SSL (Secure Sockets Layer) is a cryptographic protocol that enables data transmission security over a TCP (Transmission Control Protocol) connection. This protocol ensures that any information transmitted between the two parties remains confidential and safe from potential attackers. SSL, and its successor Transport Layer Security (TLS), are fundamental technologies used to establish secure and encrypted communication channels between clients and servers on the Internet. SSL/TLS ensures that sensitive information, such as login credentials, financial data, and personal information, remains confidential and tamper-proof during transmission.
Understanding TCP Connections
TCP (Transmission Control Protocol) connections are critical for understanding data transmission reliability across the internet and computer networks. TCP is one of the core protocols of the Internet Protocol (IP) suite that ensures the orderly and error-free transmission of data between devices on a network. TCP allows for bidirectional data transmission. This means that TCP-enabled computer systems can send and receive data at the same time, much like a telephone call.
TCP is good at transferring data reliably, but it is not secure. That is why we use SSL (Secure Sockets Layer) to make TCP more secure. SSL encrypts your data so that it remains private and unaltered while it travels over the internet. This is critical for protecting sensitive information online.
If you want to learn more about TCP connections, please read Transmission Control Protocol (TCP) article. It will help you understand how TCP connections work.
Procedure to Secure TCP Connection with SSL
Follow these steps to create a TCP/IP server configuration that uses SSL:
- Set the Port Number:
Select an appropriate port number for your TCP/IP server. This is the port where your server will listen for incoming SSL/TLS connections. - Set the SSL Protocol:
Configure the server to utilize the “TLS” (Transport Layer Security) protocol for safe connection. TLS is the successor to SSL and offers strong encryption and security features. - Define Cipher Suites:
Set up a list of cypher suites that your server will accept. Cypher suites specify the encryption algorithms and key exchange methods that will be used to secure the connection. For example:SSL_RSA_WITH_RC4_128_MD5;SSL_RSA_WITH_3DES_EDE_CBC_SHA
Customize this list based on your security requirements and compatibility with clients. - Configure SSL Client Authentication:
Set the “SSL client authentication” property to “require.” This setting mandates that connecting clients must provide authentication credentials to establish a connection, enhancing security. - Deploy the Policy Project:
Save your TCP/IP server configuration as a policy project and deploy it to the integration server where you intend to deploy your associated message flow. Ensure that the integration server is properly configured to support SSL/TLS connections on the specified port.
The Phases of an SSL Connection
There are various steps involved in establishing an SSL (Secure Sockets Layer) connection. These phases ensure that communication between a client and a server is secure and encrypted.
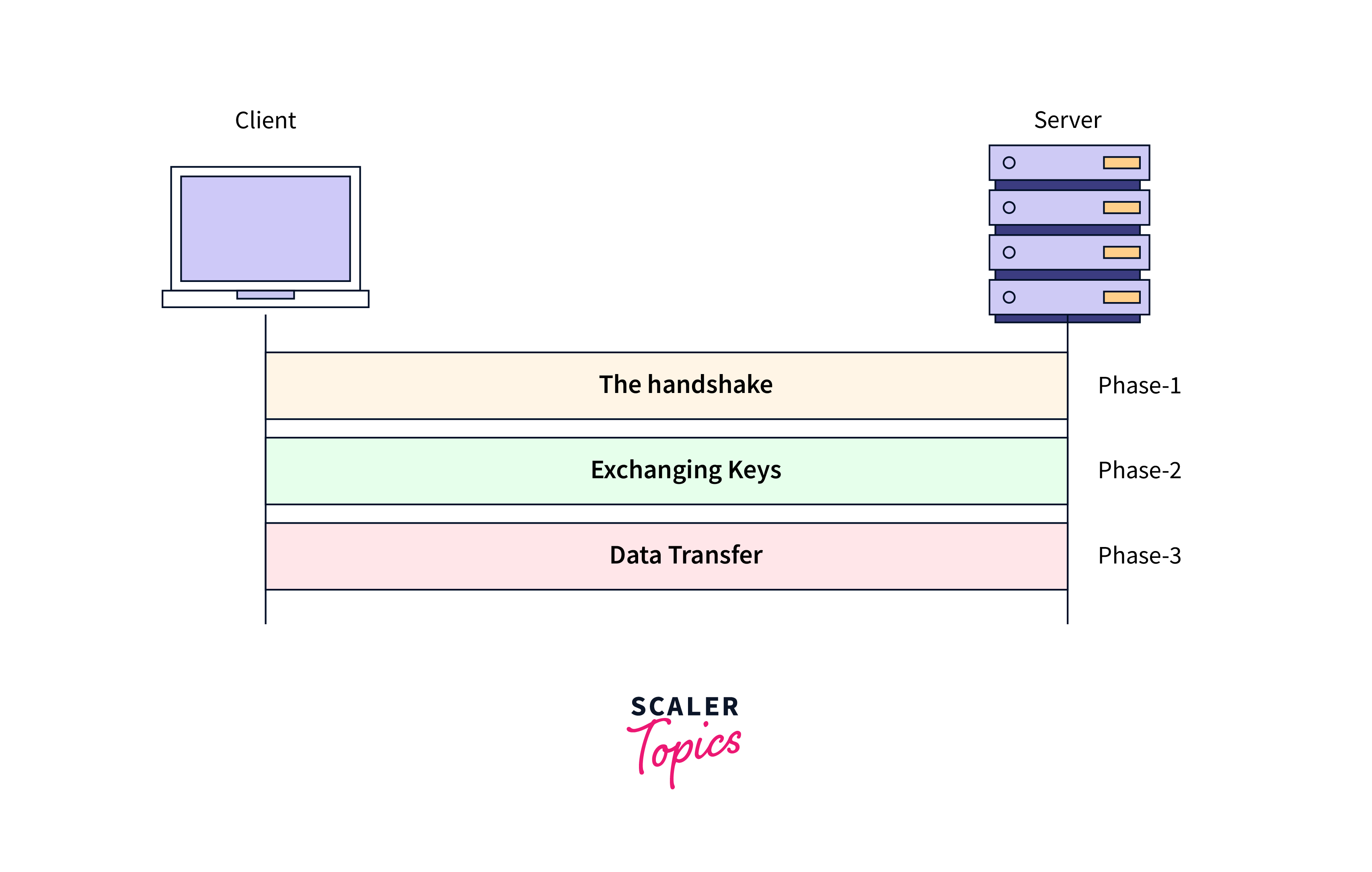
- Phase 1: The handshake:
- The client initiates a TCP connection by sending a SYN packet.
- The server responds with a SYN/ACK packet to acknowledge the client’s request.
- The client sends an ACK packet to confirm the connection.
- Phase 2: Exchanging keys:
- After the TCP connection is established, the SSL handshake begins.
- The client sends a hello message to the server, initiating the SSL handshake.
- The server responds by sending its signed certificate, which includes the public key but not the private key.
- The client verifies the certificate’s validity.
- If the certificate is valid, the client generates its own private key, encrypts it using the server’s public key, and sends it back to the server.
- The server decrypts the data using its own private key, obtaining the client’s private key.
- The server uses the client’s private key to decrypt the data portion of the packets sent by the client.
- Phase 3: Data Transfer:
After establishing a TCP connection and enabling encryption and decryption, the final two steps of the second phase are repeated to securely transfer segmented data over TCP segments over the created TCP connection.
Benefits of SSL for TCP Connections
SSL (Secure Sockets Layer) provides several important benefits when used in conjunction with TCP (Transmission Control Protocol) connections:
- SSL encrypts data transmitted over a TCP connection, ensuring that it is secure and confidential. This encryption stops unauthorized individuals from eavesdropping in and intercepting data.
- SSL validates data integrity during transmission. It checks that data has not been altered or tampered with while in transit using cryptographic hash algorithms.
- SSL provides a mechanism for both the client and server to authenticate each other. This ensures that the client is connecting to the intended server, reducing the risk of man-in-the-middle attacks and impersonation.
- SSL protects against phishing attacks by verifying the authenticity of websites. When users see the padlock icon or
https://in the browser’s address bar, they can be assured that they are connecting to a trustworthy site. - SSL encryption is required for secure e-commerce and online banking transactions. It protects financial and personal information while fostering confidence between consumers and websites.
- SSL helps organizations meet security and privacy requirements when handling sensitive data.
- SSL prevents data from being intercepted or manipulated by network intermediates such as ISPs or public Wi-Fi providers, which helps in the maintenance of privacy.
Conclusion
SSL (Secure Sockets Layer)is a cryptographic protocol that enables data transmission security over aTCP (Transmission Control Protocol)connection.- SSL/TLS ensures that sensitive information, such as login credentials, financial data, and personal information, remains confidential and tamper-proof during transmission.
- TCP is one of the core protocols of the
Internet Protocol (IP)suite that ensures the orderly and error-free transmission of data between devices on a network. - TCP allows for bidirectional data transmission. This means that TCP-enabled computer systems can send and receive data at the same time, much like a telephone call.
- TCP is good at transferring data reliably, but it is not secure. That is why we use
SSL (Secure Sockets Layer)to make TCP more secure. - SSL protects against phishing attacks by verifying the authenticity of websites. When users see the padlock icon or
https://in the browser’s address bar, they can be assured that they are connecting to a trustworthy site.