The Native VLAN functions as a conduit for untagged data across a trunk port. If untagged data arrives at a trunk port, the switch inherently assigns it to the native VLAN. The Native VLAN refers to the default VLAN for an Ethernet trunk (a link or port that carries traffic for multiple VLANs) when no VLAN information is explicitly specified or tagged on the frames. In other words, it’s the VLAN to which untagged traffic belongs on a trunk port.
Native VLAN
Native VLAN refers to VLAN services that have been designed with backward compatibility in order to accommodate older devices that do not support VLANs. Native VLAN does not have a network tag, therefore older devices can simply recognize when trunk lines are sent. The switches can be set up using the dot IQ concept, which is an 802.1Q tunneling frame. The switch port trunk native VLAN command is used to configure native VLAN. Native VLANs are identified if they are not associated with any trunks. It is not essential to have native VLAN on the trunk.
Note:
- Untagged ports/Access Ports link individual end devices such as PCs, servers, or printers, to a designated VLAN. Each of these ports belongs to a specific VLAN and can only carry traffic intended for that VLAN. The data sent through an untagged port does not have a VLAN ID attached to it.
- Trunk ports/tagged ports connect switches and transport data for multiple VLANs over a single link. Data sent over a trunk port is labeled with a VLAN ID, allowing switches to determine the appropriate VLAN for the data and route it accordingly. Cisco uses the terms
accessandtrunk, but HP usesuntaggedandtaggedports to denote the same concept.
How does It Work?
Let’s take a simple example to understand the workings of native VLAN. The diagram portrays a setup wherein multiple personal computers (PCs) are interconnected via switches and a hub. Notably, Switch1 and Switch2 are linked together. Additionally, the hub is interconnected with numerous PCs and is also linked to Switch2. In this scenario, we establish a connection with the hub and discover a trunk link connecting Switch1 and Switch2.
Imagine that a specific type of data traffic, labeled as 10, arrives at Switch1. Before this traffic is sent through the trunk link, it undergoes a process known as frame tagging. This tagging step is crucial because it enables Switch2 to correctly identify the Virtual LAN (VLAN) to which the frame belongs. As a result, Switch2 can effectively direct the frame only through the appropriate ports associated with that VLAN. However, there are situations where frames arrive without any tags. This is particularly common when frames are received through a HUB, as HUBs don’t support the tagging concept. In these instances, Switch1 assumes that the frame is meant for the native VLAN and consequently forwards it to that VLAN by default.
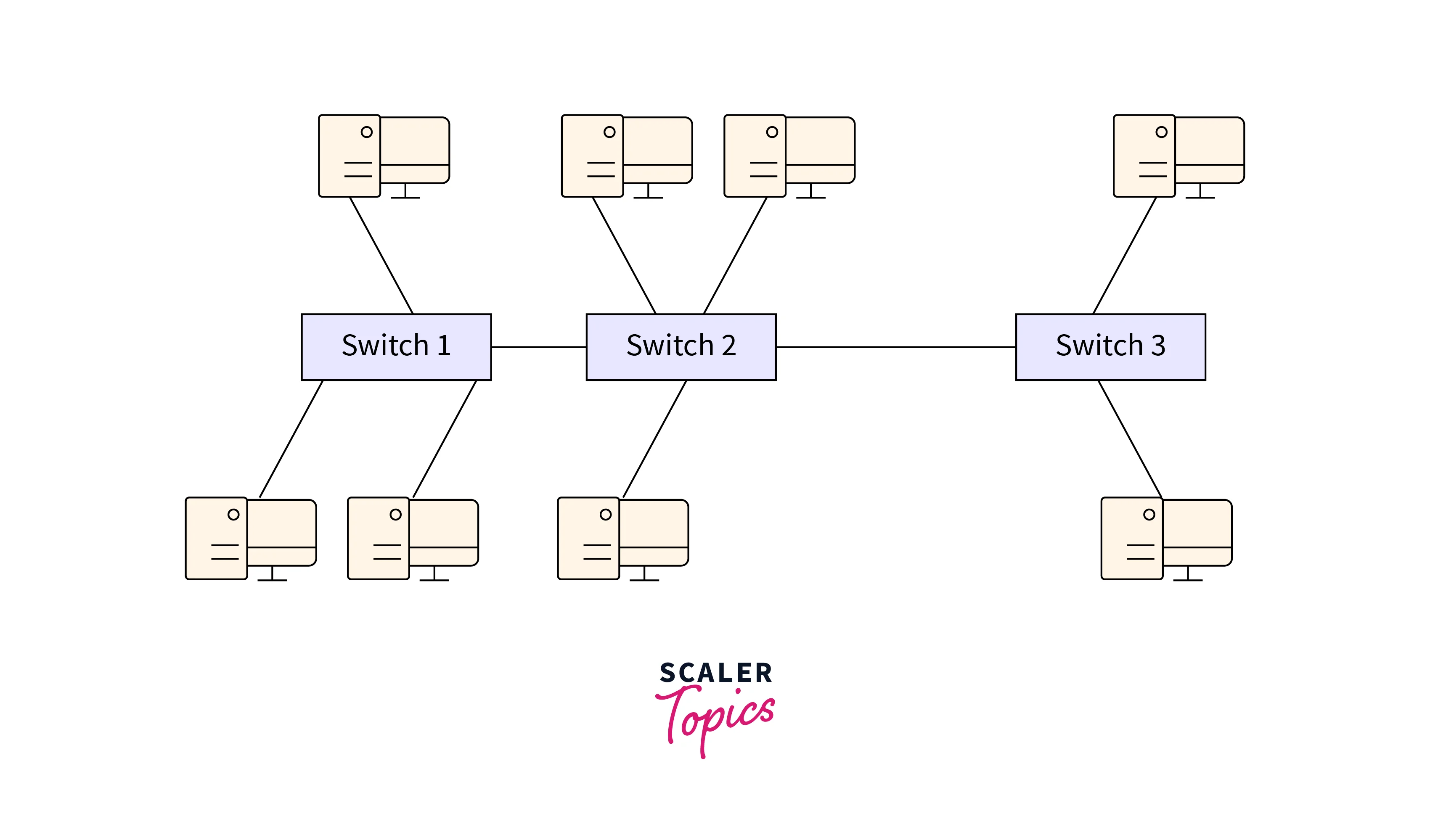
In this context, it’s important to note that endpoints cannot comprehend VLAN concepts. Therefore, an access port is designed to receive untagged traffic. This means that when untagged data arrives at an access port, the switch connects that traffic with the VLAN linked to that specific port. On the other hand, trunk ports are engineered to handle tagged traffic. When traffic arrives at a trunk port, it’s expected to be accompanied by tags that provide VLAN information. The switch then utilizes this VLAN information to make determinations about which VLAN to associate the incoming traffic with. This demarcation between access and trunk ports is pivotal in maintaining proper VLAN associations within the network.
If a switch gets a frame without a tag, it will assume it is a native VLAN. Trunks only carry tagged frames and are used to convey data between VLANs. To verify this, we can use the ping command. There is only one native VLAN per trunk, and it must match on both ends of the trunk, which are responsible for all untagged traffic.
Importance of Native VLAN
Let’s discuss the importance of Native VLAN.
- Dual Role: The Native VLAN is a genuine VLAN with its members. It handles both encapsulated (tagged) frames and untagged ones.
- Untagged Frame Management: It ensures untagged frames, without an assigned VLAN, are appropriately handled. These frames can be directed to the intended VLAN.
- Effective Forwarding: A switch on a trunk port can forward any layer 2 frame, tagged or not, to the correct VLAN. Unencapsulated frames on a trunk are discarded.
- Encapsulation and Security: Frames transmitted via the trunk port are encapsulated. This foils VLAN hopping attacks, redirecting attackers to an inactive VLAN.
- PVID Identification: Each physical port is linked to a Port VLAN Identifier (PVID). Untagged frames are assigned to this PVID.
- Versatile Traffic Handling: Native VLAN handles tagged and untagged traffic from various VLANs, enhancing compatibility.
- Best Practices: Opting for a Native VLAN other than VLAN1 enhances security and networking efficiency.
:
Native VLAN Use Cases
Consider an Access Point (AP) that is connected to a switch through a trunk port. This wireless access point supports two wireless networks: Office-WiFi on VLAN 10 and Guest-WiFi on VLAN 15. The AP’s management traffic, which is assigned to VLAN 100, makes use of the trunk port’s native VLAN. This guarantees that untagged management traffic is labeled with VLAN 100 for accurate forwarding.
To establish this setup, the switch’s port connecting to the AP is configured as a trunk port. VLANs 10 and 15 are permitted for traffic passage. Additionally, VLAN 100 is set as the native VLAN, streamlining untagged management traffic’s journey by attaching it to VLAN 100 before onward transmission.
Native VLAN Mismatch
The configuration of the Trunk interface is specific to each location. This implies that the settings on one end of the link don’t need to precisely match those on the opposite end. For instance, one side could have native VLAN 10 while the other side uses VLAN 20 on a single trunk link. However, this mismatch creates a problematic state known as a Native VLAN mismatch. Cisco’s proprietary CDP protocol can identify this error and provide error messages accordingly. It’s important to note that if CDP is turned off, the switch won’t automatically identify this misconfiguration.
A Native VLAN mismatch can lead to significant problems and security risks, including:
- Traffic Misdirection: Frames from the configured Native VLAN travel untagged over the trunk. Upon arrival, due to differing trunk settings, they can end up being forwarded to an unintended VLAN, confusing.
- VLAN Hopping: This misconfiguration could enable malicious traffic to cross VLAN boundaries, potentially breaching network security measures.
Difference between Default VLAN and Native VLAN
Let’s look at the key differences between default VLAN and Native VLAN.
| Serial No. | Basis of comparison | Native VLAN | Default VLAN |
|---|---|---|---|
| 1. | Modification | Native VLAN is set to VLAN 1 by default, although it can be changed to any VLAN. | The default VLAN is always VLAN 1, and it cannot be modified. |
| 2. | Disabling of VLAN | It is possible to disable VLAN. | The Default VLAN cannot be disabled. |
| 3. | Untagged traffic | Traffic can be sent regardless of whether the Default and Native VLANs are the same or different. | When both the Default and Native VLANs are the same, traffic is sent. |
| 4. | Encapsulation type | It only supports .1Q. | It supports .1Q as well as ISL. |
| 5. | Max Number of VLANs per switch | There can be as many native VLANs as there are .1Q trunks on the switch. | One default VLAN per switch. |
| 6. | Operand | Native VLAN is specified through the NATIVE operand command. | The VLAN operand command specifies the default VLAN. |
| 7. | Tagging | Tagging is possible in Native VLAN if necessary, but it is untagged by default. | Tagging is allowed in default VLAN. |
Configuring and Verifying Native VLAN on a Trunk Port
Initially, let’s examine how to verify the active mode and native VLAN of a trunk port by employing the command show interface switchport.
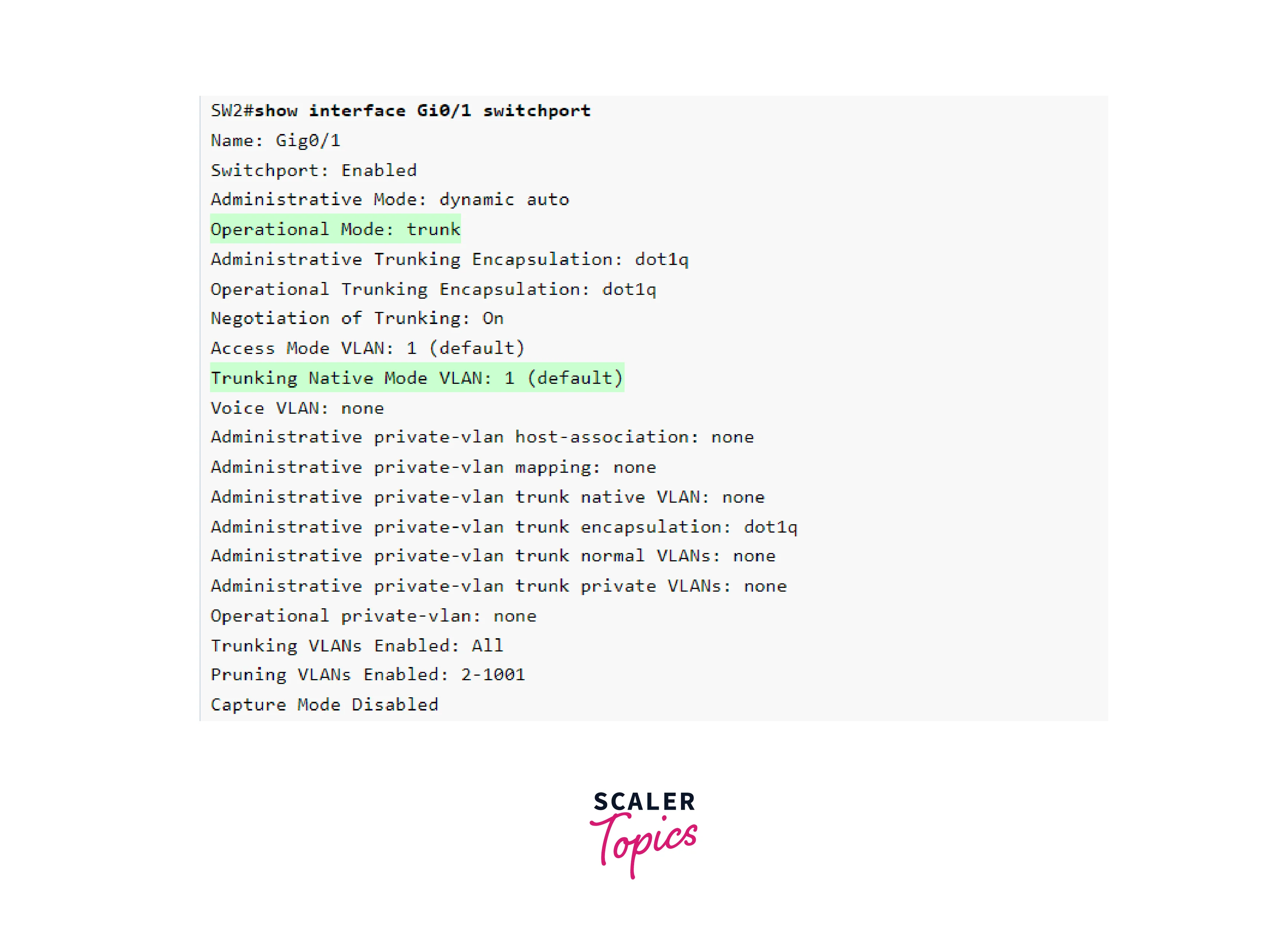
VLAN 1 is the Native VLAN by default. However, this can be changed with the switchport trunk native vlan command in interface configuration mode. Keep in mind that this configuration is unique to each location and it must be manually aligned on both ends of the trunk link to avoid a faulty state.

Allowed VLANs on a Trunk Port
By default, frames from all VLANs are routed over the trunk link on Cisco switches. Nevertheless, it’s possible to specify the precise VLAN numbers that should traverse the link. There are various scenarios where allowing only specific VLANs is preferred over transmitting all VLANs. For instance, in Figure 4, the left switch has VLANs 10, 20, 30, and 40, while the right switch has VLANs 10, 20, 50, and 60. To efficiently utilize the trunk link, you’d likely choose to transfer only traffic from VLANs 10 and 20. This is achieved through the “switchport trunk allowed vlan” feature. Let’s configure the link in Figure to exclusively transmit frames from VLANs 10 and 20.
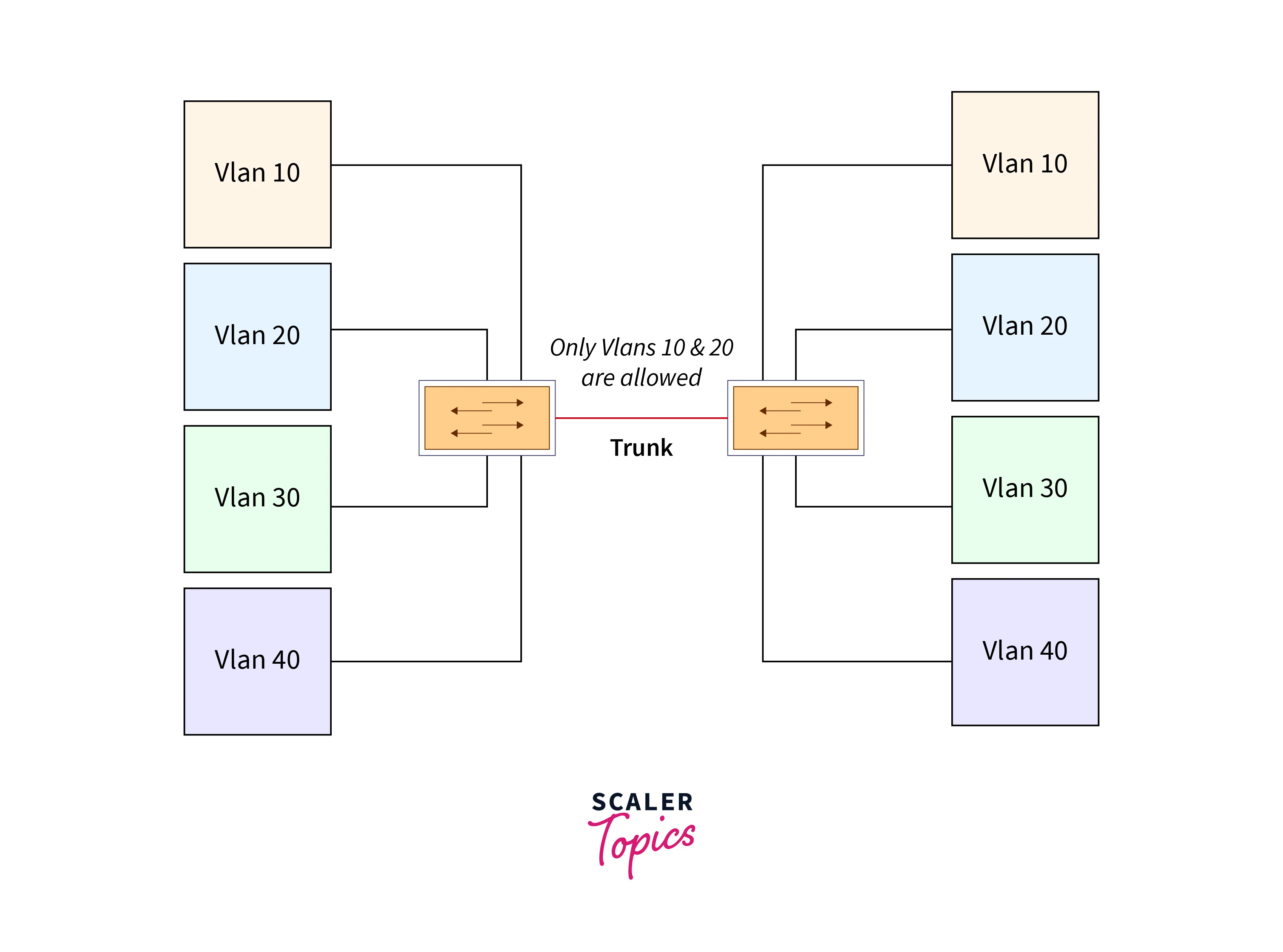
We only want to allow 10 and 20 VLAN. Let us set up the trunk link on SW1 and SW2. We just need to consider one case because both switches have the same configuration.
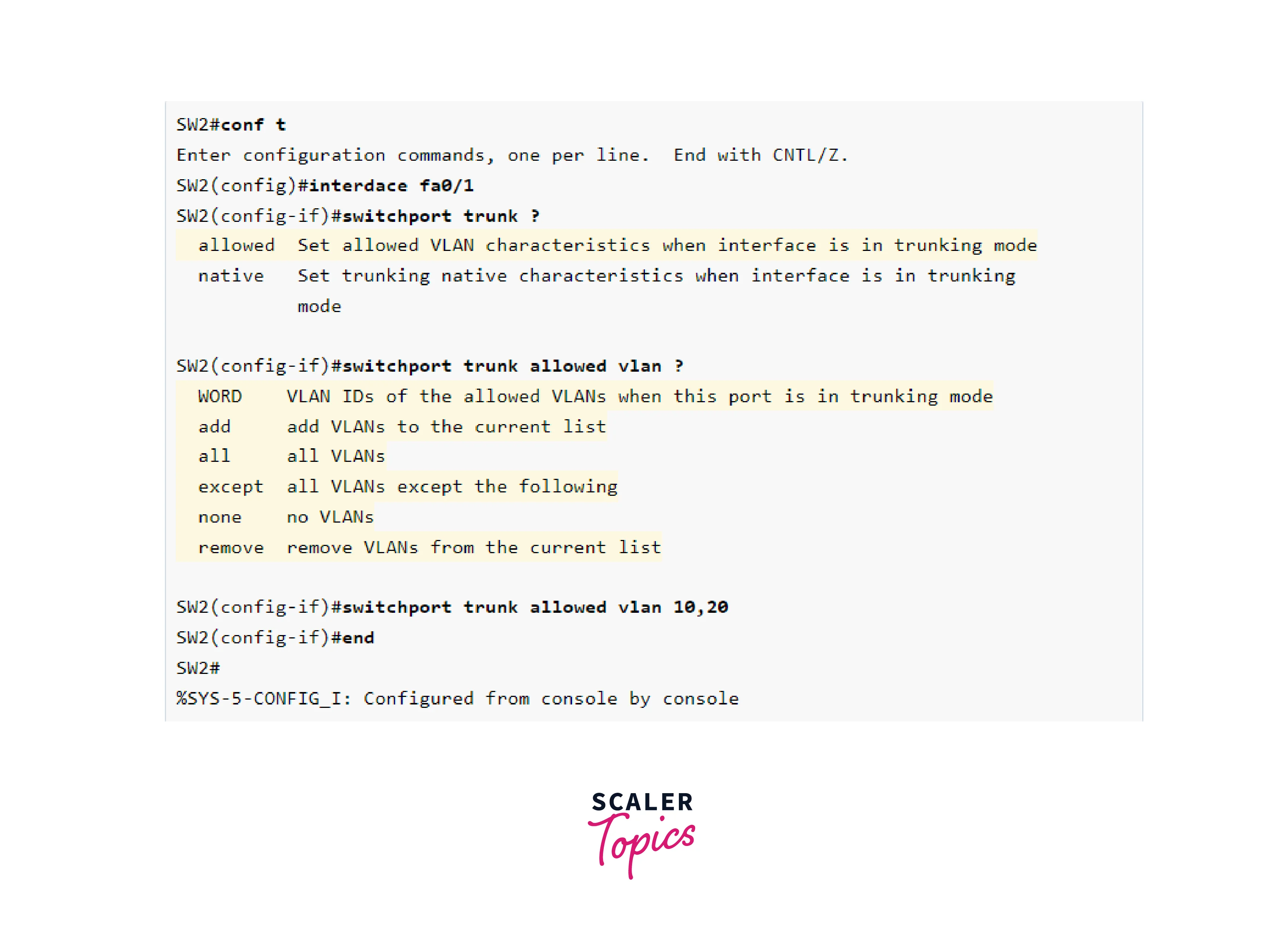
The identical configuration is used on both switches. Now let’s have a look at the trunk ports.
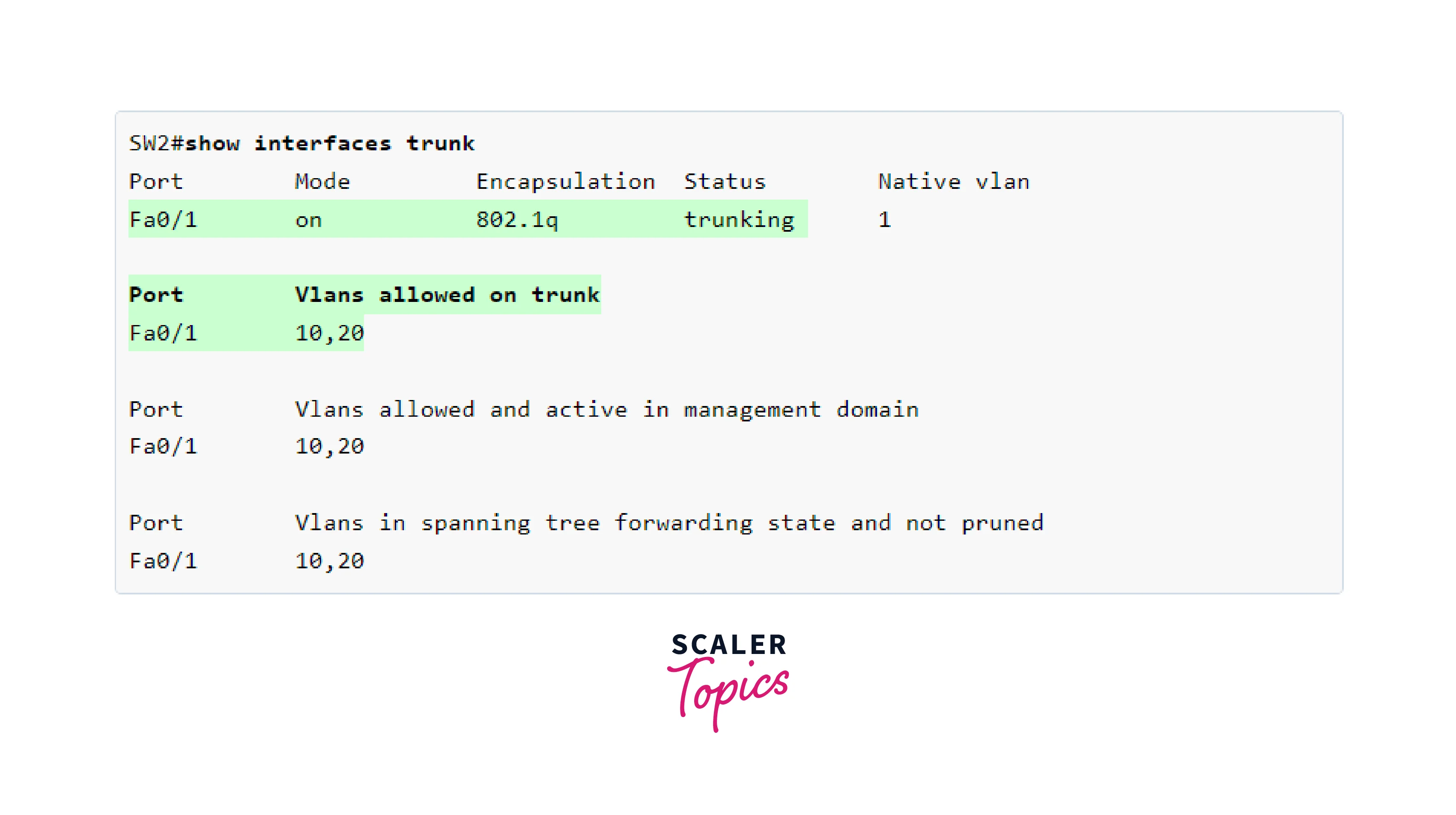
This function is commonly used when connecting a switch owned by one organization to an external switch owned by another organization. Typically, an arrangement is in place to allow data to be exchanged within a given VLAN. As a result, the goal is to exclude all other VLANs, filtering out unnecessary traffic.
Conclusion
- Untagged ports/Access Ports link individual end devices such as PCs, servers, or printers, to a designated VLAN. The data sent through an untagged port does not have a VLAN ID attached to it.
- Trunk ports/tagged ports connect switches and transport data for multiple VLANs over a single link. Data sent over a trunk port is labeled with a VLAN ID, allowing switches to determine the appropriate VLAN for the data and route it accordingly.
- Native VLAN refers to VLAN services that have been designed with backward compatibility in order to accommodate older devices that do not support VLANs.
- Native VLAN does not have a network tag, therefore older devices can simply recognize when trunk lines are sent.
