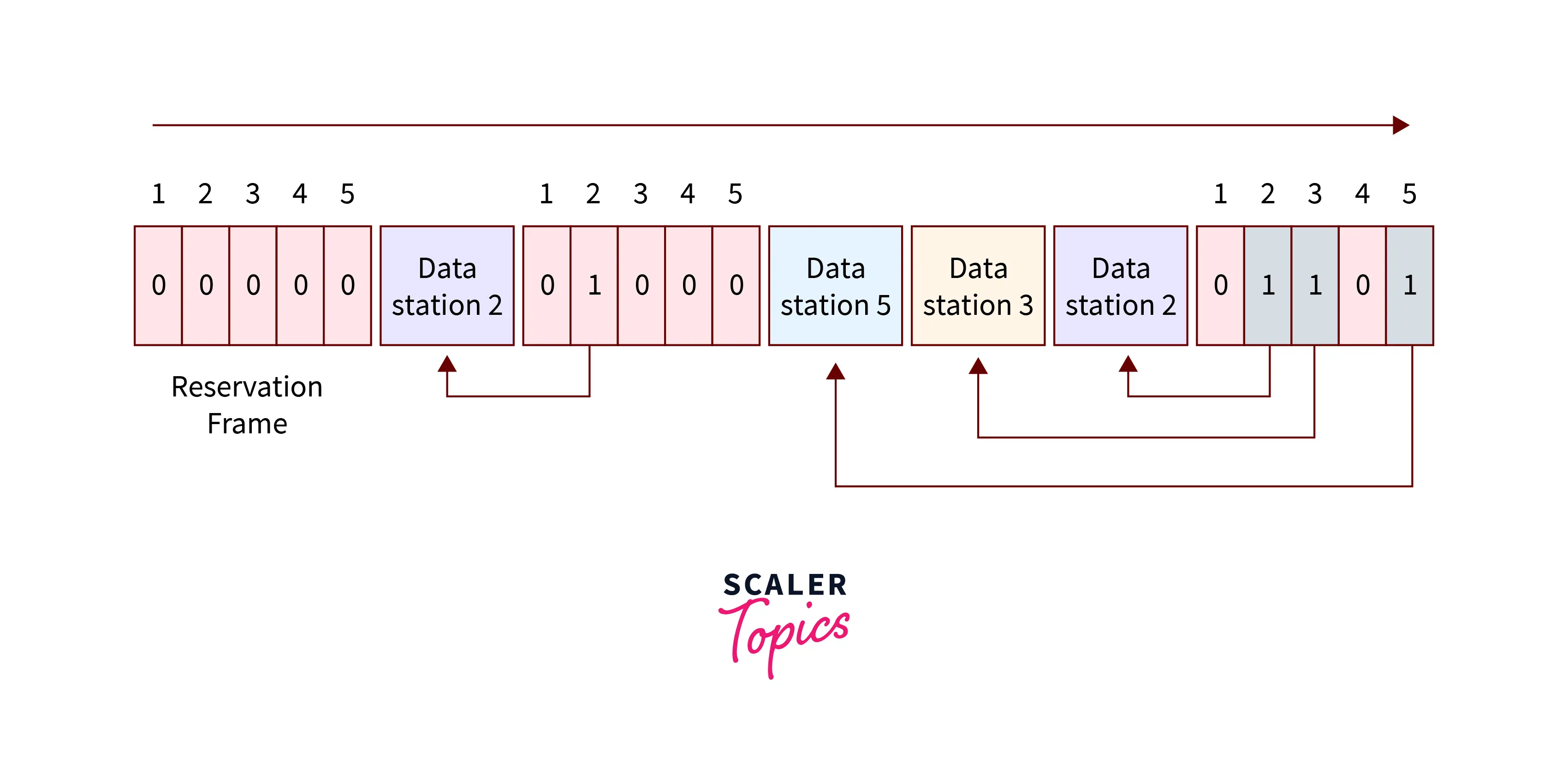
- Suppose there are M stations, then the reservation interval is divided into an equal number of M slots. There is one separate slot for each station.
- Suppose station 1 wants to transmit a frame to another station, then it can send only 1 bit during slot1. During this period, no other station can transmit the data on the medium.
- Suppose the ith station wants to send a frame by adding one bit into the ith slot then after checking all the N number of slots, each station will learn which station wants to transmit the data.
- The station can transfer the frame according to the sequence in which they reserved the slot.
- If the transmission period expires then a new interval reservation starts.
- There is no chance of collision if the station agrees on the thought of which station is next to transfer the frame.
Example
Let us take an example, through which we learn how reservations work. Suppose there are 5 stations and also 5 mini slot reservation frames. If in the first interval, only the 2nd,3rd, and 5th stations are allowed to make the reservation and then after that in the second interval only the second station is allowed to make the reservation.
Refer to the below image to understand the example of a reservation
Polling
Generally, the polling method is used in those types of topology where one device is served as a primary station and other devices are served as the secondary station.
- In this method, all data needs to be transmitted through the primary device even though its final destination is the secondary device.
- The primary device is acting as an initiator and always controls the link.
- On the other hand, secondary devices must follow the instructions of the primary device.
- This is the responsibility of the primary device to decide which particular secondary device is allowed to access the channel for how much time.
- Data frame transmission is done by the primary device and also contains the address of the secondary device that has been chosen for granting access.
- All secondary devices can receive the data but the device that is addressed can only be allowed to respond to that data and transmit data if has any to send.
- Otherwise, if there is no data to send then, it transmits a poll reject (NAK) frame to the primary device.
Efficiency
Suppose the time for Polling is Tpoll and Tt will be the time needed for the transferring of data. Then $$Efficiency = {\frac{Tt}{Tt+Tpoll}}$$
Poll Function
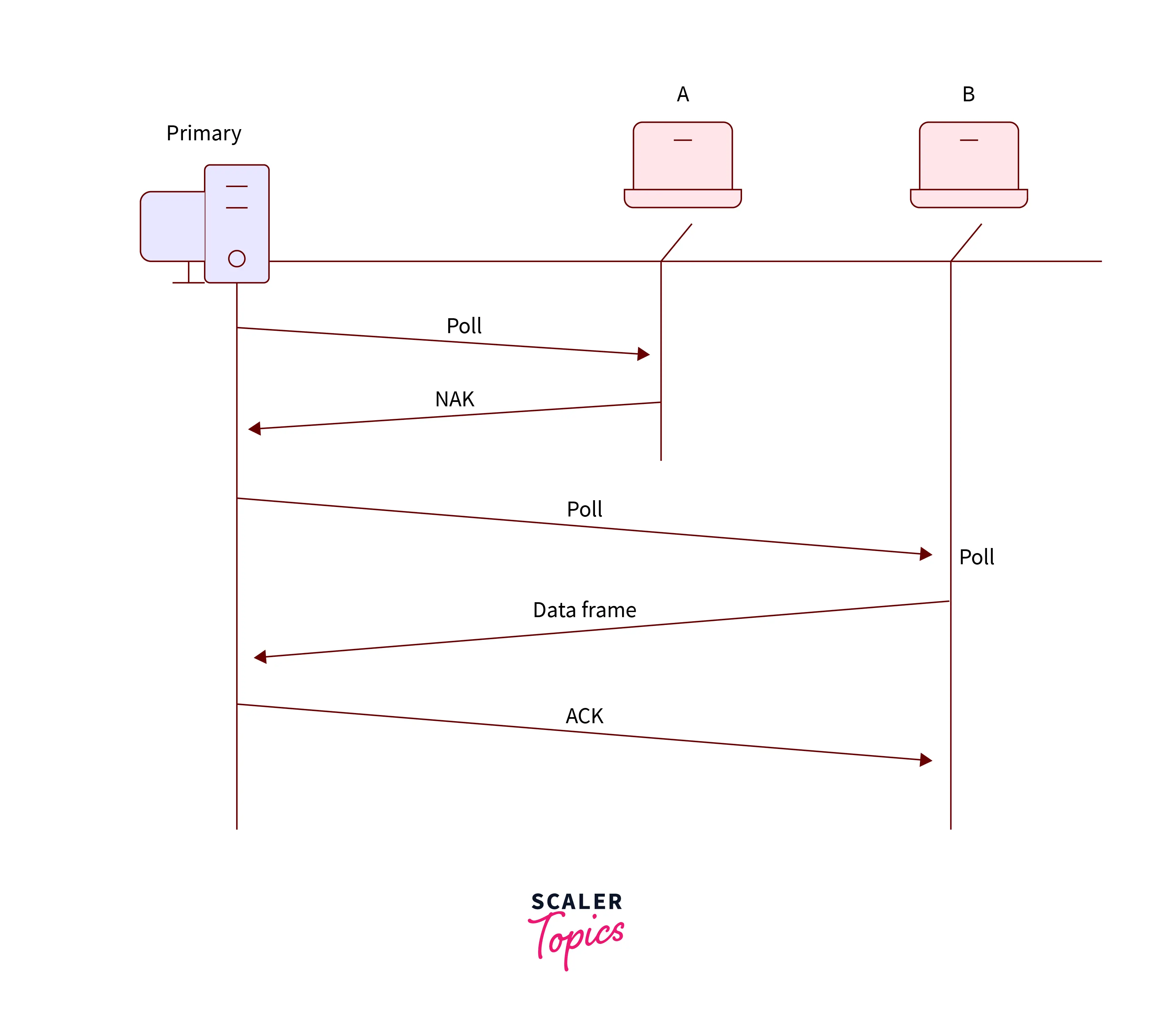
Suppose there is a condition when the primary device wants to accept data from secondary devices, then in this condition, it generally asks from secondary devices if they want to transmit any data. This process is known as the polling function. The polling function is used by the primary device to ask for transmit the data from the secondary device.
- When the Primary device wants to get the data frame then it should ask (poll) each secondary device on that particular network if they want to transfer any data frame.
- If the secondary device has any data that it needs to transfer to the primary device then it sends the data frame although it will transmit a
negative acknowledgment (NAK) - If there is a condition when the primary device receives a negative acknowledgment from one secondary device then it repeats this process with another secondary device in the same manner till it finds the secondary device that has some data to send.
- Whenever the primary device gets a positive acknowledgment i.e. data frame from any secondary device, then after it, it reads the data frame and transmits a
return acknowledgment (ACK).
Refer to the below image for the visualization of the poll function
Select Function
Suppose there is a condition when the primary device needs to send some data to secondary devices then they tell the secondary devices so that secondary devices prepare themselves to receive the data. This process is known as the select function. The primary device generally uses a select function when it wants to send some data to secondary devices.
As already mentioned above the primary device always has control over the link.
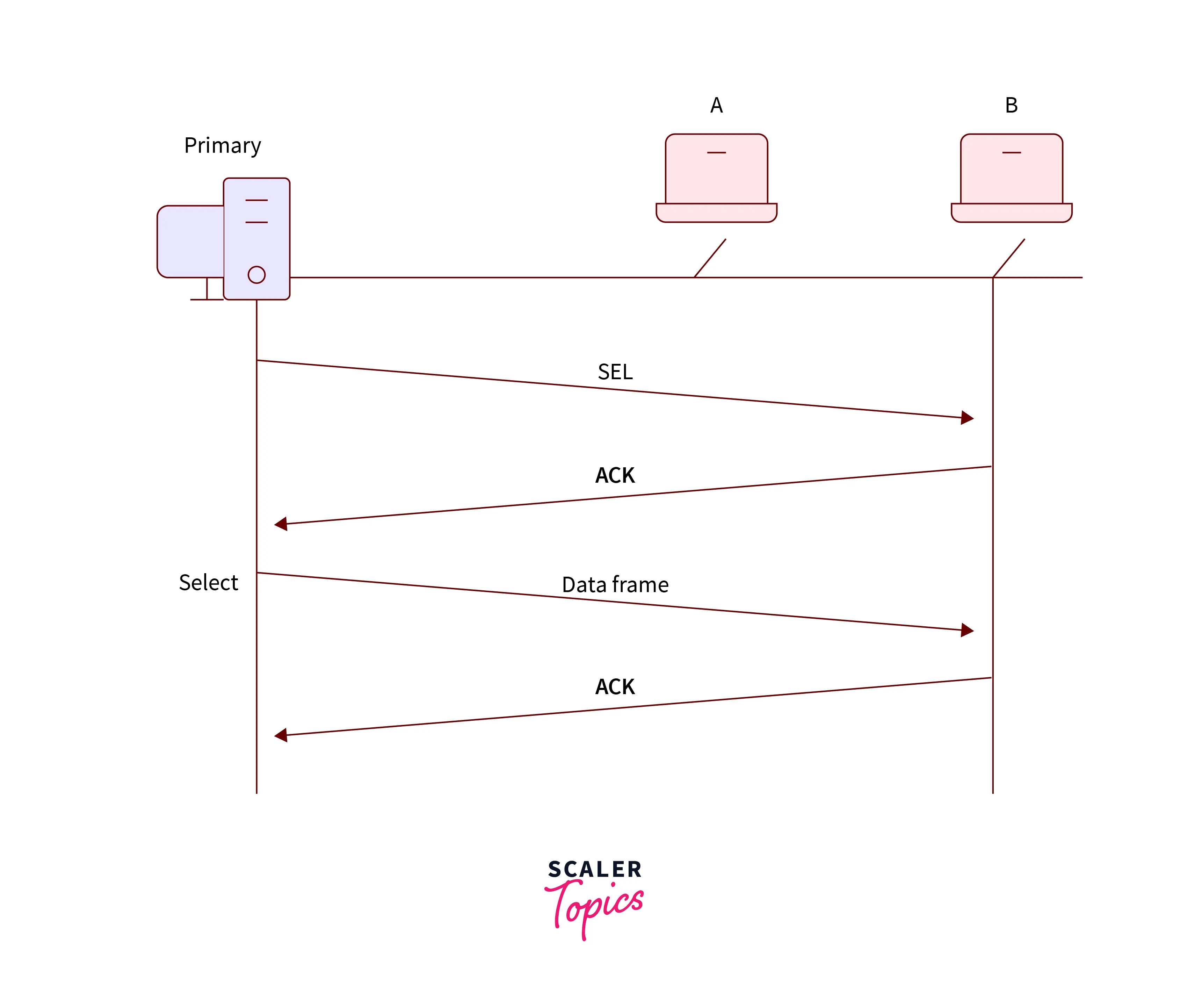
- Before transferring any data frame, there is the creation of a
select (SEL)frame - And the primary device transmits this frame to the secondary device.
- This SEL frame in its one field contains the address of the secondary device to which the primary device wants to send the data.
- There is an alert from the primary device to the secondary device for the transmission of the upcoming data packet.
- After this primary device waits for the
acknowledgment(ACK)frame from the secondary device.
Refer to the below image for the visualization of the select function
Advantages of Polling
Some of the advantages of using the polling method are given below
- There are fixed and predictable data rates and the minimum and maximum access time on the channel.
- To ensure faster access to data from the secondary device it used priority assignment.
Drawbacks
Some of the disadvantages of using the polling method are given below:
- The dependency on the reliability of the controller is high.
- In the condition of low load, there is a decrement in the data rate of the channel due to the increment in turnaround time.
- There is so much overhead of polling messages.
Token Passing
All the stations present in a particular network are arranged in the form of a logical ring in the token-passing method. In other words, there is always a predecessor and successor for each station in a medium. The station that is logically present before the station in the ring is known as the predecessor station and on the other hand, the station that is present after the station in the ring is known as the successor station.
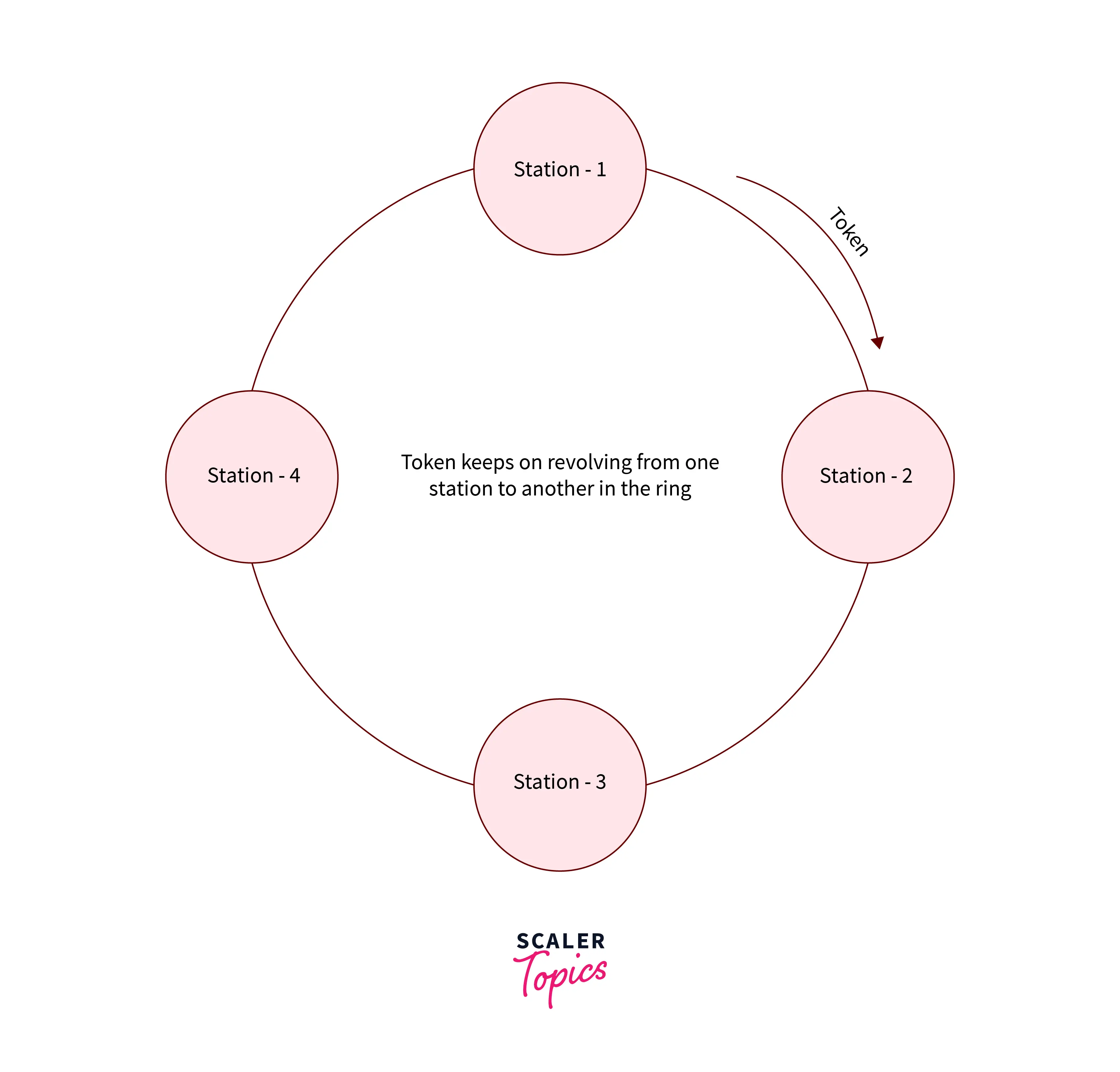
The station that is currently using the channel is known as the current station. There is a special bit pattern or a small message known as a token. It usually passes in a predefined order from one station to another station.
- The station that has this token now has the right to access the channel and can also transmit data present in its queue.
- Any station needs to wait for some time till it gets a token from its predecessor station if wants to transfer any data.
- After this, the station receives a token and then holds it and have now the right to access the channel and transfer its data.
- In the condition, when the station has nothing to transfer then it releases the token soon and passes this token to the next logical station present in that particular ring.
- Although, the station can transfer the data again only when it has a token and it is possible now in the second round only.
- Station simply passes the token to the next logical station if it has nothing to transfer at that particular time.
There is a problem of replication of token or sometimes the loss of token in the token passing method. The creation of a new station or the deletion of the existing station can be proved to be the hurdle in performing the token passing method properly and reliably.
Performance
There are two parameters through which the performance of the token ring can be identified –
- Delay and
- Throughput
Delay: Delay is considered as the measurement of time. Delay is the time difference between when the data packet is ready to transfer and when it is transferred. Therefore, ${\frac{a}{N}}$ is the average time needed for sending a token to the next station.
Throughput: There is always some traffic on the network in which you transfer the data packet. So the measure of successful traffic on the communication medium is known as throughput.
$Throughput, S = {\frac{1} {(1 + a/N)}}$ for a<1
here N = number of stations,
$a={\frac{Tp} {Tt}}$,
Tp = propagation delay,
Tt = transmission delay
The diagram below shows that when station-1 has a token, it transfers all the data frames that it wants to transfer on the medium. It transfers all the data frames present in its queue. After this station-1 passes the token to station-2 and this process repeats itself. Station-1 can now only transfer the data again when all the stations present in that particular network have already transmitted their data frame and passed their token.
Refer to the below image for a visualization of the token-passing approach
Advantages
Some of the advantages of using the token passing method are-
- It resolves the problem of the collision of data on a particular medium.
- It allowed equal access to resources to each connected station in a particular network.
Disadvantages
Some of the disadvantages of using the token passing method are-
- Station had to wait for the token even if no other computer wanted to transmit the data.
- Required more expensive equipment for complicated processes.
Conclusion
- The controlled access protocol allows only one station to transfer data at a time.
- Three common controlled access protocol methods are reservation, token passing, and polling.
- In reservation, a station needs to make a reservation then only it can transmit the data on the medium.
- In token passing, all the stations in a particular network need to be arranged in the form of a logical ring, then only send the data.
- In Polling, only one station serves as a primary station, and all other stations on a medium act as the secondary station.
- Delay and throughput are the parameters for governing token passing.