TELNET is an acronym for TErminaL-NETwork. It is a form of protocol that makes it possible for one computer to connect to a nearby computer. It is employed as a common TCP/IP protocol for the virtual terminal service provided by ISO. The local computer is the one that establishes the connection. A remote computer is a computer that is connected to, i.e., one that accepts the connection. When the local and distant computers first connect. Telnet uses the client/server model to operate. Telnet client software is used on the local computer, and telnet server software is used on remote systems.
:::
:::section{.main}
Introduction to TELNET
- The primary function of the internet is to offer services to users. For instance, users could wish to execute various application programs at a distant site and transmit the results to the local site. A client-server application, like
FTPorSMTP, is needed for this. However, this would prevent us from designing a unique program to meet every requirement. - The best option is to offer a broad client-server program that enables users to access any application program on a distant machine. Consequently, an application that enables users to sign in to distant computers To fulfill such requirements, the well-known client-server application Telnet is employed. Terminal Network is referred to by the acronym telnet. Telnet offers a connection to the distant computer in a method that makes a local terminal appear to be on the remote side. An interactive text-based bidirectional communication capability via a virtual terminal connection is provided by Telnet, an application protocol that is utilized on the Internet or local area network. In an
8-bit byte-oriented data connection using the Transmission Control Protocol, user data is interleaved in-band with Telnet control information (TCP). - A pioneering Internet standard,
STD 8of the Internet Engineering Task Force (IETF), was created in1969with the development of Telnet, which started withRFC 15and was expanded upon inRFC 855. Teletype Network is indicated by the name. A command-line interface on a distant host could previously be accessed with Telnet. However, the use of Telnet for this purpose has dramatically decreased in favor of SSH due to severe security problems when utilizing Telnet over an open network like the Internet. - The program that executes the client portion of the protocol is referred to as telnet in this context. Almost all computer platforms can run client apps for Telnet. Additionally, the verb telnet is employed. To telnet is to create a connection using the Telnet protocol, either using a command-line client or a graphical interface. As an illustration, a typical instruction may be: “To change your password, telnet into the server, log in, then execute the passwd command.”
:::
:::section{.main}
Modes of Operation in TELNET
The different Modes of Operation in TELNET are:
Default Mode
- If no further modes are activated during option negotiation, this mode is utilized.
- In this mode, the client is in charge of echoing.
- As soon as the user inputs a character, the client repeats it on the screen but does not transfer it until the entire line has been typed.
Character Mode
- Each character that is typed in this mode is transferred from the client to the server.
- The character is then echoed by the server so that it may be seen on the client’s screen.
- Only if the transmission duration is very long is the character’s echoing performed.
Line Mode
- The character mode and the default mode both have drawbacks, thus this option is suggested to make up for them.
- This mode allows the client to do line echoing.
- A whole line is then transferred from the client to the server at that point.
:::
:::section{.main}
Types of TELNET Login
Local Login
When someone connects to a local computer, it is known as local login.
When the workstation is using a terminal emulator, the terminal driver takes keystrokes entered by the user. The operating system then starts the necessary application software after receiving these characters from the terminal driver.
On the other hand, the operating system gives special characters a specific meaning.

- Local login is the act of signing into a local computer by a user.
- Keystrokes entered by the user are recognized by the terminal driver when the workstation is running a terminal emulator. These characters are then sent from the terminal driver to the operating system, which ultimately launches the chosen application software.
- The significance of special characters, however, varies depending on the operating system. For instance, under
UNIX, certain character combinations might have specific meanings, such as suspend when the control character is combined with the letter “z.” Situations like these don’t cause any issues because the terminal driver is aware of what these characters imply. However, it can lead to remote login issues.
Remote Login
When a person logs into a distant location, such as a computer, they can access any services that are offered by that computer. This procedure is known as remote log in. A user can comprehend the results of processing that has been transferred from the remote computer to the local computer with the aid of remote login.
How to Login Remotely:
- Local operating system supports character input from the user while using a local computer.
- Characters sent to the TELNET client by the local computer are not translated by it.
- To transmit these characters to the local TCP/IP protocol stack, the TELNET client converts them into a set of characters known as Network Virtual Terminal (NVT) characters, a global character set.
- To reach the TCP/IP stack at a remote computer, commands or text in the form of NVT must travel via the Internet.
- Once the operating system has received the characters, the TELNET server then receives them.
- Then, a TELNET server converts those characters into ones that a distant computer can read.
- The pseudo-terminal driver, a piece of software that makes it appear as though characters are coming from a terminal, sends characters to the remote operating system.
- After that, the operating system sends the character to the proper application software.
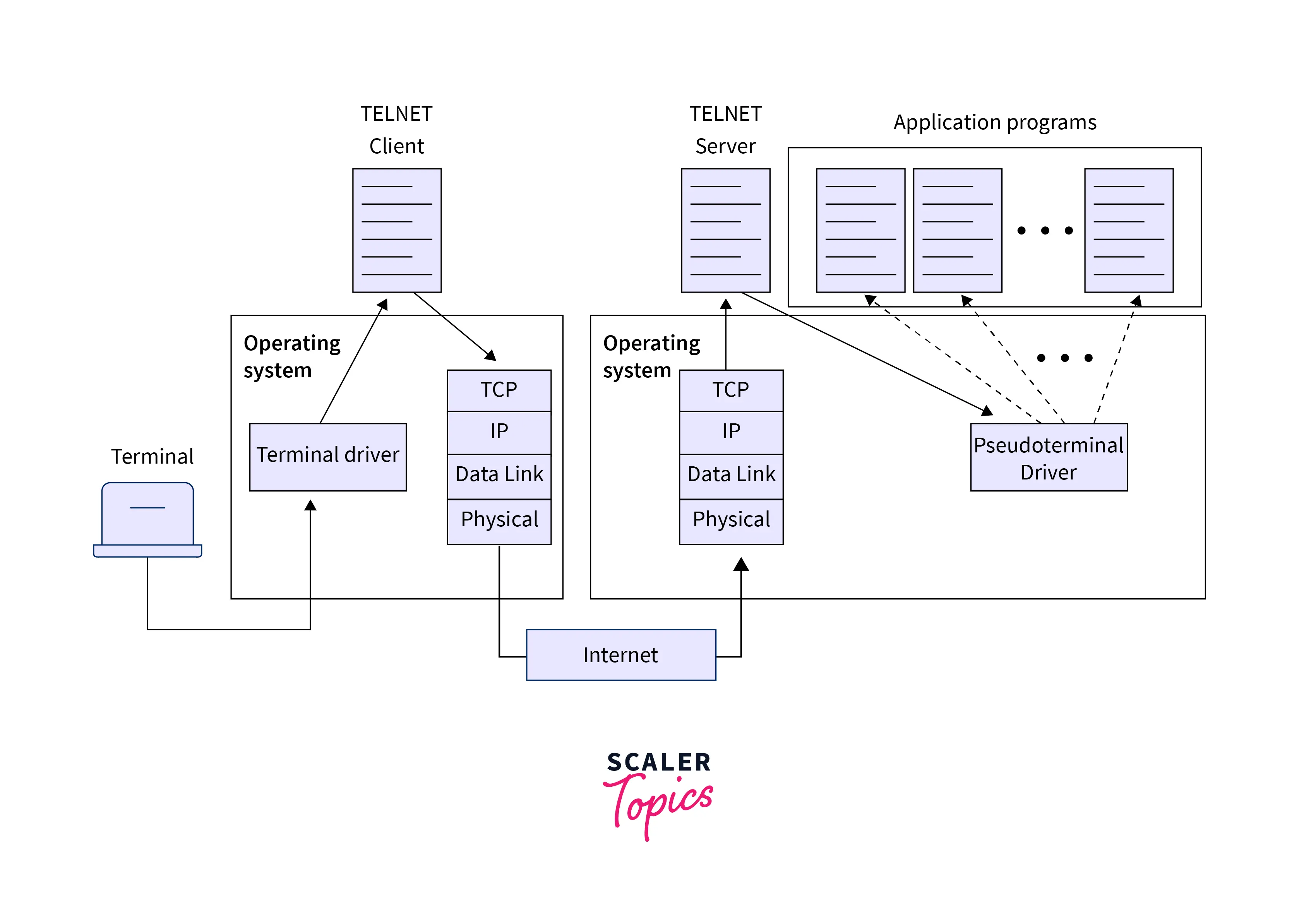
The user must complete a remote login process if they wish to access application software on a remote machine.
How remote login occurs
At the local site
The terminal driver receives the user’s keystrokes and transmits them to the TELNET client, which receives the characters. The TELNET client then sends the characters to the nearby TCP/IP stack, where they are then converted into a common character set known as network virtual terminal characters.
At the remote site
To the remote machine’s TCP/IP, the commands are sent in NVT forms. The operating system in this instance receives the characters before passing them on to the TELNET server. For a distant computer to interpret the characters, the TELNET server changes them. The characters cannot, however, be delivered directly to the operating system since a distant operating system does not receive the characters from the TELNET server. To receive the characters from the TELNET server, some kind of program is needed. When the application software is needed, the operating system sends these characters to it.
Commands in TELNET
It was created in 1969 to give users a command-line interface for connecting to servers or distant devices and establishing communication. However, it is occasionally used as a remote management tool as well as for initial device configuration, such as for network devices. From a security perspective, Telnet itself has several significant issues that we shall cover in more detail later. Its lack of encryption, though, makes it rather out of date in terms of contemporary security, and this is the biggest problem with it. It would not be entirely accurate to say that it is out of date because the internet had not undergone such a significant transformation when it was created.
Telnet has been regarded as a suitable protocol for network and server administrators for a very long time. Because the majority of devices at the time supported it, its ability to remotely manage networked devices is especially helpful for administrative activities (or operations).
Additionally, it may be used to send an email directly from the servers to verify the availability of the ports (or to check the ports) and immediately discover issues on the email server.
One of the most effective and efficient ways to configure servers is the Telnet solution.
Here, we’ll go over a few of the most essential and often-used commands for Telnet, which clients utilize to establish connections.
telnet hostname As soon as the user has supplied their login and password, the connection is typically set up or started using this command. The control device needs user recognition to support Telnet. Device names on a network are represented by entry hostnames. The following command can also be used by a user to indicate the right IP address and connection request over the specified port.
telnet IP-address port number Here are some other basic actions that may be somewhat extended by the user with parameters and are executed using telnet commands:
| Command | Description |
|---|---|
| ? | To access the help menu, use this. To end the current telnet connection, use this command. |
| close | The telnet connection and all other open connections are immediately terminated when this command is used. |
| Quit | To indicate the transmission type, it is utilized. Text files and binary files are two examples. |
| mode type | Typically, it is employed to create a new connection on the given host by using the already established one. |
| open hostname | Typically, it is employed to create a new connection on the given host by using the already established one. |
| display argument | The many sorts of active connections, including the terminal, type of port, etc., are displayed. |
| Environ argument | It once served as a definition for the operating system’s relevant (or presently used) variables. |
| Send argument | To the host, it transmits the chosen, typical telnet character string. |
| set argument | Changes to the connection’s parameters are made using it. |
| unset | It’s employed to load the connection settings that have already been set. |
TELNET Command Options
telnet
| Option | Description |
|---|---|
| -d | turns on debug mode. |
| -a | tries to log in automatically. |
| -n tracefile | Opens the trace file so that the proper data may be recorded (also see “set trace file”). |
| -l user | You will be logged in as the designated user if the host supports environ. |
| -e escape char | Creates an escape character. |
| -E | No character is recognized as an escape character. |
| -x | Attempts to turn on encryption |
mode
| Option | Description |
|---|---|
| character | LINEMODE is disabled. |
| Line | activates LINEMODE. |
| isig/-is | enables/disables LINEMODE’s TRAPSIG mode. |
| edit/-edit | enables or disables LineMode’s EDIT mode. |
| softtabs/-softtabs | Activates or deactivates LINEMODE’s SOFT TABS mode. |
| litecho/-litecho | enables/disables LINEMODE’s LIT ECHO-Modus. |
send
| Option | Description |
|---|---|
| abort | sends a “Process Abort” sequence. |
| Ao | Sends a “Abort output” sequence, after which the host flushes its output to the client. |
| ayt | Sends a “Are you there?” message; the recipient can confirm by responding. |
| brk | “Break” sequence is sent. |
| ec | Sending a “Erase character” sequence causes the host to delete the most recent character input. |
| el | The host deletes the line that is being typed after receiving the Erase line sequence. |
| eof | the “End of file” sequence is sent. |
| eor | the “End of record” sequence is sent. |
| esc | transmits the presently used escape character (also known as “telnet -e”). |
| ga | sends the “Go ahead” signal. |
| getstatus | requests that any input that has not yet been processed be discarded by the host. |
| ? | Information regarding the send command is provided. |
set/unset(value can be TRUE/FALSE or a special character)
| Option | Description |
|---|---|
| echo value | determines whether the typed characters should be shown as well. |
| eof value | enables the “End of file” character (also known as the “send eof” character). |
| erase value | Activates erase character; only effective in localchars mode (see also “toggle localchars”); see also “send ec” |
| escape value | Escape character is enabled (see also “telnet -e”). |
| flushoutput value | Abort output character is enabled (see also “send ao”); this feature only operates when localchars is selected (see also “toggle localchars”). |
| lnext value | “lnext” characters are enabled. |
| quit value | enables “break” characters; only effective in localchars mode (see also “send brk”) (see also toggle localchars). |
| reprint value | “Reprint” character is enabled. |
| start value | The “start” character is enabled, but only if TOGGLE-FLOW-CONTROL is active. |
| stop value | The “stop” character is enabled, but only if TOGGLE-FLOW-CONTROL is on. |
| worderase value | ” Worderase” characters are enabled. |
environ
| Option | Description |
|---|---|
| define variable value | Values can be contained in single or double quotes when assigning a value to a variable. |
| undefine variable | the given variable is deleted. |
| export variable | sends the supplied variable overseas. |
| unexport variable | Declares that the export of the specified variable is only permitted when Telnet is expressly asked to do so. |
| list | The * character specifies whether a variable is automatically exported when it lists all variables. |
| ? | Gives details about the send command. |
toggle (Initial state is TRUE)
| Option | Description |
|---|---|
| autosynch | When the quit character is transmitted (see also “set quit”), an additional “synch” sequence is sent if both autosynch and localchars are activated. |
| binary | binary option on input and output is enabled or disabled. |
| inbinary | The “binary” option is enabled or disabled upon input. |
| outbinary | binary option is enabled or disabled on the output. |
| crlf | TRUE: The carriage return setting is . |
| crmod | FALSE: The carriage return setting is . (FALSE is the usual state in this case.) |
| debug | changes the “carriage return” mode’s status. |
| localchars | changes the “Socket debug” mode’s status (FALSE is the normal state here). |
Common Uses for TELNET
Telnet may be used to access a server and do a range of tasks, such as changing files, executing applications, and checking email.
Some servers allow remote connections with Telnet, allowing users to access open data to access basic games or look for weather reports. The fact that many of these functions still work with earlier systems that require access to particular data or are nostalgically appealing is one reason why they are included.
Telnet allows users to connect to any program, including web servers and ports, that uses text-based, unencrypted protocols. The telnet connection will ping the port to determine if it is open or not when users open a command prompt on the remote system, type the word telnet, and the name or IP address of the remote machine. A blank screen indicates that a port is open, whereas an error message indicating that a port is connecting indicates that a port is closed.
Here are some applications for telnet:
- For Unix, Linux, and Windows, there are two free CLI programs called
PuTTYandplinkthat offer SSH, rlogin, Telnet, and raw TCP clients. - Inline Browser
- Software by Van Dyke Georgia SoftWorks GSW ConnectBot SecureCRT
- An application that supports SSHv2, RLogin, Telnet, Serial, platforms for *nix, Windows, and Mac OS X, as well as various BBS terminal emulators
- The
ANSI-BBSis the primary usage of the NetRunner BBS telnet client. Emulation that is mostly accurate and transparent is provided using an SDL2-focused emulation engine. - NCSA Telnet
- Given that telnet offers a comparable level of functionality for hosts that are protected by a firewall, TeraTerm Rtelnet is a SOCKS version of telnet.
- virtual terminal
RUMBA - Telnet client and server are included in
Inetutilsonce more. - Another CLI tool,
exe, is installed by default with Windows.
Advantages of TELNET
The client can be used to utilize or test other services that rely on TCP as a transport protocol as Telnet connections are essentially regular TCP connections. For instance, a straightforward request may be used to examine the operation of an HTTP server or, as was already indicated, the status of an email server.
The fact that the connection protocol may be utilized on many systems adds to this adaptability. Only a small number of devices do not adhere to the approved IETF standard. It makes no difference if the client and server machines use the same operating system. If authorization has been granted, Telnet also has the benefit of enabling unlimited access to the resources of a managed system.
- Universal: Telnet may be used with many different operating systems. Connecting to newer devices running various operating system versions is possible even with older hardware.
- To be more precise, Telnet enables you to test access from a computer on your school’s network to a set of ports on an external server.
- Configuration of networking devices is possible using a Telnet connection to switches and routers.
- It has the capability of transmitting and receiving data.
- It allows user authentication and aids in the administration of the network’s components.
- Every telnet client and server uses a network virtual terminal (NVT).
- On a shared basis, distant computers employ automation test facilities. Restricting the usage of pricey test facilities and equipment at a few key locations for users everywhere reduces costs.
Disadvantages of TELNET
Telnet poses a serious security concern since neither the establishment of the connection nor the transit of data is encrypted when utilizing the Telnet protocol. Therefore, whatever text you submit, including the login credentials needed for remote access, is susceptible to being seen by unauthorized people. This implies that gaining control of the system won’t be too difficult for hackers. Secure Shell is a reliable replacement for Telnet (SSH).
The following are TELNET’s downsides or disadvantages:
User IDandpasswordare communicated in clear text. This increases the security risk of the Telnet protocol by making it simpler for hackers or attackers to execute listening and snooping.- Since Telnet is a character-based communication method, it is not possible to use
GUI-basedtools through Telnet connections. Cursor motions and other GUI data cannot be sent. - It is a pretty ineffective protocol.
- Each keystroke must pass through numerous context changes before it can be used again.
- Because of the sluggish typing speed, it is pricey.
- The Telnet Protocol allows for the transmission of encryption commands together with a User ID and Password.
- Security risks exist with the Telnet protocol since hackers and attackers are lax about spying and listening.
- On the Internet, it is a protocol that is highly ineffective.
- Because of sluggish typing rates, it is expensive.
Conclusion
- A client-server protocol called Telnet is based on character-oriented data transfer across TCP connections. Telnet enables text-based input and output on computers for remote control.
- The Telnet client, which acts as the controlling element in this process and is sometimes referred to as remote access or remote login, may be installed on both specialized hardware and regular computers. The appearance of the transferred data information varies, nevertheless, depending on the terminal device.
- Every time you want to connect to a different computer or network component, Telnet is a must. The text-based command line is used for everything. This was particularly useful in the past when mainframe computers’ services were being shared. However, although being used less and less frequently, Telnet is still used to administer networks, access programs, and share databases today.
- It assertively positions itself as a networking protocol alongside a piece of software that enables access to remote computers and terminals through the internet. a platform that is adaptable and expandable and is thought to be sustained for many more years.
- The Telnet protocol has long been the industry standard for remote connections due to its usefulness and ease of use. The protocol is now, however, inappropriate and unsatisfactory in many situations due to rising demands for the security of controlled and transmitted data. The Secure Shell (SSH) protocol, which uses encryption and public-key authentication, provides the foundation for most remote connections on the Internet today. For machines with constrained operating systems that cannot run SSH servers, Telnet is still a viable option.
PuTTyis a well-liked client application that streamlines remote access based on both protocols. - The biggest issue with Telnet is its security holes. Without encryption, the data is sent over the network. It makes it possible for spies to acquire information like user names and passwords. Because of this, Secure Shell (SSH), a type of encrypted [telnet], first appeared in the middle of the
1990s.