A VPN (virtual private network) is a service that establishes a secure, encrypted online connection. A VPN establishes a virtual connection between your device and a distant server managed by a VPN service. This connection establishes a secure point-to-point tunnel that encodes your personal information, conceals your IP address, and enables you to bypass online barriers and firewalls. VPNs are widely used for virtual privacy by normal internet users and firms.
Different Types of VPN and Their Use Cases
Generally, there are eight major types of virtual private networks (VPNs). Let’s discuss them briefly:
1. Remote Access VPN
A remote access virtual private network allows users to connect to a secure network remotely using a virtual private network (VPN). Employees who need to access their company’s network from distant locations or people who want to connect to a private network from a public area safely typically use this type of VPN. Individuals using VPN services for personal or home use commonly rely on them to bypass geographical internet restrictions and access blocked websites. In addition, users who prioritize internet security often employ VPN services to bolster their online privacy and enhance their overall internet security.
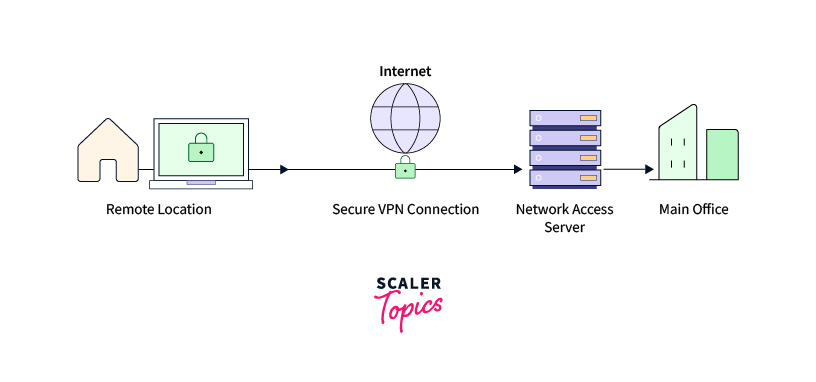
Remote access VPNs operate by securing or encrypting information transmitted between an outside user and your organization’s internal network. No matter where the user is, these VPNs create private tunnels connecting a company’s network with a remote user.
2. Site-to-Site VPN
A Site-to-Site virtual private network, also called Router-to-Router VPN, refers to a connection established between two or more networks. Site-to-site VPNs are valuable for organizations operating across multiple offices scattered over vast geographical areas. For example, a corporate network in which different offices collaborate or a branch office network with a central office and multiple branch locations.
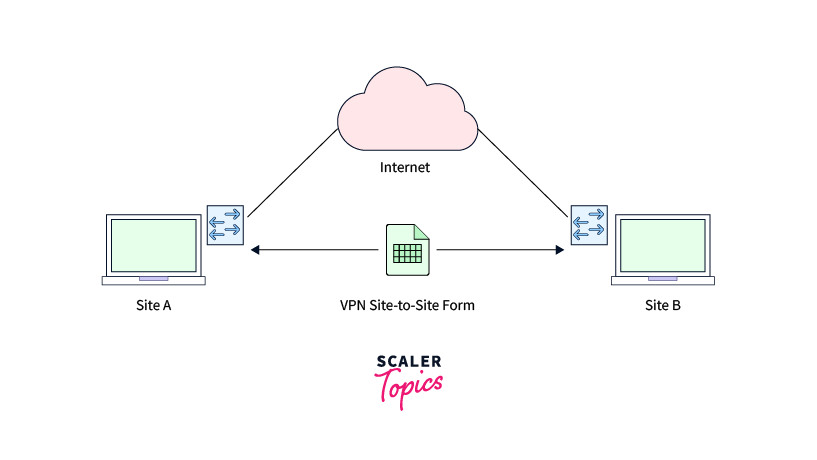
There are two types of site-to-site VPN:
- Intranet-based VPN:
An intranet-based Site-to-Site VPN establishes connections between multiple local-area networks (LANs), effectively creating a wide-area network (WAN). So when the company’s various offices are connected using Site-to-Site VPN, then it is called intranet-based Site-to-Site VPN. - Extranet-based site-to-site:
These VPNs are frequently utilized by two or more distinct organizations that wish to share some resources while maintaining the privacy of others. When using an extranet-based site-to-site VPN, each organization connects to the VPN and selects the information they wish to make available to the other businesses. They can work together and discuss without disclosing confidential information in this way.
3. Cloud VPN
A Cloud VPN is a technology that securely connects users or devices to cloud-based resources. It ensures secure communication by encrypting data transmission and connects remote users to cloud-based resources using the internet as the primary transport medium. Cloud VPNs are commonly provided as services by cloud providers like Amazon Web Services (AWS) and Microsoft Azure. They utilize the same encryption and security protocols like IPsec or SSL, ensuring the confidentiality and security of data transferred through the VPN.
4. Mobile VPN
A mobile VPN is a technology that establishes a secure and encrypted connection for mobile devices, such as smartphones or tablets, to access resources on a private network or the internet. The term “Mobile VPN” can lead to misunderstanding, as VPNs apply to various devices, including mobile phones. In this context, the term “mobile” pertains to its capability to adapt connections and maintain the virtual network even when the connection fails.
Consider a scenario in which an employee works remotely using their laptop while off-site and relies on mobile data for connectivity. Later, they return to their home office and switch to the Wi-Fi network. Despite potential changes in IP address or temporary connection interruptions during this transition, their secure encrypted connection to the office remains uninterrupted and intact.
5. SSL VPN
An SSL VPN (Secure Sockets Layer Virtual Private Network) is a specific type of VPN that employs the SSL protocol to ensure a secure connection between users and the VPN server. It enables remote users to access a private network securely by creating an encrypted pathway between their device and the VPN server. SSL VPNs provide greater security than traditional IPsec VPNs since they use the same encryption methods as HTTPS, which secures online transactions.
6. PPTP (Point-to-Point Tunneling Protocol) VPN
PPTP, or Point-to-Point Tunneling Protocol, is a VPN (Virtual Private Network) protocol that allows remote users to communicate with a private network over the internet securely. PPTP creates a virtual tunnel for data transfer, allowing users to access private resources as if they were directly connected, even though they are physically separated.
7. L2TP (Layer 2 Tunneling Protocol) VPN
To establish a secure connection between two computers, L2TP (Layer 2 Tunneling Protocol) encapsulates the data packets that are being exchanged between them. It uses a better encryption technique and is an extension of PPTP. L2TP increases the security of the VPN connection by combining PPTP and L2F (Layer 2 Forwarding Protocol). L2TP doesn’t require additional software to be installed on the client’s device and is relatively simple to set up.
8. OpenVPN
OpenVPN is a free and open-source software application and protocol for establishing secure, encrypted Virtual Private Networks (VPNs). It enables secure communication over the internet between individuals and networks, ensuring data confidentiality and integrity. OpenVPN uses several encryption techniques to create a private tunnel via which data can be sent. OpenVPN is considered one of the most secure and versatile VPN solutions available.
Different Types of VPN Protocols
a.) Internet Protocol Security (IPSec)
IPSec is a VPN tunneling protocol that enforces session authentication and data packet encryption to secure data sharing. The encrypted message is contained within the data packet, which is further encrypted. The IPSec protocol combines with other protocols to enhance security and is often used in Site-to-site VPN setups due to its high compatibility. The IPSec protocol runs in 2 modes:
- Transport mode
- Tunneling mode
b.) Layer 2 Tunneling Protocol (L2TP)
L2TP (Layer 2 Tunneling Protocol) is a tunneling protocol frequently used with another VPN security protocol, such as IPSec, to establish a highly secure VPN connection. L2TP forms a tunnel connecting two L2TP connection points, while the IPSec protocol encrypts data and ensures safe communication within the tunnel.
c.) Point–to–Point-to-Point tunneling Protocol (PPTP)
PPTP is a different tunneling protocol that establishes a secure tunnel using a PPTP cipher. However, due to the significant growth in computing power and cyber attacks since the ’90s, it would take a little while to crack the cipher through brute force and access the exchanged data. As a result, this cipher is scarcely used in modern technology. Instead, there’s a preference for more secure tunneling protocols featuring advanced encryption.
d.) SSL and TLS
HTTPS web pages are encrypted using the Secure Socket Layer (SSL) and Transport Layer Security (TSL) protocols. As a result, the web browser serves as the client, and user access is restricted to specific applications rather than the entire network. Almost all browsers come equipped with SSL and TLS connections, so no addition is required to use SSL and TLS. SSL/TLS is commonly used in remote access VPNs.
e.) Secure Shell (SSH)
SSH establishes the VPN tunnel over which data is transferred and ensures the tunnel is encrypted. A SSH client creates SSH connections, and data is sent from a local port to the distant server over an encrypted tunnel. It is useful for remotely accessing your office desktop from your home laptop.
f.) SSTP (Secure Socket Tunneling Protocol)
The SSTP is a VPN protocol that establishes a tunnel between a client device and a server. Its primary purpose is to ensure safe remote access to private networks via the Internet. Microsoft introduced SSTP as a replacement for the less secure PPTP and L2TP/IPSec protocols as SSTP uses SSL/TLS and default TCP port 443, SSTP is better than PPTP (Point-to-Point Tunneling Protocol).
g.) IKEv2 (Internet Key Exchange Version 2)
IKE version 2 is an improvement to the Internet key exchange protocol. It is a VPN protocol that allows for quick and secure connections but is not generally supported by VPN providers.
h.) OpenVPN
OpenVPN is an open-source SSL/TLS framework improvement that adds extra cryptographic algorithms to make your encrypted tunnel even more secure. Due to its great security and efficiency, it is the most commonly used tunneling protocol.
i.) WireGuard
Wireguard is the latest tunneling protocol, now widely accessible, and is simpler yet notably more efficient and secure than IPSec and OpenVPN. It utilizes streamlined code to achieve optimal performance with minimal room for error. Though still in its early adoption phase, you might come across offices employing WireGuard-based Site-to-site connections.
Which VPN Protocol is Best for You?
- When selecting a VPN protocol, first determine your setup type: remote access or site-to-site.
- Consider your business needs and network requirements, including risk model, traffic load, and data accessibility.
- WireGuard, L2TP, SSL/TLS, and OpenVPN are safe for
remote access. - For site-to-site, the choice may depend on existing hardware compatibility. If you already have routers that support OpenVPN, it may make more sense to keep them rather than replace them with ones that can handle Wireguard.
Conclusion
- A VPN (virtual private network) is a service that establishes a secure, encrypted online connection.
- VPNs are widely used for virtual privacy by normal internet users and firms. Organizations can use VPNs to ensure that outside users who access their data center are authorized and using encrypted channels.
- A remote access virtual private network allows users to connect to a secure network remotely using a virtual private network (VPN).
- A Site-to-Site virtual private network, also called Router-to-Router VPN, refers to a connection established between two or more networks.
- IPSec is a VPN tunneling protocol that enforces session authentication and data packet encryption to secure data sharing.
- PPTP (Point–to–Point Tunneling Protocol) is a different tunneling protocol that establishes a secure tunnel using a PPTP cipher.
- OpenVPN is an open-source SSL/TLS framework improvement that adds extra cryptographic algorithms to make your encrypted tunnel even more secure.
WireGuard, L2TP, SSL/TLS, andOpenVPNare the best VPN options for remote access setups.- For the site-to-site, the choice depends entirely on existing hardware compatibility.
