A telecommunications network is a collection of nodes linked together by telecommunications links that allow the nodes to exchange messages. The links may employ several technologies to transmit messages and signals based on circuit switching, message switching, or packet switching approaches. The public switched telephone network (PSTN), the Internet, computer networks, and wireless radio networks used by cell phone service providers are all examples of telecommunications networks.
Introduction to Telecommunication Networks
Telecommunications, or telecom, is the electronic exchange of information over long distances and includes all forms of voice, data, and video transmission. This broad term covers various information-transmitting technologies and communications infrastructures, including telegraphs, landline phones, mobile phones, satellites, microwave communications, fiber optics, and radio and television broadcasts.
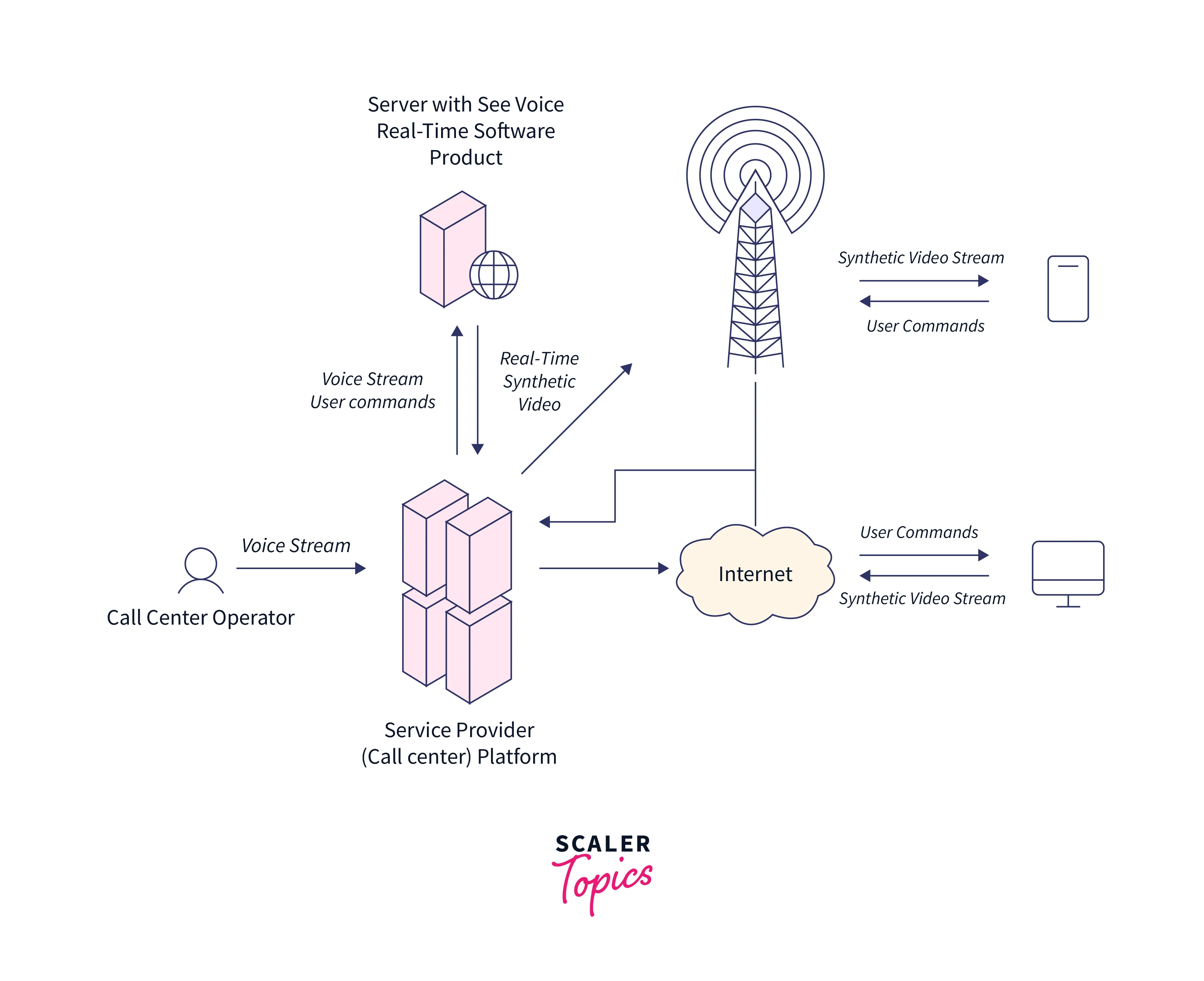
A complete telecommunications circuit comprises two stations, each of which has a transmitter and a receiver. At any station, the transmitter and receiver can be merged into a single device known as a transceiver. The signal transmission medium can be electrical wire or cable (commonly, we use copper-based cables), optical fiber, electromagnetic fields, or light. Wireless communications are the transmission and receipt of data in free space using electromagnetic fields.
History of Telecommunication Networks
The term telecommunications is derived from the Greek prefix “tele,” which means “distance,” and the Latin word communicare, which means “to share.” Let’s have a look at the brief history of the telecommunication network.
| Year | Work in the field of Telecommunication Networks |
|---|---|
| 1876 | Alexander Graham Bell created the first telephone. This early form required an interpreter, or telegrapher, at both ends. The early telephones were intercom systems, with two phones connected immediately. |
| 1877 | The invention of the switchboard exchange telephone system allowed any two phone lines to join and communicate with each other. |
| 1891 | Dial phones were invented, eliminating the need for an operator on every call. Making phone calls became significantly faster and more accessible as a result. |
| 1947 | The transistor was invented, which paved the way for contemporary electronics like computers and calculators. |
| 1948 | Microwaves were first employed to transfer phone signals in areas where phone cables were unavailable. |
| 1960 | When phones switched from mechanical to electronic switching, services like voice messaging, speed calling, and caller ID were possible. |
| 1984 | The Bell System was dismantled, allowing other service providers to compete for customers and removing AT&T’s near-monopoly on American telecommunications services. |
| 1984 | Two-way radio usage was replaced by cellular and personal communications service (PCS) phones for mobile communications. |
| 1990 | The modern internet has become widely used. |
| 2000 and beyond | Mobile phones became more sophisticated over the first decade of the 2000s. Smartphone use was common by 2012. |
Network Structure
Every telecommunications network is theoretically divided into three components or planes.
- Data Plane:- The data plane (also known as the user plane, bearer plane, or forwarding plane) transports the actual payload of the network’s users.
- Control Plane:- The control plane transports control information (commonly referred to as signaling).
- Management Plane:- The management plane transports network management operations, administration, and management traffic. The management plane is sometimes included in the control plane.
Data Networks
Data networks are widely utilized for communication between individuals and companies worldwide. Data networks can be linked to offer users seamless access to resources hosted outside the provider to which they are connected. The Internet is the best example of interconnecting multiple data networks from various enterprises.
IP addresses identify terminals connected to IP networks such as the Internet. The Internet protocol suite (TCP/IP) protocols govern and route messages across the IP data network. There are three major network structures that IP can be used to route messages efficiently. These structures are:
- Local Area Network.
- Metropolitan Area Network.
- Local Area Network.
Local Area Network (LAN)
Local area networks (LANs) are telecommunications networks that link various computers and information processing equipment within a constrained physical space. In small spaces like offices, classrooms, or manufacturing facilities, they are used to provide connectivity. Numerous firms frequently employ them to connect and facilitate communication between office end users, departments, workgroups, etc.
Metropolitan Area Network (MAN)
The Metropolitan Area Network (MANs) is a larger version of the Local Area Network. It uses a similar technology to LAN and is commonly referred to as MAN. LAN is limited to a private campus or building, whereas MAN is intended to span an entire city. It is a telecommunications network that combines multiple LANs into a single network or cable.
Wide Area Networks (WAN)
Wide Area Networks (WANs) are communications networks that cover a vast geographical area, such as a large city or metropolitan area. Large businesses use WANs or international corporations to transmit and receive information among employees, suppliers, and customers in different cities, states, or nations worldwide.
Types of Networks
Switched Communications Network
A switched communications network routes data from source to destination via a network of nodes. There are two methods for switching.
- Circuit Switching:- In a circuit-switched network, a dedicated physical path is established via the network and maintained for the duration of the communication. The
classic (analog) telephone systemis one example of this type of network. It is a connection-oriented transmission scheme, so every data follows the same path through the network. They often arrive at their destinations in the order they were sent.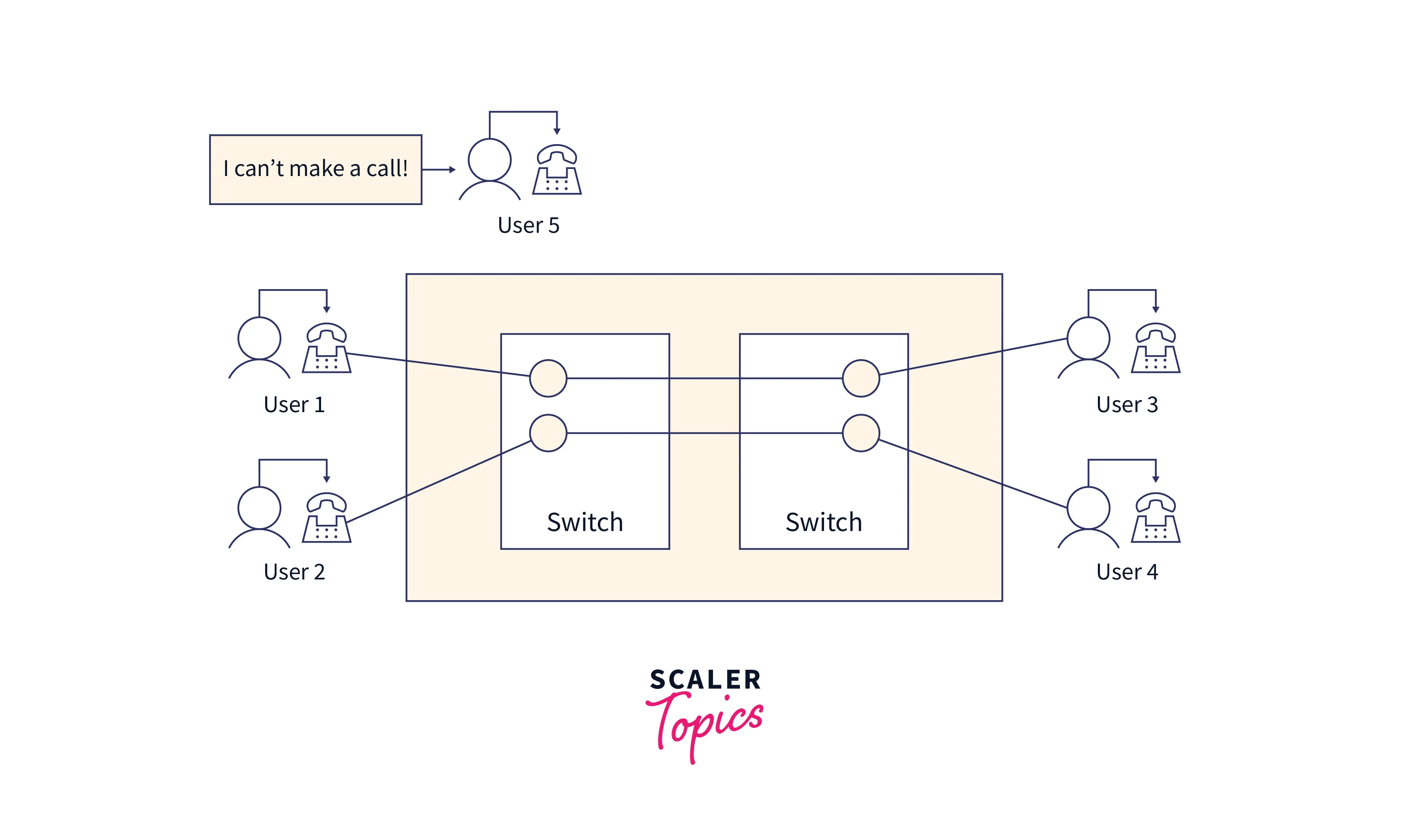
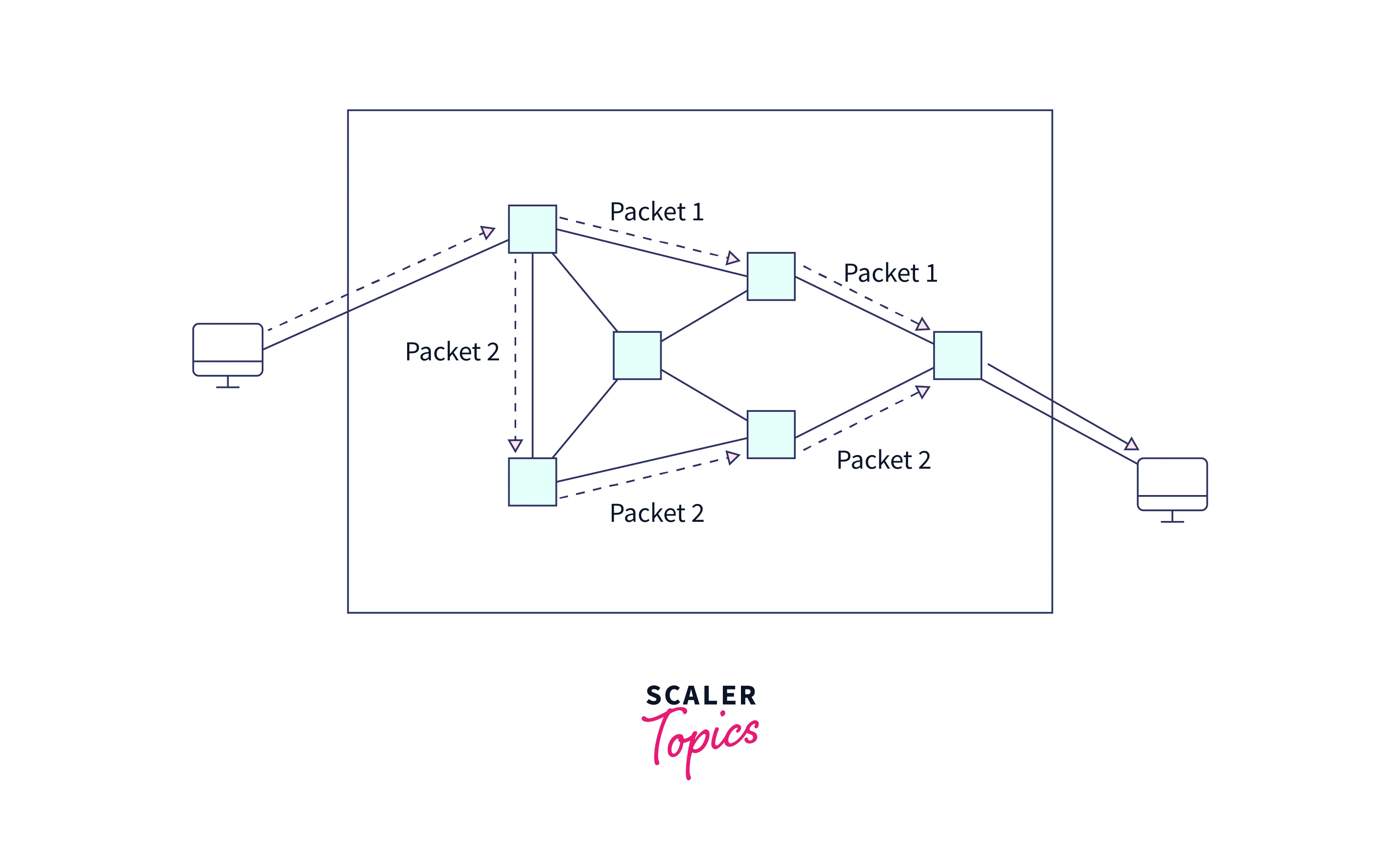
- Packet Switching:- A packet-switched network transports digital data in little chunks known as packets, each of which travels independently over the network. Packet switching networks use the store-and-forward technique in which each packet is temporarily kept at each intermediary node and then forwarded when the following link becomes available. It is a connectionless transmission scheme so that each packet may follow a distinct path via the network. Datagrams are numbered so they can be appropriately reassembled if they do not arrive at their destination in the sequence they were sent.
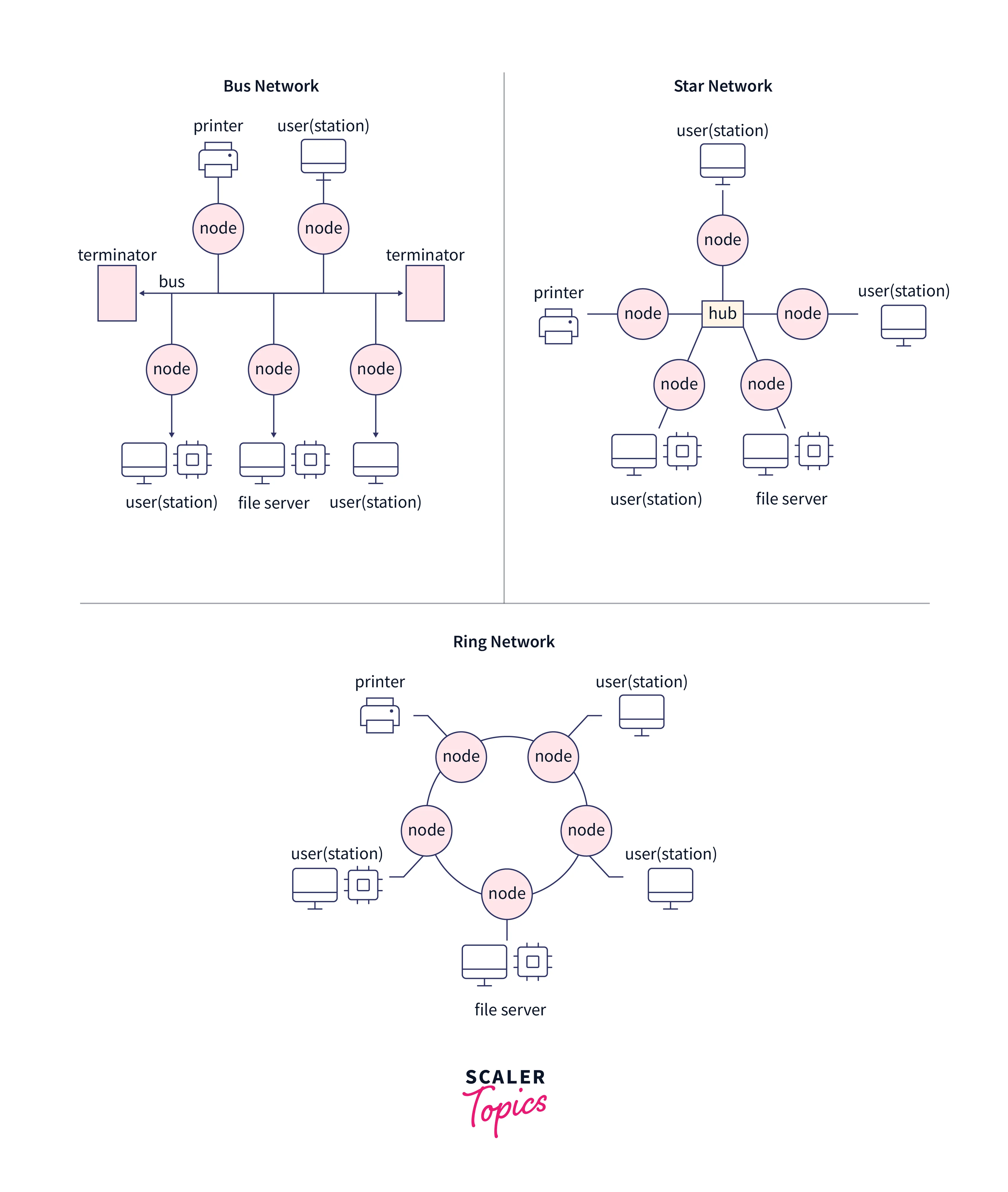
Broadcast Network
A broadcast network eliminates the complex routing procedures of a switched network by assuring that all nodes in the network receive all transmissions from each node. A broadcast network, as a result, has only one communication channel. For example, a wired local area network (LAN) can be configured as a broadcast network, where each node is connected with one user, and all the nodes are commonly grouped in a bus, ring, or star topology, as illustrated in the diagram given below. Nodes in a wireless LAN can broadcast over radio or optical connections.
Network Access
In a broadcast network, where every node can hear every transmission, a process must be devised for allocating a communications channel to the nodes that have packets to transmit while also preventing collisions from causing destructive interference (simultaneous transmissions). Multiple access communication can be established through scheduling (a method in which nodes broadcast in a systematic ordered succession at regular intervals) or through arbitrary access to the channel.
Scheduled Access
Each node is given a time slot in turn when using the time-division multiple access (TDMA) scheduling technique, and it uses the slot if it has something to send. TDMA may not be efficient if specific nodes are significantly busier than others because no data is transferred during the time allotted to silent nodes. In this scenario, it may be possible to construct a reservation system where there are fewer time slots than nodes, and a node only reserves a slot when it is required for transmission.
Random Access
The substantial overhead required for the polling, reservation, token passing operations, and the risk of long inactive periods, when only a few nodes are broadcasting, are all disadvantages of scheduled access schemes. This can cause significant delays in information routing, especially when heavy traffic occurs in various portions of the network at different times, as is common in many actual communications networks. Random-access protocols were created expressly to provide nodes with something to transmit with faster channel access. Although the channel is susceptible to packet collisions under this protocol, several approaches have been developed to mitigate this risk.
Carrier Sense Multiple Access (CSMA)
Carrier senses multiple access(CSMA) is a random-access strategy that reduces the likelihood of collisions. It detects or listens to see if the shared channel for transmission is busy or not and broadcasts if the channel is not busy. Using CMSA protocols, several users or nodes send and receive data via a shared media, such as a single cable, optical fiber linking multiple nodes, or a section of the wireless spectrum. Since nodes detect transmissions before transmitting their frames, frame collisions are reduced. If two nodes discover an idle channel simultaneously, they may commence transmission simultaneously. The frames would get garbled, culminating in a collision. Each node waits a random amount of time before sending again to avoid another collision. CSMA is generally used in packet networks with radio links, such as the amateur radio system.
Spread-Spectrum Multiple Access
Methods have been devised to enable simultaneous transmissions on a broadcast network without necessarily resulting in mutual packet destruction because collisions are detrimental to network performance. Spread-spectrum multiple access (SSMA) is considered one of the most effective. If the channel is not overloaded, simultaneous transmissions in SSMA will only slightly raise the bit error probability for each user. A suitable control code can be used to produce error-free packets. Compared to traditional CSMA, SSMA has more expensive and complex equipment and wider signal bandwidth.
Open Systems Interconnection
The International Organization for Standardization (IOS) developed the open systems interconnection (OSI) model, a conceptual model that enables various communication systems to exchange data via agreed-upon protocols. The OSI, or Open Systems Interconnection, offers a standard for multiple computer systems to be able to communicate with one another. One could think of the OSI Model as a common language for computer networking. Its foundation is the idea that a communication system may be broken down into seven abstract levels, each one built on top of the previous.
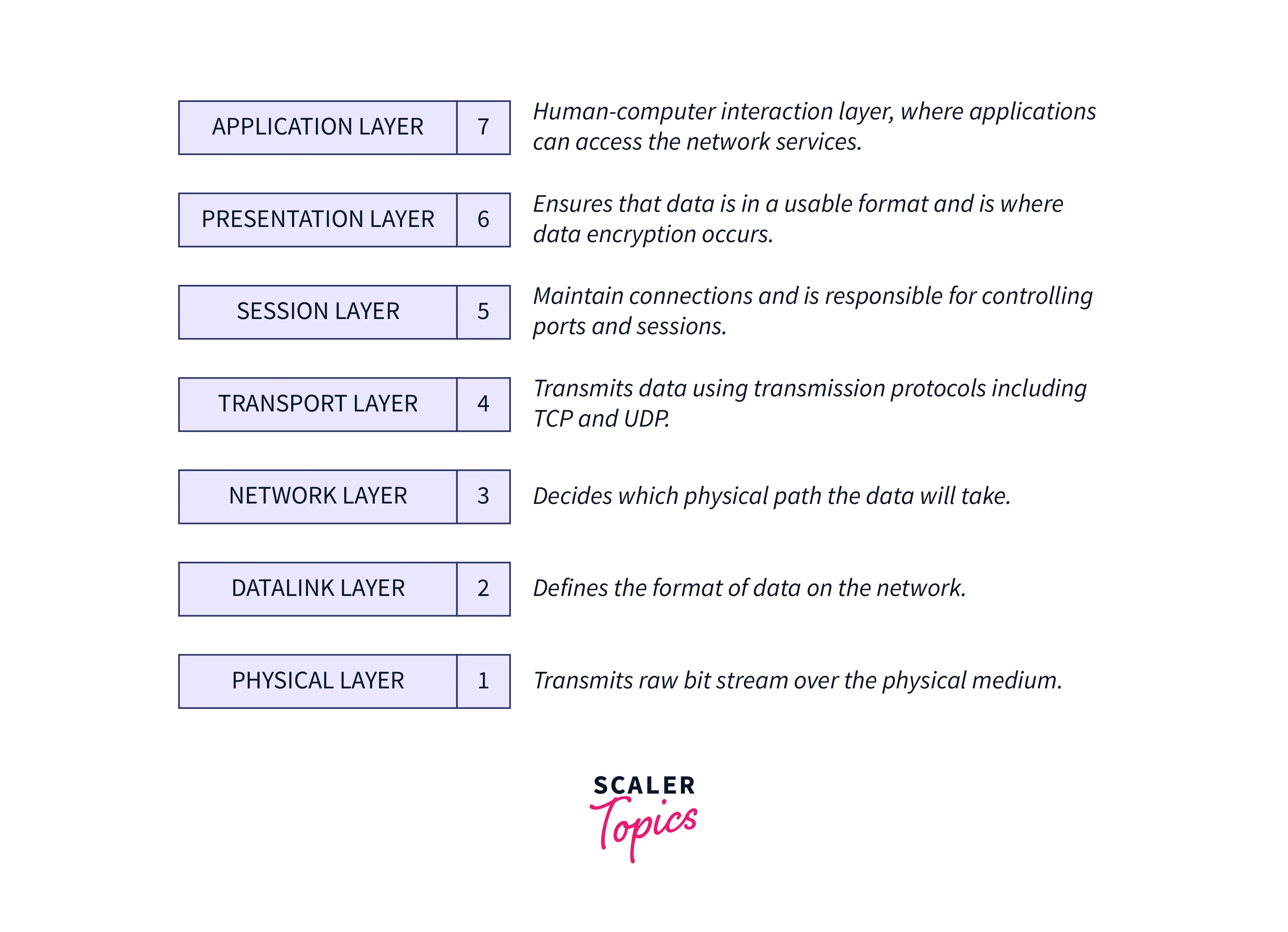
Data Recognization and Use
- The application layer directly interacts with user data. For example, web browsers and email clients rely on the application layer to establish communications. However, it should be noted that client software applications are not part of the application layer; instead, the application layer is responsible for the protocols and data processing on which the software relies to deliver meaningful data to the user.
- On the other hand, the presentation layer completes tasks that are needed frequently enough to justify a general explanation. These operations are frequently added to a software library accessible by numerous users using various applications. Text conversion, data compression, and data encryption are a few examples.
- The session layer that provides a user interface with the network also manages the process of connecting to another computer, confirming user authenticity, and establishing a dependable communication process. It also controls the process of connecting to the network. Additionally, this layer ensures that files that multiple network users can change are kept organized.
- The transport layer is responsible for end-to-end communication between the two devices. This includes extracting data from the session layer and segmenting it before sending it to
layer 3. The receiving device’s transport layer is responsible for reassembling the segments into data that the session layer can ingest. The transport layer of the OSI model is also responsible for flow control and error handling. Flow control calculates the best transmission speed to guarantee that a sender with a fast connection does not overcome a receiver with a slow connection. On the receiving end, the transport layer handles error control by checking that the data received is complete and requesting retransmission if it isn’t.
Data Transfer
- The network layer separates data into packets and decides how to route the packets within the network, which nodes (if any) will verify the packets for errors along the path, and whether congestion control is required in a frequently used network.
- The data-link layer converts a raw communications channel into a line that looks to the network layer to be practically error-free. This is accomplished by dividing data into data frames, transferring them sequentially, and processing acknowledgment frames received back to the source by the destination. This layer defines frame boundaries and provides recovery processes for lost, damaged, or duplicated frames.
- The physical layer contains the transmission medium and several electrical and mechanical parameters.
Telecommunications-Industry-And-Service-Providers
Telecommunications systems are often managed and operated by telecommunications service providers, also known as communications service providers. Historically, these providers provided telephone and related services; however, they now offer Internet and WAN services, metropolitan area network (MAN), and worldwide services.
In several nations, telecom service providers were predominantly owned and operated by the government. This is no longer the case, with many being privatized. Although most nations have governing bodies to create and implement telecommunications guidelines, the International Telecommunication Union (ITU) is the United Nations (UN) institution that administers telecommunications and broadcasting regulations. The Federal Communications Commission (FCC) is the major regulatory body in the United States.
Internet service providers (ISPs), telecom equipment providers, cellular service providers, radio and television broadcasters, satellite television providers, cable companies, and managed service providers(MSPs) are among the many organizations that offer various sorts of telecommunications services. Some of the foremost service providers in India are:
- Reliance Rcom
- Reliance Jio
- Indian Airtel
- Vodafone/Idea(VI)
- Qualcomm
- Virgin Mobile
Capacity and Speed
The capacity and speed of telecommunications networks improved similarly to digital computers’ speed and capacity thanks to advancements in semiconductor technology, which are expressed in the transistor density’s biannual doubling and experimentally described by Moore’s law. In telecommunications, this is stated in Edholm's law, which was suggested and named after Phil Edholm in 2004. This empirical law states that the bandwidth of telecommunication networks doubles every 18 months, which has been demonstrated since the 1970s. The trend can be seen in the Internet, cellular (mobile), wireless and wired local area networks (LANs), and personal area networks. This advancement is the result of rapid advancements in metal-oxide-semiconductor technology development.
Conclusion
- Telecommunications, or telecom, is the electronic exchange of information over long distances and includes all forms of voice, data, and video transmission.
- Telecommunication networks may employ several technologies based on circuit switching, message switching, or packet switching approaches to transmit messages and signals.
- Every telecommunications network is theoretically divided into three components or planes.
- Data Plane
- Control Plane
- Management Plane
- Telecommunications systems are often managed and operated by telecommunications service providers, also known as communications service providers.
- The
International Organization for Standardization (IOS)developed theopen systems interconnection (OSI)model, a conceptual model that enables various communication systems to exchange data via agreed-upon protocols. - Telecommunications systems are often managed and operated by telecommunications service providers, also known as communications service providers. But in several nations, telecom service providers were predominantly owned and operated by the government.
Scheduled Access, Random Access, Carrier Sense Multiple Access(CSMA), andSpread-spectrum multipleaccess are four major network access algorithms.
